In the digital age, data has emerged as one of the most valuable resources, driving economies, shaping public opinion, and determining the success of nations. Amid this reality, cybercrime has become a potent tool for state actors, with China often cited as a significant player in the realm of cyber espionage and cybercrime. This article delves into how China has allegedly used cybercrime to obtain data, the motivations behind these actions, their methods, and the implications on global geopolitics.
UPDATE – join us on the 13th June for the accompanying webinar.
The Who – Those Working In The Shadows
On the digital battlefield, whether state-sponsored or self-motivated hacker, anonymity is key. This makes the task of attributing the activity of threat actors to real-world identities that much harder. More often than not, we see the evidence of digital crime, and can use available intelligence to make best estimates of a culprit, but a threat actor who wants to remain anonymous can do so with a reasonable application of effort. However, despite these efforts, identification of threat actors and attribution of criminal activity can be possible.
China’s cyber activities are primarily conducted by state-sponsored groups. These groups, often referred to as Advanced Persistent Threats (APTs), include:
APT 1
APT1, also known as the Comment Crew or Shanghai Group, is a highly active cyber espionage unit linked to the Chinese military, specifically PLA Unit 61398. Identified by cybersecurity firm Mandiant in a 2013 report, APT1 is known for targeting a wide array of industries, including information technology, aerospace, telecommunications, and scientific research.
Their primary method of infiltration involves spear-phishing emails, followed by deploying custom and publicly available malware to maintain access and exfiltrate sensitive data. The group’s activities have largely focused on U.S.-based organisations, aiming to steal intellectual property and trade secrets to benefit Chinese companies and government entities.
APT 10
APT10, also known as Stone Panda or MenuPass Group, is a cyber espionage group attributed to the Chinese government. The group has been active since at least 2009 and is known for targeting managed IT service providers (MSPs) and their clients across various industries, including healthcare, aerospace, and manufacturing. APT10’s operations typically involve sophisticated tactics such as spear-phishing, the use of custom malware, and leveraging legitimate credentials to infiltrate networks and exfiltrate data. Their focus on MSPs allows them to gain access to multiple organisations through a single breach, maximising the impact of their espionage efforts.
APT10’s activities have had significant global repercussions, prompting extensive investigations and responses from cybersecurity firms and government agencies. In December 2018, the U.S. Department of Justice indicted two Chinese nationals associated with APT10, accusing them of stealing sensitive data from dozens of companies and government agencies.
APT 31
APT31, also known as Zirconium, Judgment Panda, or Bronze Vinewood, is a Chinese state-sponsored cyber espionage group. The group is known for its advanced and persistent cyber operations targeting a wide range of sectors, including government, finance, technology, and aerospace. APT31 employs sophisticated tactics such as spear-phishing, supply chain attacks, and the deployment of custom malware to infiltrate and maintain access to targeted networks. Their primary goal is to steal sensitive information and intellectual property to support Chinese national interests and provide strategic advantages.
The activities of APT31 have significant global implications, prompting extensive countermeasures from affected organisations and governments. Notably, in 2020, APT31 was linked to cyberattacks targeting the U.S. presidential election campaign, highlighting the group’s capability and intent to influence political processes.
APT 41
APT41, also known as Winnti, Barium, or Wicked Panda, is a Chinese state-sponsored cyber threat group known for its dual role in cyber espionage and financially motivated cybercrime. Active since at least 2012, APT41 targets a wide range of sectors, including healthcare, telecommunications, finance, and video game industries. The group employs diverse tactics, techniques, and procedures (TTPs), such as spear-phishing, supply chain compromises, and the use of custom malware to infiltrate networks. APT41 is particularly notable for its ability to pivot from traditional espionage activities to financially driven attacks, including ransomware and cryptocurrency mining.
The activities of APT41 have led to significant economic and security repercussions globally. In September 2020, the U.S. Department of Justice charged five Chinese nationals associated with APT41 with hacking into over 100 companies and entities worldwide.
These groups are composed of highly skilled hackers and often operate under the direction of the Chinese government, particularly the Ministry of State Security (MSS) and the People’s Liberation Army (PLA).
The What & The Why – China’s Motivations For Stealing Data
“Know yourself and know your enemy, and you shall never be defeated.”
Chinese Advanced Persistent Threats (APTs) target a wide range of data across various sectors. The specific data targeted and stolen can vary depending on the APT group and their specific objectives, but generally includes the following types:
- Intellectual Property (IP) and Trade Secrets:
- Technological innovations: This includes sensitive information from sectors where technological innovation is key, such as aerospace (e.g., designs for new aircraft or satellite technology), biotechnology (e.g., genetic research), semiconductors (e.g., chip designs), and automotive (e.g., electric vehicle technology). The aim is often to reduce the time and cost associated with research and development by acquiring innovations from other nations.
- Manufacturing processes: This encompasses proprietary methods, production techniques, and formulas used in manufacturing. For example, a pharmaceutical company’s proprietary process for producing a drug or an electronics company’s methods for fabricating microchips.
- Corporate Data:
- Strategic plans: Corporate strategies can include market expansion plans, new product launches, or competitive tactics. Accessing this information gives competitors an unfair advantage.
- Client and partner information: Information about key clients, partners, and their contracts or negotiations can be exploited to undercut or sabotage business deals.
- Employee data: Personal information about employees, such as social security numbers, addresses, and employment history, can be used for targeted attacks or to compromise individuals who hold critical positions within an organisation.
- Government and Military Information:
- Defence and military secrets: This includes detailed information about defence systems, weapons designs, military operational plans, and intelligence reports. Such data is critical for national security and military advantage.
- Diplomatic communications: Sensitive communications between diplomats, government officials, and international bodies. This can provide insights into negotiation tactics, foreign policy strategies, and international relations.
- Healthcare Data:
- Patient records: Patient data includes medical histories, diagnoses, treatments, and personal identification information. This data is valuable not only for identity theft but also for crafting highly targeted social engineering attacks.
- Medical research: Data from clinical trials and research into new treatments and drugs is invaluable for both economic and public health reasons. Stealing this data can provide a competitive edge in the pharmaceutical industry.
- Financial Data:
- Banking information: Includes account numbers, transaction histories, credit card information, and other financial records. This data can be used for financial fraud or to gain insights into the financial health of organisations.
- Payment systems: Information related to the security and operation of payment processing systems, such as those used in banking and retail. Compromising these systems can lead to large-scale financial theft or disruption.
- Energy and Infrastructure Data:
- Operational data: Details about the daily operations of critical infrastructure such as power grids, water supply systems, and telecommunications networks. This information can be used to disrupt services or to understand and replicate operational efficiencies.
- Designs and security details: Blueprints and security protocols for infrastructure facilities, which can be used to plan attacks or unauthorised access.
- Academic and Research Data:
- Scientific research: Data from academic research projects, particularly those in cutting-edge fields like artificial intelligence, quantum computing, and nanotechnology. This can accelerate a nation’s technological progress by acquiring the latest scientific breakthroughs.
- Educational resources: Curricula, exam results, and other educational materials can be used to understand and influence the educational standards and outputs of other countries.
The Where – Understanding Which Nations Are Targeted
Chinese Advanced Persistent Threat (APT) groups, which are often associated with state-sponsored cyber activities, have targeted a wide range of countries over the years. Some of their primary targets include:
- United States:
- Chinese APT groups have consistently targeted U.S. government agencies, including defence, diplomatic, and intelligence entities, to gather political and military intelligence.
- Additionally, they have sought to steal intellectual property from U.S. corporations, particularly in the technology, aerospace, healthcare, and energy sectors.
- Some notable incidents include the hacking of the Office of Personnel Management (OPM) in 2015, which compromised the sensitive personal data of millions of federal employees, and the targeting of defence contractors involved in sensitive military projects.
- European Countries:
- European nations have been targeted for intellectual property theft, economic espionage, and political influence operations.
- Chinese APT groups have focused on stealing cutting-edge technology, research, and development data from industries such as aerospace, automotive, telecommunications, and pharmaceuticals.
- European governments and diplomatic institutions have also been targeted for intelligence gathering and monitoring political developments.
- Asian Countries:
- China’s regional rivals, such as Japan and South Korea, have been targeted for political and military intelligence gathering, as well as stealing advanced technology.
- Countries like India have experienced cyber intrusions aimed at accessing sensitive government information, military strategies, and technological advancements.
- Southeast Asian nations have been targeted for economic espionage, particularly related to infrastructure projects, natural resources, and geopolitical influence.
- Taiwan:
- Due to the ongoing political tensions between China and Taiwan, Taiwanese government agencies, defence contractors, and organisations have been frequent targets of Chinese cyber espionage.
- The aim is to gather intelligence on Taiwan’s defence capabilities, political developments, and cross-strait relations.
- Australia:
- Australian government institutions, defence contractors, and companies across various sectors have been targeted for intellectual property theft, economic espionage, and monitoring of political developments.
- Notable incidents include cyber intrusions targeting universities and research institutions to steal sensitive research data and technology.
- Canada:
- Canadian government agencies, particularly those involved in defence, foreign affairs, and natural resources, have been targeted for intelligence gathering.
- Chinese APT groups have also targeted Canadian companies in sectors such as aerospace, telecommunications, and mining for economic espionage purposes.
- Africa and Latin America:
- While less extensively reported, there have been instances of Chinese cyber espionage targeting countries in Africa and Latin America.
- These activities often revolve around gaining access to natural resources, monitoring infrastructure projects, and influencing political developments in alignment with China’s strategic interests.
Overall, Chinese APT groups demonstrate a global reach in their cyber operations, driven by motivations such as geopolitical competition, economic advantage, and technological advancement. They employ sophisticated techniques to infiltrate networks, exfiltrate data, and maintain persistent access for intelligence gathering and other strategic objectives.
The When – A Timeline of Chinese Threat Actor Activity
“If you know the enemy and know yourself, you need not fear the result of a hundred battles.”
For 2500 years, the teachings of Sun Tzu have been the backbone of Chinese military doctrine. As his text, The Art of War, has become more popularised, its teachings have been applied across other walks of life, particularly business and governance. Chinese offensive cyber policy has also followed these principles, and what we have previously discussed shows how China is utilising cyber crime activity to gather information and intelligence to satisfy a broad range of objectives.
Over the years, the finger of blame has been levelled at China for some of the biggest data breaches and incidents of corporate espionage. We look at some of these below:
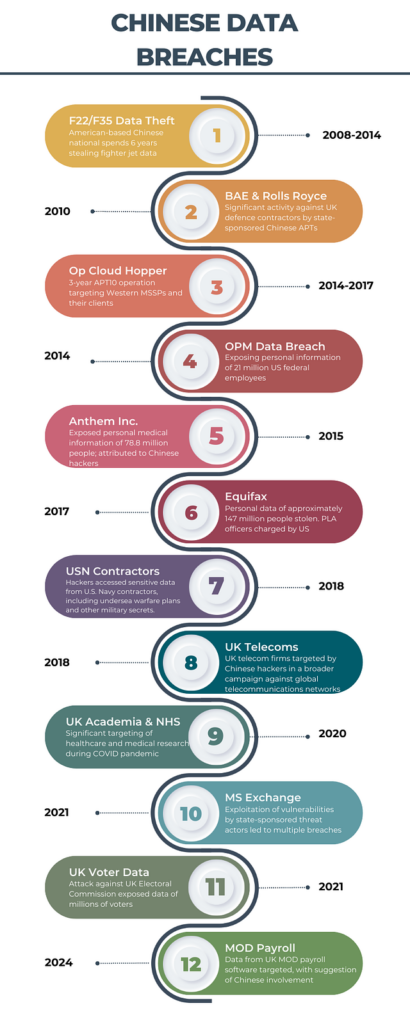
The How – Common TTPs Utilised By Chinese Threat Actors
Chinese Advanced Persistent Threat (APT) groups employ various sophisticated techniques to steal data from targeted organisations. Their methods often involve multiple stages, including reconnaissance, initial compromise, establishing a foothold, escalating privileges, internal reconnaissance, data exfiltration, and covering their tracks. Here are some common techniques and tactics used by Chinese APTs:
- Reconnaissance
Chinese APTs conduct thorough reconnaissance to tailor their attacks effectively:
- Open Source Intelligence (OSINT): Gathering information from social media platforms, corporate websites, and public records to identify key personnel and network architecture.
- Phishing Campaigns: Utilising spear-phishing emails targeting specific individuals within an organisation to collect credentials or deliver malware. For example, APT41 has been known to send emails mimicking trusted contacts or business partners.
- Initial Compromise
Common methods for initial network penetration by Chinese APTs include:
- Spear-Phishing Emails: Highly targeted emails containing malicious attachments or links. APT10 frequently used this method to deliver malware like PlugX or Poison Ivy.
- Exploiting Zero-Day Vulnerabilities: Identifying and exploiting vulnerabilities before they are publicly known. APT3, for instance, has leveraged zero-days in widely used software such as Adobe Flash and Internet Explorer.
- Supply Chain Attacks: Compromising software updates or hardware components. APT41 has been implicated in attacks on software supply chains, embedding malware in legitimate software updates.
- Establishing a Foothold
Once access is gained, Chinese APTs work to maintain a persistent presence:
- Malware Deployment: Installing Remote Access Trojans (RATs) like Sakula, used by APT10, or variants of the Cobalt Strike framework employed by APT41.
- Setting Up Command and Control (C2) Channels: Creating secure channels to communicate with infected systems. APT41 often uses DNS tunnelling and HTTP/S protocols to evade detection.
- Privilege Escalation
To gain higher privileges, Chinese APTs use various techniques:
- Credential Dumping: Tools like Mimikatz are frequently used by groups such as APT41 to extract credentials from Windows systems.
- Exploiting Privilege Escalation Vulnerabilities: Utilising known vulnerabilities in operating systems and applications. APT3 has exploited vulnerabilities in Windows to escalate privileges and move laterally within networks.
- Internal Reconnaissance
Mapping the internal network to locate valuable data involves:
- Network Scanning: Using tools like Nmap to identify live hosts and services. APT10 often employs custom network scanning tools.
- Lateral Movement: Utilising credentials and tools like PsExec or WMI to move across the network. APT41 is known for its proficiency in lateral movement, using legitimate administrative tools to avoid detection.
- Data Exfiltration
Stealing data while avoiding detection is critical:
- Data Compression and Encryption: Compressing and encrypting data to expedite transfer and evade detection. APT10 has been known to use tools like WinRAR for compression and encryption.
- Steganography: Embedding data within other files or images. APT groups may use steganography to hide data within innocuous files.
- Covert Channels: Employing techniques like DNS tunnelling or HTTPS to transfer data. APT41, for example, has used custom protocols to exfiltrate data over HTTPS.
- Covering Tracks
Chinese APTs employ various methods to avoid detection and analysis:
- Log Deletion and Manipulation: Removing or altering logs to erase evidence of their activities. APT10 has been observed cleaning up after themselves by deleting logs and temporary files.
- Use of Proxy Chains: Routing traffic through multiple compromised systems to obscure the origin of their actions. APT41 often uses a series of compromised machines to route their traffic, making it difficult to trace.
- Anti Forensic Techniques: Using tools to thwart forensic investigations, such as wiping tools or encrypting malware payloads. APT3 has been known to employ these techniques to hinder analysis.
In Conclusion
China’s use of cybercrime to obtain data is a testament to the strategic importance of information in the modern world. As China continues to leverage cyber capabilities to advance its national interests, the global community faces the challenge of balancing technological advancement with security and ethical considerations.
The ongoing cyber skirmishes highlight the need for robust international norms and cooperation to address the complexities of cyber espionage and cybercrime, ensuring a secure and stable digital future for all.
By understanding the scope, motivations, and methods behind China’s cyber activities, the international community can better prepare and respond to the evolving landscape of cyber warfare. As data becomes increasingly integral to national security and economic prosperity, safeguarding it against state-sponsored cybercrime will be crucial in maintaining global stability and trust in the digital age.
The future of cybersecurity will depend on collective efforts to strengthen defences, establish clear policies, and foster international collaboration to mitigate the risks posed by cyber espionage and cybercrime.
UPDATE – join us on the 13th June for the accompanying webinar.
Further Reading
UK Electoral Commission Breach
https://www.bbc.co.uk/news/uk-politics-68652374
MOD Payroll Breach
https://www.bbc.co.uk/news/uk-68967805
How does China use it’s data
https://www.nzz.ch/english/how-does-china-use-the-personal-data-it-steals-ld.1828192
F22/F35 Program Breaches
https://www.sandboxx.us/news/the-man-who-stole-americas-stealth-fighters-for-china



Recent Comments