By Daniel Collyer, Threat Intelligence Analyst, SOS Intelligence
This was originally sent out to our Flash Alert Subscribers on July 12th. To sign up for this free service, please click here.
Microsoft is actively investigating CVE-2023-36884, an unpatched zero-day vulnerability in their Windows and Office products, amid concerns it is being utilised by nation-state and cybercriminal threat actors to gain remote code execution (RCE) via malicious Office documents.
The zero-day is exploited via specially crafted Office documents, designed to enable RCE. The victim would be required to open the document for the malicious code to execute. However, it is reported that the vulnerability could be exploited without user interaction.
Successful exploitation of this vulnerability could pose a significant risk to data, granting threat actors access to confidential and sensitive information, allowing them to bypass or shut down system protections, and/or deny access to compromised systems
The exploit has been identified to have been utilised in a campaign by APT Storm-0978 (AKA DEV-0978, RomCom), aimed at European and North American government and defence entities.
Microsoft provided the following mitigations for the unpatched zero-day:
- Customers who use Microsoft Defender for Office are protected from attachments that attempt to exploit this vulnerability.
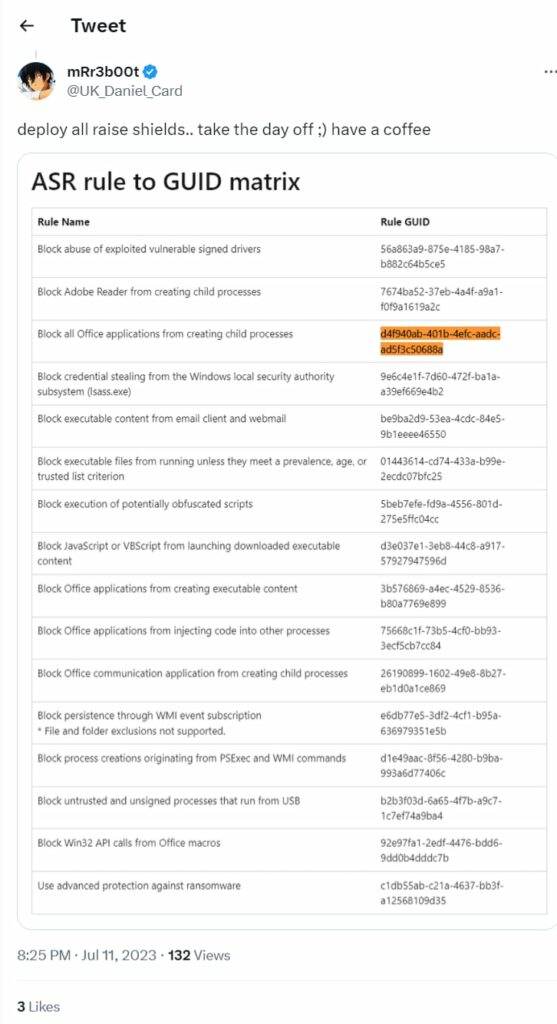
- In current attack chains, the use of the Block all Office applications from creating child processes Attack Surface Reduction Rule will prevent the vulnerability from being exploited.
- Organisations that cannot take advantage of these protections can set the FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION registry key to avoid exploitation. Please note that while these registry settings would mitigate exploitation of this issue, they could affect regular functionality for certain use cases related to these applications. Add the following application names to this registry key as values of type REG_DWORD with data 1.:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION
- Excel.exe
- Graph.exe
- MSAccess.exe
- MSPub.exe
- PowerPoint.exe
- Visio.exe
- WinProj.exe
- WinWord.exe
- Wordpad.exe
The Twitter post below, from @UK_Daniel_Card, provides the GUID references for Attack Service Reduction (ASR) rules which can be utilised to increase protection.