Simply put, we care about your success and we are not so big that you are treated as a number.

OUR COMMITMENT TO YOU
“The project that eventually became what SOS Intelligence is now was born out of a need for real time breach alerting and a lack of affordable service providers.
This lead to the internal development of a series of bespoke programs to perform automatic collection and keyword search matching against a number of different open source threat intelligence sources.
We now have a wealth of clients across most sectors, from small businesses to global corporations. We aim to reduce your business risk through cyber insight and relevant intelligence.
SOS Intelligence has been a labout of love and a lot of work over the past few years – it really can make a difference to your risk. Don’t hesitate to book a demo.”
Amir
Business leaders across all sectors are under constant pressure to evolve their risk and resilience programs to react to changing operational risks. Since partnering with SOS Intelligence, we’ve taken our digital risk monitoring to a new level.
As a large business with customers across the globe, and a digital footprint that spans thousands of touchpoints, identifying and managing risk can be time-consuming and costly. SOS Intelligence’s solution provides real-time alerts, easy to read dashboards and actionable threat intelligence, for us and our customers, this is a game changer’’
Head of Cybersecurity Consultancy Services at JT Group

Some of the companies who already trust us











We are a small team who personally know our customers and support them. You won’t just be a number.
Your satisfaction is absolutely key and we are here to help and advise.
We regularly run webinars and you can sign up and attend or watch on demand.
Social engineering is the term used for a broad range of malicious activities accomplished through human interactions (often things you think are completely normal). It uses devious manipulation to trick us into making security mistakes or giving away critical, sensitive information. Watch this essential webinar now to get the lowdown and understand what you need to do…
Listen to our founder and CEO, Amir talk about what we’ve achived over the past 12 months, the deep commitment to listening to customer needs and how our development is driven by this. Also we have some previews of what’s coming soon!
How to turn open-source intelligence into actionable cybersecurity insights.For our second webinar of 2025 we are going to be discussing the using OSINT and CTI for Threat Detection.
Open source intelligence (OSINT) is the collection and analysis of data gathered from open sources (overt sources and publicly available information) to produce actionable intelligence. In this webinar, we will discuss what are the key things you need to know and understand about this incredibly important aspect of cyber security.
Phishing, smishing, and quishing are all forms of cyber fraud aimed at deceiving individuals into revealing sensitive information. More and more common, it is not going away sadly. Watch the webinar to learn how it is done and what you need to look out for…
Steganography, the practice of hiding information, has been around for hundreds of years. However, it has now been associated with some forms of cyber attacks. In this webinar, we will exploring what you need to do about steganography in relation to cyber security.
In the digital age, data has emerged as one of the most valuable resources, driving economies, shaping public opinion, and determining the success of nations.
Amid this reality, cybercrime has become a potent tool for state actors, with China often cited as a significant player in the realm of cyber espionage and cybercrime. Watch this fascinating discussion about China and how China has allegedly used cybercrime to obtain data, the motivations behind these actions, their methods, and the implications on global geopolitics.
Learn the SIX major things that motivate cyber crime and how it plays a part with the choosing of a victim + the NINE things the cyber crime gangs then do once the victim is chosen.
Understanding how threat actors gain access is essential. In this webinar we will go through what you need to know and answer questions you may have.

Third party cybersecurity risk is a very hot topic right now and simply put, must be managed. SOS Intelligence aims to make you less vulnerable and put you one step ahead of the threat actors.

If you want to find out cyber threat hunting, what you can do and how SOS Intelligence can help, then please join us for this 20 minute webinar.
Cyber threat hunting is a proactive cyber defence activity. It is “the process of proactively and iteratively searching through networks to detect and isolate advanced threats that evade existing security solutions.” Source Wikipedia

We have recently seen some very high-profile attacks on major companies, including British Airways, Boots and the BBC. It is a sad fact that ransomware can rear its ugly head at any time.
SOS Intelligence aims to make you less vulnerable and put you one step ahead of the threat actors.
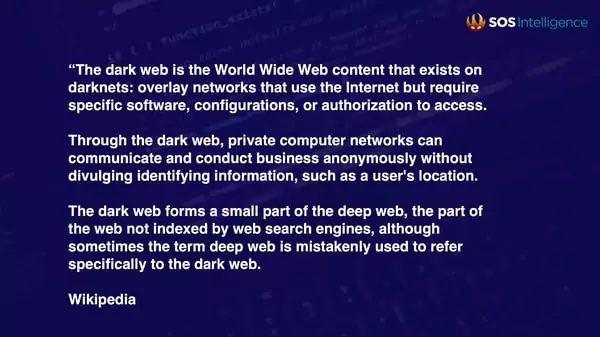
As the global need for digital interconnectivity has grown and expanded, so too has the need to communicate and share data privately.
The expansion of the “clear web” has therefore been accompanied by a growth in “dark web” services and protocols. But what is the dark web, and where has it come from?

“Without dedicated action, the global financial system will only become more vulnerable as innovation, competition, and the pandemic further fuel the digital revolution.”
We aim to make you less vulnerable and put you one step ahead of the threat actors.

If you want to find out why and how SOS Intelligence is an essential tool for legal firms, then this is for you.
Free real time breach alerting and retrospective check against our breach database.
We believe we offer the most cost effective way for you to monitor Dar Web Threats. Why not book a demo?
Realtime means you get instant notification when it matters. Be in control of how you get notified. We offer email, Slack, SMS and PagerDuty as well as (plan dependant) API integration with your own ticket system or SIEM”
You get the information you need and nothing you don’t.
We offer a comprehensive API Toolkit allowing for unparalleled integration with other tools through our fully documented API.
Search across the entire darkweb for content that you are interested in with our DARKSEARCH web UI and API toolkit.
An Onion domain relationship map, with frequently updated JSON map package + Web UI Front end.
Extremely useful in our current environment and with the use of cryptocurrency.
Interrogate the darkweb for specific URI paths, open ports and get information about darkweb webserver technology.
With SOS Intelligence we give you contextual awareness. Any event generated will allow you to view the source data of the document that matched your monitoring keyword. This means you have actionable intelligence on a breach alert at your fingertips even when the original source has been taken down or no longer available.
Threat Hunting and Investigation is a breeze with our RESTful API Toolkit and web search interfaces. If for example you are looking to track discussion around a particular vulnerability, malware botnet, ransomware group – just set the keywords you need and we will track anything we find on the Darkweb or OSNIT for you.
Protect your domain names from copy cat domains. We can monitor domain name registrations and deliver a report to your customer portal automatically of any similar looking domains that have been registered in the last 24 hours.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |


