5 – 11 August 2024
CVE Discussion
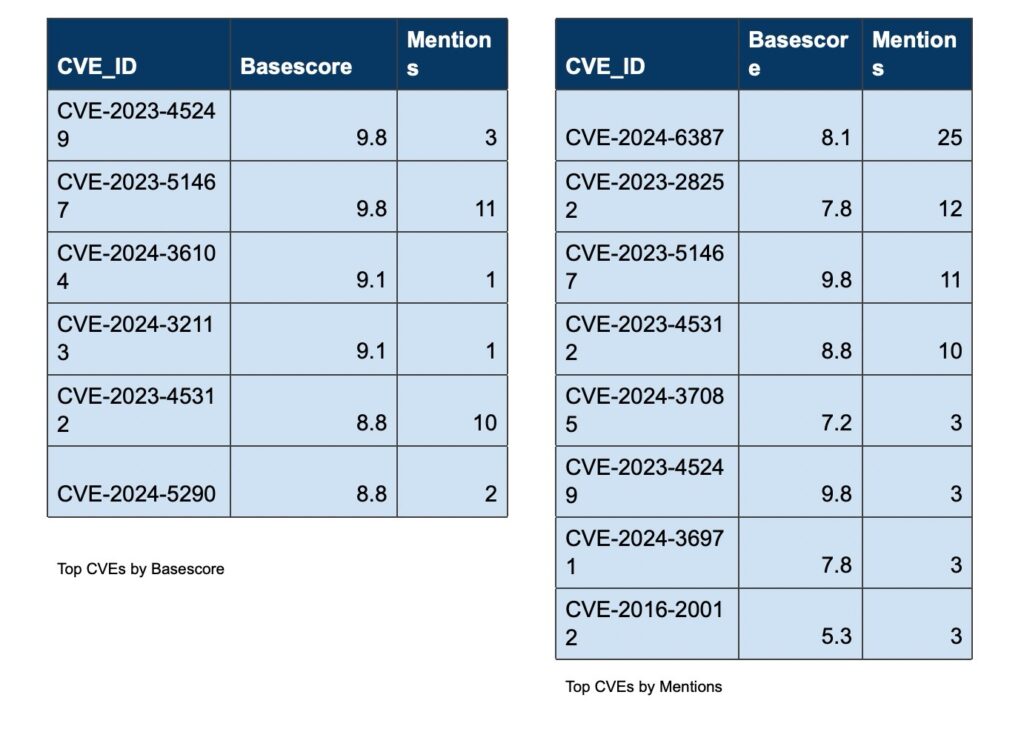
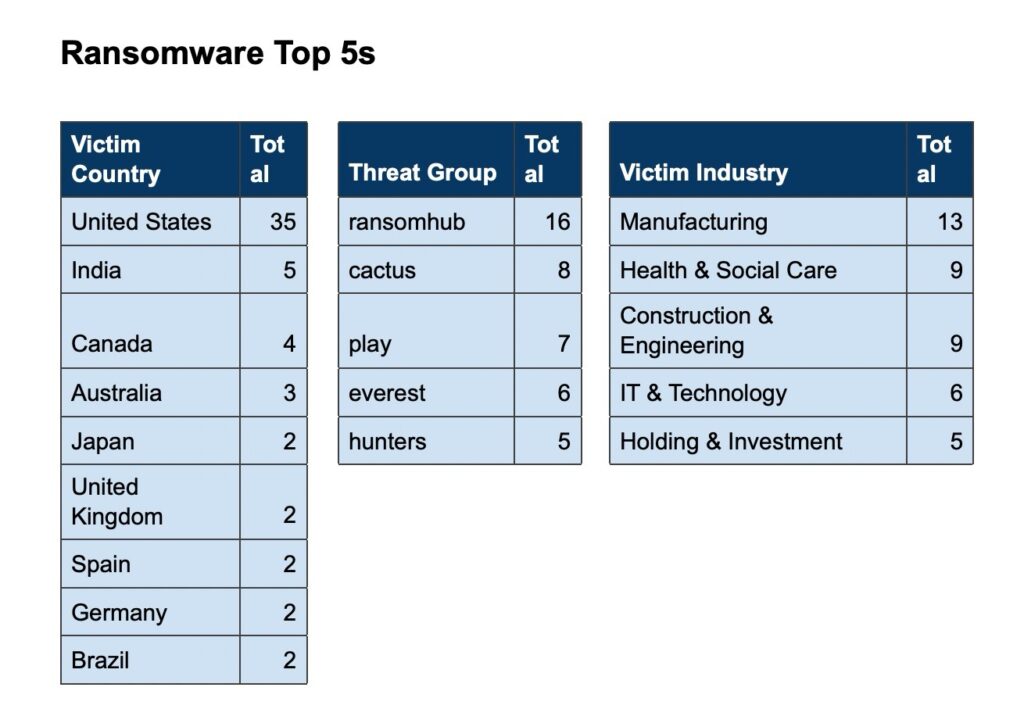
Over the past week, we’ve monitored our vast collection of new data to identify discussions of CVEs.
News Roundup
Critical Vulnerabilities Found in OpenVPN
Microsoft researchers have identified several medium-severity vulnerabilities in OpenVPN, a widely used open-source VPN software across various industries, including IT, finance, and telecommunications. These vulnerabilities, present in versions before OpenVPN 2.6.10 and 2.5.10, can be exploited to achieve remote code execution (RCE) and local privilege escalation (LPE). This could allow attackers to gain full control over targeted devices, leading to potential data breaches, system compromises, and unauthorised access to sensitive information.
The vulnerabilities are specifically found in OpenVPN’s client-side architecture, involving the communication between the openvpn.exe process and the openvpnserv.exe service on Windows systems. Key vulnerabilities include:
- CVE-2024-27459, a stack overflow vulnerability causing denial-of-service (DoS) and LPE;
- CVE-2024-24974, an unauthorised access vulnerability;
- CVE-2024-27903, a flaw in the plugin mechanism allowing RCE and LPE;
- CVE-2024-1305, a memory overflow vulnerability in the Windows TAP driver causing DoS.
These vulnerabilities require user authentication and a deep understanding of OpenVPN’s operations to be exploited, potentially allowing attackers to chain them together for more sophisticated attacks.
In response, Microsoft reported these issues to OpenVPN in March 2024, leading to the release of patches in versions 2.6.10 and 2.5.10. OpenVPN users are strongly advised to apply updates to mitigate the risks. Additionally, users should implement security measures such as segregating OpenVPN clients from unauthorised users, enforcing strong authentication, limiting user access, and monitoring for unusual activity.
Record-braking DDoS Attack
Akamai Technologies successfully mitigated one of its most extensive and sophisticated distributed denial-of-service (DDoS) attacks, which targeted a major financial services company in Israel. The attack, lasting nearly 24 hours from July 15, involved a globally distributed botnet that simultaneously targeted over 278 IP addresses using multiple methods, including UDP flood, DNS reflection, and PSH+ACK. During the peak of the attack, traffic ranged between 300 and 798 Gbps, with Akamai blocking approximately 419 terabytes of malicious traffic. This attack ranks as the sixth-largest DDoS peak traffic ever mitigated by Akamai Prolexic and underscores the growing trend of high-volume, sustained DDoS threats in the EMEA region.
The attack’s sophistication and intensity suggest a potentially state-backed threat actor, particularly given the geopolitical context and focus on Israel’s financial sector. The targeted institution had recently adopted Akamai’s Prolexic platform, which played a critical role in neutralising the threat, emphasising the need for robust, cloud-based DDoS protection solutions. Akamai cautions that organisations relying solely on on-premises mitigation or shared hosting provider defences may be vulnerable to such large-scale attacks. As DDoS threats continue to evolve, businesses must reassess their defences and invest in advanced, scalable security measures to safeguard against increasingly sophisticated attacks.
Kibana Vulnerability Leading to Remote Code Execution
Kibana, a widely used open-source data visualisation tool, has identified a critical security flaw, tracked as CVE-2024-37287, that could allow attackers to execute arbitrary code. This vulnerability has a CVSSv3 severity rating of 9.9, highlighting its critical nature. The flaw arises from a prototype pollution vulnerability, which can be exploited by attackers with access to Machine Learning (ML) and Alerting connector features, as well as write access to internal ML indices, posing significant security risks.
The vulnerability affects various Kibana environments, including self-managed installations, Kibana instances running on Docker, Elastic Cloud, Elastic Cloud Enterprise (ECE), and Elastic Cloud on Kubernetes (ECK). In all these environments, the Remote Code Execution (RCE) is confined within the Docker container, with additional protections provided by seccomp-bpf and AppArmor profiles to prevent further exploitation, such as container escape. However, the flaw remains critical, and immediate action is necessary to mitigate the risk.
To address this vulnerability, users are strongly advised to upgrade to Kibana versions 8.14.2 or 7.17.23, which include the necessary patches. This situation underscores the importance of timely software updates and robust security practices to protect systems from potential exploitation. Organisations using Kibana should prioritise upgrading to the latest versions and refer to official Kibana documentation and security advisories for detailed guidance.
Emerging Ransomware Variant Discovered Targeting Linux Machines
Symantec researchers have discovered a new Linux ransomware variant associated with a bilingual double-extortion ransomware group. This variant poses a significant threat by not only encrypting sensitive data but also exfiltrating it, allowing cybercriminals to demand ransom payments for both decryption and the protection of the stolen data. This double-extortion tactic greatly increases the potential damage to organisations, as the attackers gain additional leverage by threatening to leak the stolen information, making the attacks particularly dangerous across all industries.
The ransomware operates by depositing ransom notes in critical system directories and forcibly halting essential processes like PostgreSQL, MongoDB, MySQL, Apache2, Nginx, and PHP-FPM to ensure the attack’s success. The ransom note, written in both English and Spanish, warns victims that their files have been encrypted and exfiltrated, with decryption possible only through the attackers’ software. It further threatens to leak company data, including employee emails and customer databases, unless the victim contacts the attackers via the privacy-focused messaging app, ‘Session.’ Symantec has categorised this threat under Ransom.Gen and advises organisations to deploy comprehensive security solutions, maintain regular backups, train employees on cybersecurity awareness, and segment networks to mitigate the impact of such attacks.
New AMOS Mac Stealer Targets Apple Users via Fake Apps
A new variant of the AMOS Mac stealer is being distributed via a fake Loom website hosted on Google Ads, potentially linked to the Crazy Evil threat group. This advanced malware targets Apple users by masquerading as trusted applications like Ledger Live, Figma, and TunnelBlick, allowing it to steal sensitive data such as browser information, credentials, cryptocurrency, NFTs, and DeFi assets. The malware’s ability to clone legitimate apps and bypass Apple’s App Store security poses a significant threat, particularly to users relying on these platforms.
Cybercriminals are increasingly targeting gamers, especially younger individuals, by using social engineering tactics like fraudulent job postings or fake rewards on gaming platforms. A recent discovery of a .dmg file linked to the popular MMORPG Black Desert Online highlights this trend, with the Crazy Evil group distributing a modified AMOS stealer capable of targeting macOS Ledger wallets. The group, linked to a recent campaign via darknet analysis, remains largely anonymous but may have ties to a Russian government-associated network.
The investigation into this campaign uncovered an IP address with strong malware ties, flagged by VirusTotal as malicious and linked to the Russian ISP Gesnet.ru, raising concerns about network-wide compromise. To protect against such threats, users are advised to exercise caution when downloading software, adhere strictly to official app stores, and remain vigilant, especially within online gaming communities. Continuous awareness and proactive security measures are crucial to safeguarding against the evolving threat of AMOS malware.

