16 – 22 September 2024
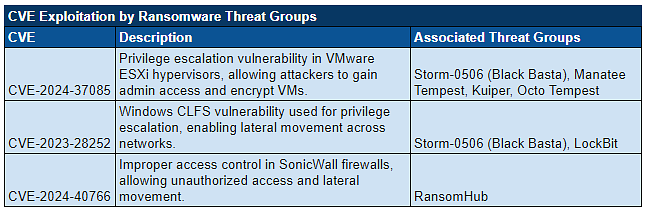
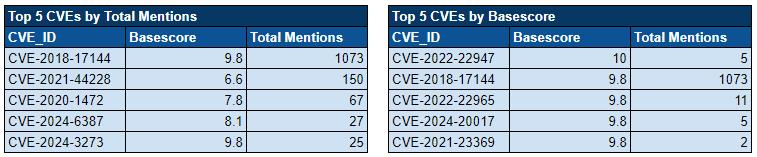
CVE Discussion and Exploitation
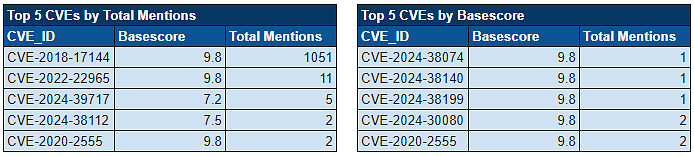
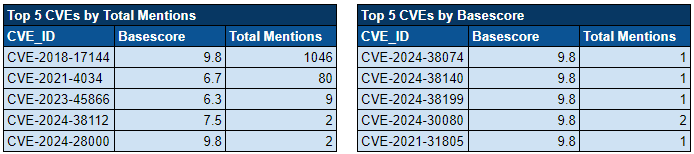
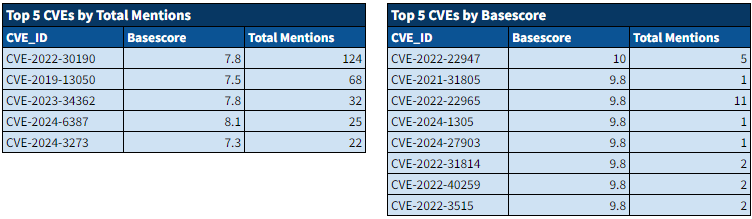
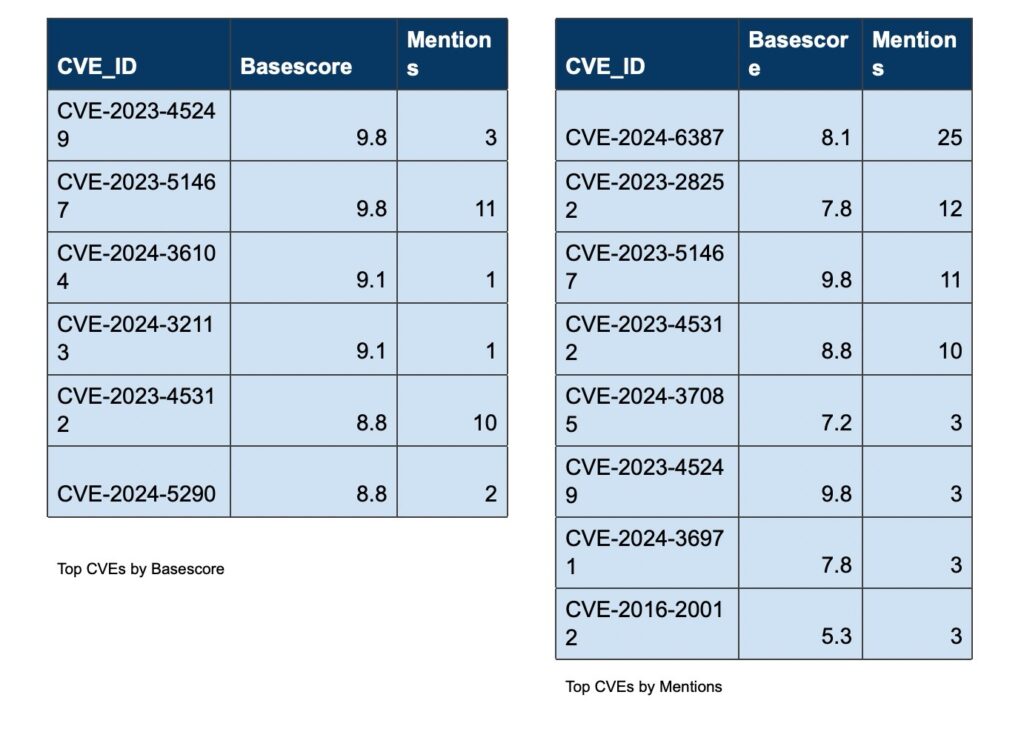
Over the past week, we’ve monitored our vast collection of new data to identify discussions of CVEs.
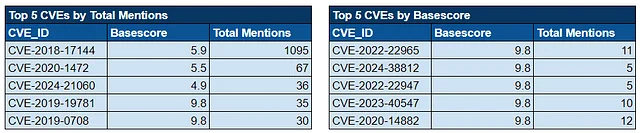
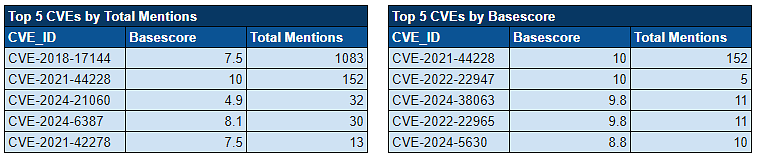
Noteworthy Exploitation of New CVEs by Threat Actors:
- CVE-2024-43461 (Microsoft Windows MSHTML Platform Spoofing)
Exploited by the Void Banshee APT group, this vulnerability allowed them to spoof the MSHTML component in Windows, tricking users into opening files that appeared to be PDFs but were actually harmful HTA files. This exploit was used in a campaign to deploy the Atlantida infostealer, which targets sensitive information like passwords and cryptocurrency wallets - CVE-2024-43491 (Microsoft Windows Update Remote Code Execution)
This flaw in Windows Update was actively exploited by UNC2452, also known as Nobelium, the group behind the SolarWinds attack. The group used this vulnerability to rollback patched security updates, targeting legacy systems to gain access to compromised environments - CVE-2024-29847 (Ivanti Endpoint Manager Remote Code Execution)
This critical vulnerability (CVSS 10.0) was leveraged by FIN11, a financially motivated group known for ransomware campaigns. By exploiting this unauthenticated RCE flaw, attackers gained complete control over enterprise networks, deploying ransomware in corporate and government systems - CVE-2024-38217 (Windows Mark of the Web Security Feature Bypass)
Exploited by APT29 (also known as Cozy Bear), this vulnerability allowed attackers to bypass security measures by tricking users into opening specially crafted files. This vulnerability was part of a broader campaign targeting government entities
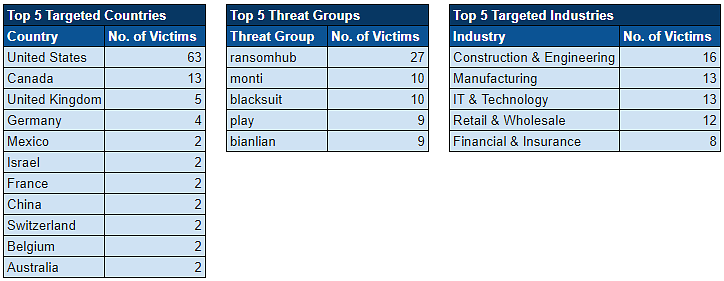
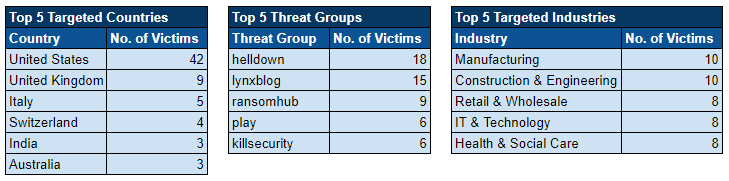
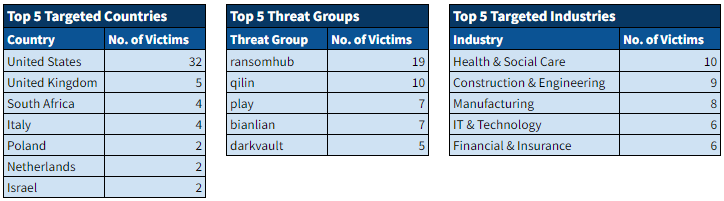
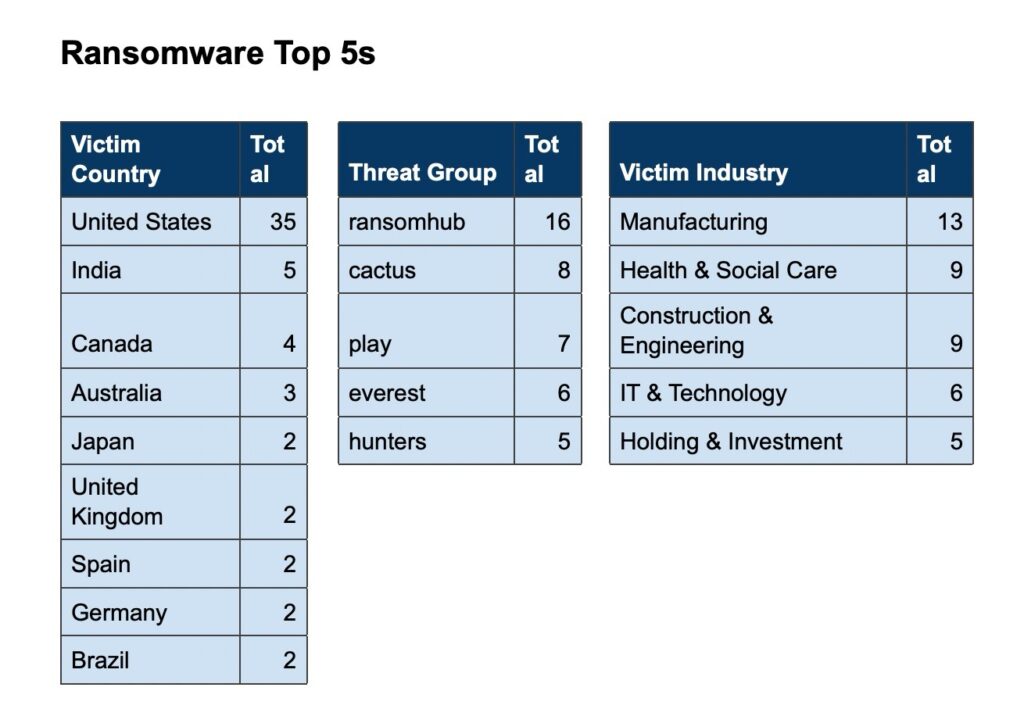
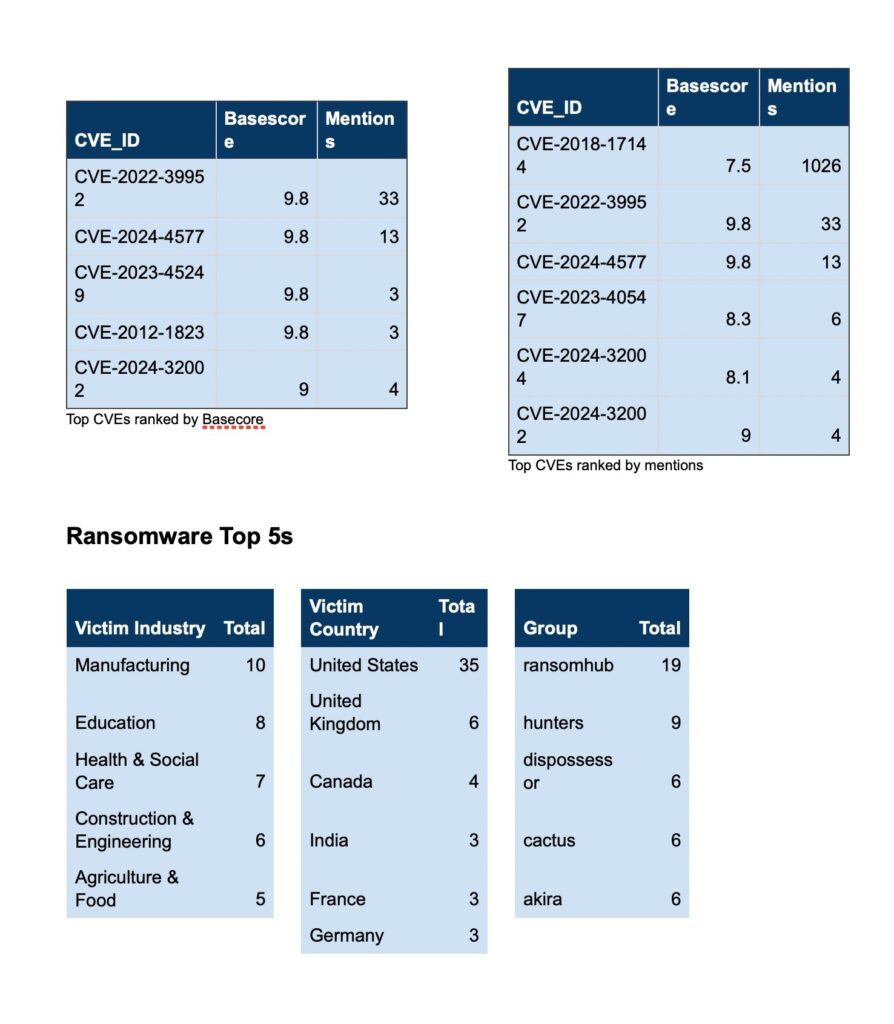
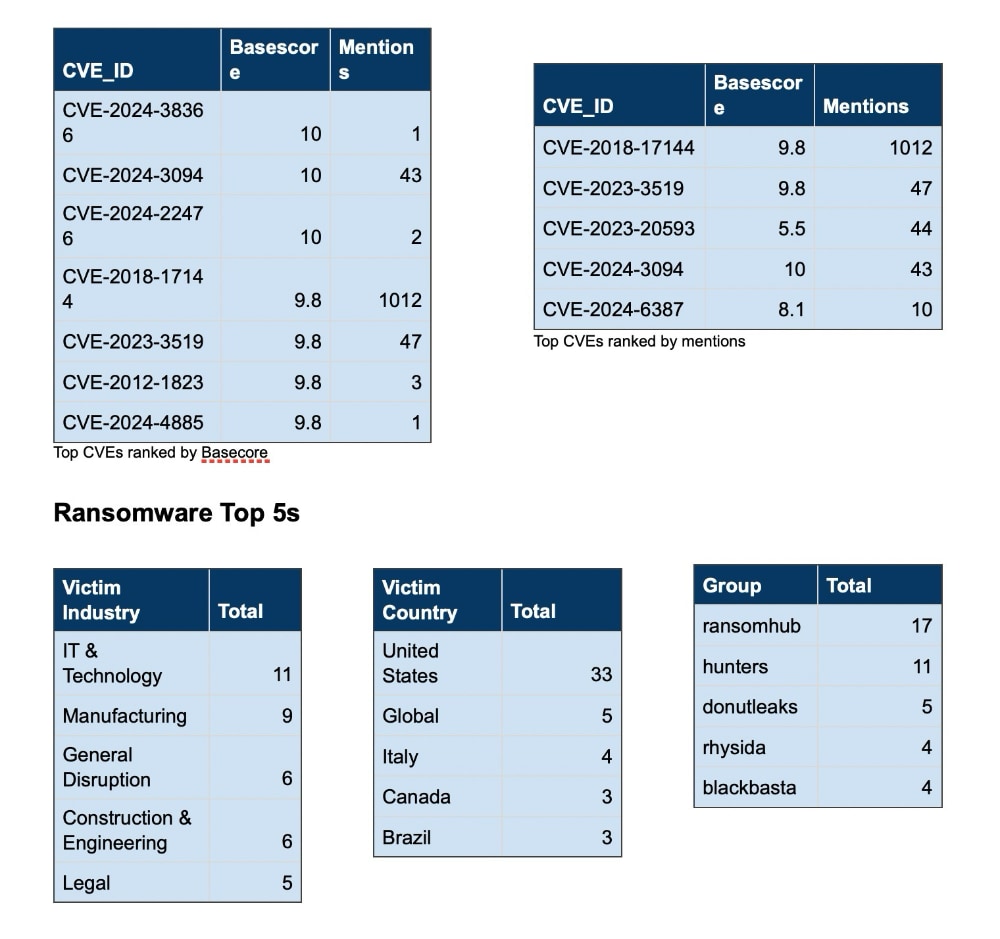
Ransomware Activity
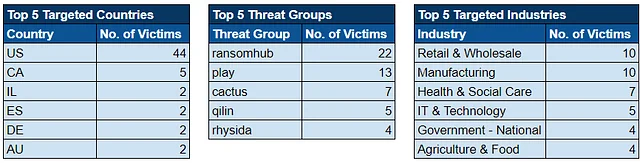
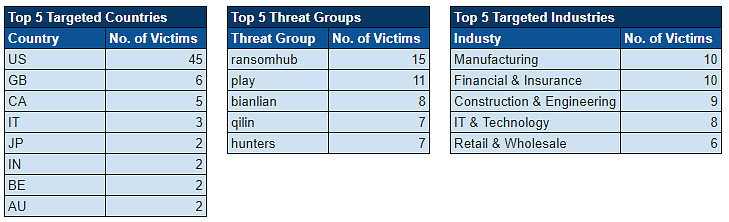
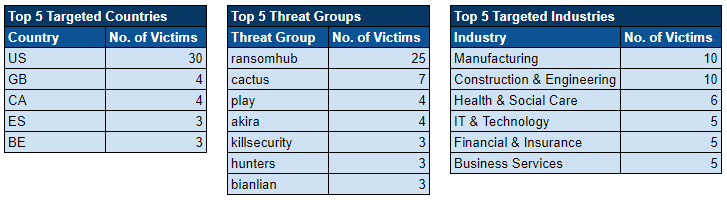
Over the past week, we’ve captured 73 ransomware incidents, affecting victims in 22 countries across 16 industries.
Ransomware Top 5s
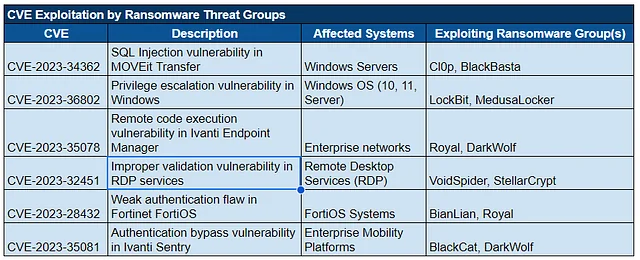
Advancements in Ransomware Tactics:
- Ransomware groups are evolving their techniques by shifting away from traditional malware use. Instead, attackers now focus on exploiting known vulnerabilities in publicly accessible applications. Many of these attacks rely on legitimate software tools, such as PowerShell and Windows Management Instrumentation (WMI), as part of a “living off the land” strategy. This allows them to avoid detection by using tools already present in the target’s environment. Moreover, encryption-free attacks are becoming more prevalent, where attackers steal data to extort companies without encrypting files, simplifying their operations and reducing the chance of detection. Another notable trend is the continued targeting of newly patched systems, where attackers exploit vulnerabilities soon after patches are released
Emerging Threat Actors:
- DarkWolf: A new ransomware group identified, targeting sectors in finance and healthcare across Europe. Early analysis suggests they have adopted similar strategies to BlackCat with a focus on data exfiltration and precise targeting of vulnerable networks.
- StellarCrypt: This group has been observed leveraging a combination of phishing and social engineering to breach systems. Active primarily in the education sector, their operational maturity appears to be increasing, showing signs of evolving into a more structured threat.
- VoidSpider: A splinter group of LockBit affiliates has emerged, conducting high-speed encryption attacks with modified tools. Their attacks appear opportunistic but have shown strong preference for remote desktop protocol (RDP) vulnerabilities.
Key Ransomware Incidents:
- German authorities have seized 47 cryptocurrency exchange services that facilitated illegal money laundering for cybercriminals, including ransomware gangs. These platforms allowed users to exchange cryptocurrencies anonymously by bypassing “Know Your Customer” regulations, creating a safe environment for laundering criminal proceeds. The Federal Criminal Police Office (BKA) highlighted that such services are crucial to cybercrime operations, aiding groups like ransomware operators and darknet dealers. Following the operation, titled “Final Exchange,” visitors to the seized sites are redirected to a warning page revealing that the authorities now possess their transaction and user data. Although no arrests have yet been made, future investigations are expected to lead to the prosecution of cybercriminals, while the operators of the exchanges face charges under German law that could result in lengthy prison sentences.
- Microsoft has reported that the ransomware group Vanilla Tempest, previously known as Vice Society, is now targeting U.S. healthcare organizations with INC ransomware attacks. Active since 2021, Vanilla Tempest has previously attacked sectors like education and IT, using various ransomware strains. Their recent attack on the U.S. healthcare sector involved gaining access via the Gootloader malware, then deploying INC ransomware across the victim’s network. This follows a similar ransomware attack on Michigan’s McLaren Health Care, which disrupted IT systems and patient databases. In May 2024, INC ransomware’s source code was advertised for sale on hacking forums, increasing concerns about its spread.
- Ransomware groups like BianLian and Rhysida are increasingly using Microsoft’s Azure Storage Explorer and AzCopy tools to exfiltrate data from compromised networks and store it in Azure Blob storage. These tools, designed for managing and transferring large-scale data in Azure, allow cybercriminals to upload stolen data to the cloud, which they can later transfer to their own storage. Azure’s trusted enterprise status and scalability make it less likely to be blocked by corporate firewalls, enabling smoother data theft. Researchers from modePUSH observed attackers using multiple instances of Storage Explorer to speed up the process, with log files providing crucial evidence for incident responders. Security measures to mitigate such attacks include monitoring for AzCopy execution, unusual network traffic to Azure endpoints, and enforcing logout protocols to prevent active session misuse.
News Roundup
Microsoft Patches 79 Vulnerabilities, Including Four Zero-Days
In its September 2024 “Patch Tuesday,” Microsoft addressed 79 vulnerabilities, four of which were zero-day flaws under active exploitation. Notable among them is CVE-2024-38226, impacting Microsoft Publisher, allowing attackers to bypass macro security in untrusted files. Another critical vulnerability, CVE-2024-43491, targets Microsoft Windows Update, posing a remote code execution risk by exploiting previously mitigated vulnerabilities in Windows 10. These patches are crucial as they cover a wide range of issues, including privilege escalation (CVE-2024-38014) and bypassing the “Mark of the Web” protection (CVE-2024-38217)
While Microsoft continues its efforts to secure its software, these zero-day vulnerabilities underscore the persistent threat to enterprises. Security experts emphasize that timely application of these patches is critical to prevent exploitation by cybercriminals. This update also highlights the increasing sophistication of attackers, particularly in targeting essential business tools like Microsoft Office and Windows systems, putting sensitive data at risk
PIXHELL: Data Exfiltration via LCD Screens
A new attack method named PIXHELL has been discovered, demonstrating how data can be stolen from air-gapped systems via LCD monitors. Researchers at Ben-Gurion University of the Negev devised a technique where malware modulates pixel patterns on LCD screens, generating sound frequencies that can be captured by nearby devices, such as smartphones. Though the data transfer rate is low at 20 bits per second, it poses a risk for exfiltrating sensitive information like passwords
PIXHELL is part of a growing trend of side-channel attacks targeting systems that are isolated from external networks. Security experts advise that critical environments, particularly those handling highly sensitive data, implement strict access controls, including banning devices with microphones and introducing background noise to neutralize potential attacks
Commercial Spyware Evades Global Sanctions
Commercial spyware, such as Pegasus and Predator, continues to be a pressing issue despite international sanctions. These tools are reportedly evolving to be harder to detect, enabling authoritarian regimes to deploy them against journalists and activists. Developers are circumventing regulations by renaming their companies and altering spyware to obscure the countries using them. Governments and civil society groups are increasingly calling for stricter oversight of the spyware industry, as these tools enable cyber-espionage on a global scale
Avis Car Rental Cyberattack Affects 299,000 Customers
Avis, a major car rental service, disclosed a cyberattack in August 2024 that led to the theft of sensitive information from 299,006 customers. The stolen data includes names, contact details, credit card numbers, and driver’s license information. Avis has begun notifying affected individuals and is offering free credit monitoring for a year. The full scale of the attack is still under investigation, and there is potential for the number of affected customers to increase as more details emerge
MC2 Data Leak Exposes Over 100 Million U.S. Citizens
A massive data breach involving MC2 Data, a background check service, exposed the personal records of over 100 million U.S. citizens. The unprotected database, discovered in September 2024, included names, Social Security numbers, and other personal details. This breach highlights the ongoing vulnerability of personal data held by third-party services, raising concerns about inadequate cybersecurity practices in sectors that handle sensitive information.











Recent Comments