02 – 08 September 2024
CVE Discussion
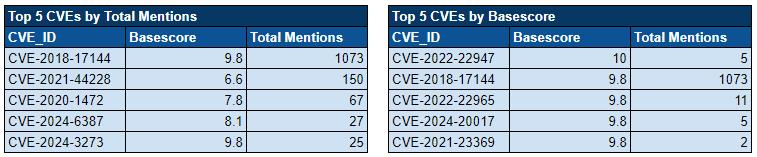
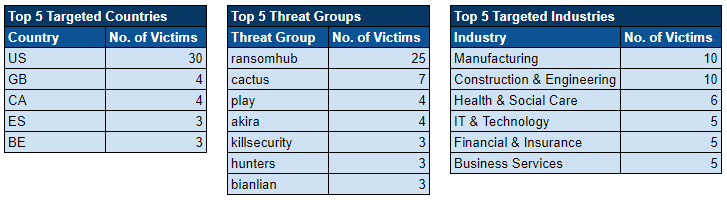
Over the past week, we’ve monitored our vast collection of new data to identify discussions of CVEs.
Ransomware Top 5s
News Roundup
New Malware Exploits Google Sheets for Data Theft and Control
In August 2024, cybersecurity researchers at Proofpoint discovered a novel malware campaign, nicknamed “Voldemort,” that exploits Google Sheets for storing and transmitting stolen data. This backdoor malware takes advantage of Google Sheets’ trusted status to mask its malicious activities, including issuing commands and exfiltrating data. The threat actor also used various common techniques, such as cobalt strike payloads and Windows LNK files, to deploy additional malicious scripts, particularly targeting systems using the C programming language.
The attack began intensifying on 5 August 2024, affecting over 70 organisations with more than 20,000 malicious messages. Users were redirected to malicious URLs and download pages, where files disguised as PDFs would activate the malware. Once deployed, Voldemort would gather system information and download additional malware from Google Sheets, further spreading within the compromised network. The malware’s sophisticated use of Google’s APIs allowed it to covertly interact with infected machines, creating unique pages within Google Sheets for each victim, which stored stolen data.
Researchers noted that while the malware’s impact was significant, many of the infections occurred within sandbox environments or were targeted at security researchers. Despite this, the actor behind Voldemort remains unidentified, though they are suspected to be an Advanced Persistent Threat (APT) group focused on intelligence gathering. The use of Google Sheets for command and control highlights the increasing complexity of cyberattacks, as cybercriminals find new ways to exploit trusted platforms to bypass detection.
Hacktivist Group Head Mare Exploits WinRAR Vulnerability in Targeted Cyber Attacks
The hacktivist group “Head Mare” has been exploiting a vulnerability in WinRAR, a popular file compression utility, to launch attacks on both Windows and Linux systems. Known as CVE-2023-38831, this flaw allows the group to execute arbitrary code through malicious archive files, enabling them to infiltrate systems and encrypt files. Active since the Russo-Ukrainian conflict, Head Mare primarily targets organizations in Russia and Belarus, aiming to cause significant disruption through sophisticated malware and ransomware attacks.
Head Mare’s toolkit includes a mix of widely available software and custom-developed malware, such as LockBit and Babuk ransomware for encryption, and PhantomDL and PhantomCore for system access and exploitation. Their methods involve phishing campaigns that distribute malicious archives, exploiting the WinRAR vulnerability to gain initial access. Once inside, the group maintains persistence by modifying the Windows registry and creating scheduled tasks. They also demand ransoms for data decryption, adding a financial motive to their politically driven attacks.
The group’s infrastructure is highly advanced, using VPS servers and tools like ngrok for network pivoting and command-and-control (C2) communication. Head Mare employs various evasion techniques, including obfuscating their malware and disguising it as legitimate software. Their activities, which exploit the CVE-2023-38831 vulnerability, emphasise the growing complexity of cyber threats linked to geopolitical conflicts. Organisations in affected regions are urged to patch vulnerabilities and strengthen defences against phishing attacks to mitigate these risks.
Electric Vehicle Owners Targeted by Quishing Attacks via Charging Stations
Electric vehicle (EV) owners are being warned about the rise of “quishing” attacks at charging stations. These attacks involve cybercriminals using fraudulent QR codes to deceive drivers into visiting malicious websites or providing sensitive information. As QR codes become increasingly common for payment and activation at public charging stations, scammers exploit this trust by placing fake QR code stickers over legitimate ones. When unsuspecting users scan these codes, they are redirected to fake payment portals, where their personal data or payment details may be stolen.
The consequences of these attacks can be severe, including financial losses and the installation of malware on users’ devices. Cybersecurity experts warn that as vehicles become more connected, quishing attacks may also evolve to target cars themselves. To protect against these scams, EV owners are advised to inspect charging stations for tampering, use official charging apps, avoid entering payment information on unfamiliar websites, and keep their devices up to date with the latest security software.
Charging station operators are responding to the threat by enhancing security measures, such as using tamper-evident QR codes and increasing inspections. Experts stress the importance of staying informed about these emerging threats, as the expanding EV market presents new opportunities for cybercriminals. With awareness and caution, drivers can enjoy the benefits of electric mobility while protecting themselves from evolving scams like quishing.
Cisco Meraki Systems Manager for Windows Vulnerability Allows Privilege Escalation
Cisco has issued a critical security advisory regarding a vulnerability in the Cisco Meraki Systems Manager (SM) Agent for Windows, identified as CVE-2024-20430. This flaw allows authenticated local attackers to execute arbitrary code with elevated privileges, potentially gaining SYSTEM-level access. With a CVSS score of 7.3, this high-severity vulnerability presents a significant risk to affected systems and requires immediate action. The vulnerability stems from improper handling of directory search paths at runtime, enabling attackers to exploit the system by placing malicious configuration and DLL files.
There are no workarounds for this vulnerability, but Cisco has released software updates that address the issue. Users are strongly advised to upgrade to Cisco Meraki SM Agent for Windows Release 4.2.0 or later. The Cisco Meraki SM Agent for Mac is not affected. Customers can download the updates through the Meraki Dashboard, provided they have a valid license. Systems configured to automatically update will receive the patch to mitigate the risk.
While there have been no reported public exploitations of the vulnerability, Cisco urges users to stay vigilant by consulting the Cisco Security Advisories page for updates and ensuring that their systems are running the latest software versions. Cisco’s proactive approach in addressing this issue underscores the importance of maintaining strong security practices to safeguard against emerging cyber threats.

