26 August – 01 September 2024
Over the past week, we’ve monitored our vast collection of new data to identify discussions of CVEs.
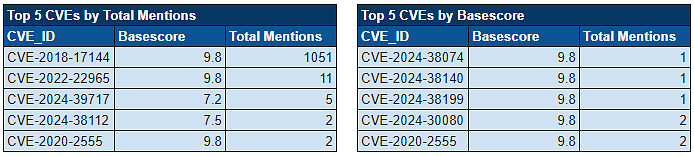
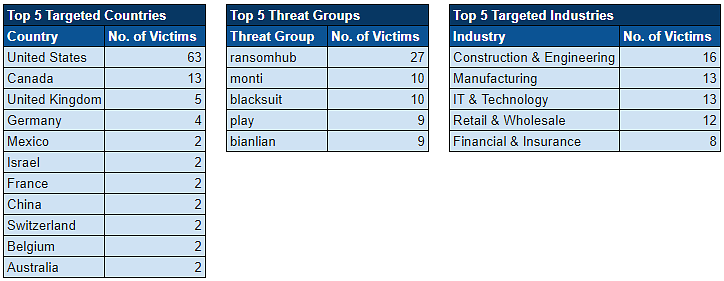
Ransomware Top 5s
News Roundup
Iran State-Sponsored Hackers Using Fake Job Offers
Mandiant recently uncovered a sophisticated cyber espionage campaign led by Iranian state-sponsored hackers, targeting potential recruits from foreign intelligence services, particularly in Israel. Running from 2017 until March 2024, the operation involved over 35 fake recruitment websites in Farsi, designed to attract individuals with expertise in cybersecurity and intelligence.
These sites systematically collected personal, professional, and educational information, aiming to identify and recruit individuals for human intelligence (HUMINT) purposes. The campaign, associated with APT42, an Iranian group linked to the IRGC, also extended its focus to Arabic-speaking intelligence communities in Syria and Lebanon.
The fake websites, which mimicked legitimate HR agencies, used social engineering tactics to lure targets by presenting job opportunities related to Israel. The sites featured Israeli-related imagery and branding, with links disseminated via social media platforms like Twitter and Telegram. Mandiant’s investigation also revealed connections to Iranian software developers and exposed the use of command and control structures within the fraudulent recruitment platforms.
This campaign highlights Iran’s ongoing efforts to bolster its intelligence capabilities by targeting skilled individuals, using deceptive online methods to gather critical information.
Repeated Use of iOS and Chrome Exploits by State-Sponsored Hackers
Google’s Threat Analysis Group (TAG) has uncovered multiple sophisticated cyber campaigns targeting Mongolian government websites between November 2023 and July 2024. These campaigns involved watering hole attacks, where the compromised websites, such as cabinet.gov.mn and mfa.gov.mn, delivered malicious payloads to unsuspecting visitors. Initially, the attacks focused on iOS devices by exploiting a WebKit vulnerability in versions older than 16.6.1, before shifting to Android users with a Chrome exploit chain targeting versions m121 to m123.
Despite available patches, these n-day vulnerabilities remained unaddressed on some devices, leaving them exposed to these attacks.
TAG attributes these campaigns to APT29, a Russian government-backed group, known for using tactics similar to those employed by commercial surveillance vendors like Intellexa and NSO Group. The attacks primarily aimed to steal authentication cookies from targeted websites, using advanced techniques such as creating websockets linked to attacker-controlled IPs and bypassing Chrome’s Site Isolation feature.
Google has informed the relevant tech companies and the Mongolian CERT about the breaches, adding the malicious domains to Safe Browsing to protect users. This incident underscores the ongoing threat of watering hole attacks and highlights the critical need for timely application of security patches to defend against such exploits.
RansomHub Exploiting RDP Services for Large-Scale Data Exfiltration
RansomHub, a Ransomware-as-a-Service (RaaS) group, has been exploiting Remote Desktop Protocol (RDP) services to exfiltrate significant volumes of data from targeted organisations. Operating with a double extortion model, RansomHub encrypts files and steals sensitive data, primarily targeting entities in the United States, United Kingdom, Spain, France, and Italy, with a focus on sectors such as healthcare, finance, and government.
Despite not being highly advanced, the group effectively uses dual-use tools for network propagation and command-and-control through remote monitoring and management, demanding substantial ransoms—reportedly up to $50 million in some cases.
RansomHub’s operations began in February 2024, emerging on the dark web forum ‘RAMP’ under the alias “Koley.” They offer affiliates a 90-10 profit share and utilise a sophisticated ransomware written in Golang, capable of running on Windows, Linux, and ESXi systems. The group’s attack strategy often involves compromising domain admin accounts via tools like LummaC2, followed by network discovery and lateral movement using tools such as Netscan and PsExec. Before encrypting files, data is typically exfiltrated to cloud storage services like Mega.
Researchers have urged organisations to enhance their security measures, particularly around access controls and incident response, to mitigate the risks posed by such sophisticated RaaS operations.
Hackers Exploit GitHub to Spread Lumma Stealer Malware
Cybersecurity analysts at Gen Digital have uncovered a concerning trend where threat actors are using GitHub to distribute the Lumma Stealer, a sophisticated information-stealing malware. Lumma is designed to exfiltrate sensitive data such as login credentials, financial information, and cryptocurrency wallets from compromised systems. As a Malware-as-a-Service (MaaS) tool, it is actively promoted through GitHub repositories, making it accessible to a wide range of cybercriminals.
Lumma Stealer’s developers are employing new tactics, such as abusing session cookies during Google account logins, and continuously updating comments on GitHub to include links to malicious files hosted on platforms like Mediafire. These comments, often difficult to remove in time, lead to encrypted archives containing the malware.
Cybercriminals are also using platforms like YouTube and Dropbox to distribute Lumma Stealer under the guise of fake tutorials or cracked software, targeting users seeking free alternatives. The increasing sophistication of these attacks, including the potential use of generative AI for crafting convincing messages, poses a significant challenge for cybersecurity efforts.
Critical Dell BIOS Flaw Could Allow Hackers to Execute Arbitrary Code
A critical vulnerability, identified as CVE-2024-39584, has been discovered in the Dell Client Platform BIOS, posing a significant security risk to affected systems. This flaw, classified as a “Use of Default Cryptographic Key” vulnerability, has a CVSS base score of 8.2, reflecting its high potential impact. If exploited, a high-privileged attacker with local access could bypass Secure Boot and execute arbitrary code, leading to a complete system compromise, affecting the system’s confidentiality, integrity, and availability.
Dell has responded by releasing BIOS updates for several affected products, including various Alienware models. Users are strongly urged to update their BIOS to the remediated versions, released on August 27 and 28, 2024, to protect against potential exploitation.
No alternative workarounds are currently available, making these updates crucial for maintaining system security. Dell has credited the BINARLY Research team for identifying this vulnerability and advises users to regularly check for and apply security patches to safeguard their systems.
Photo by Arman Taherian on Unsplash

