SOS Intelligence is currently tracking 183 distinct ransomware groups, with data collection covering 368 relays and mirrors.
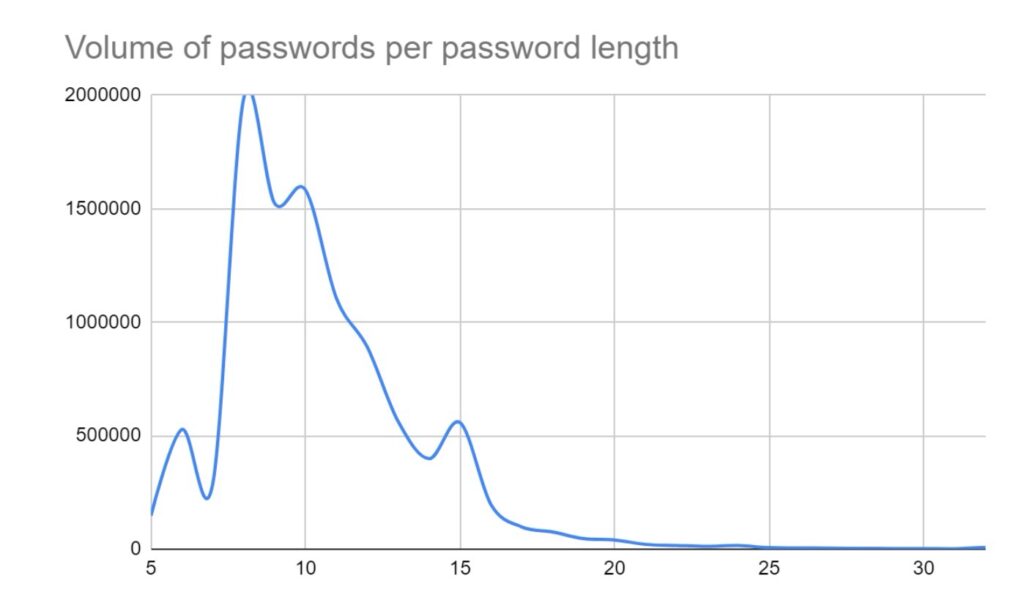
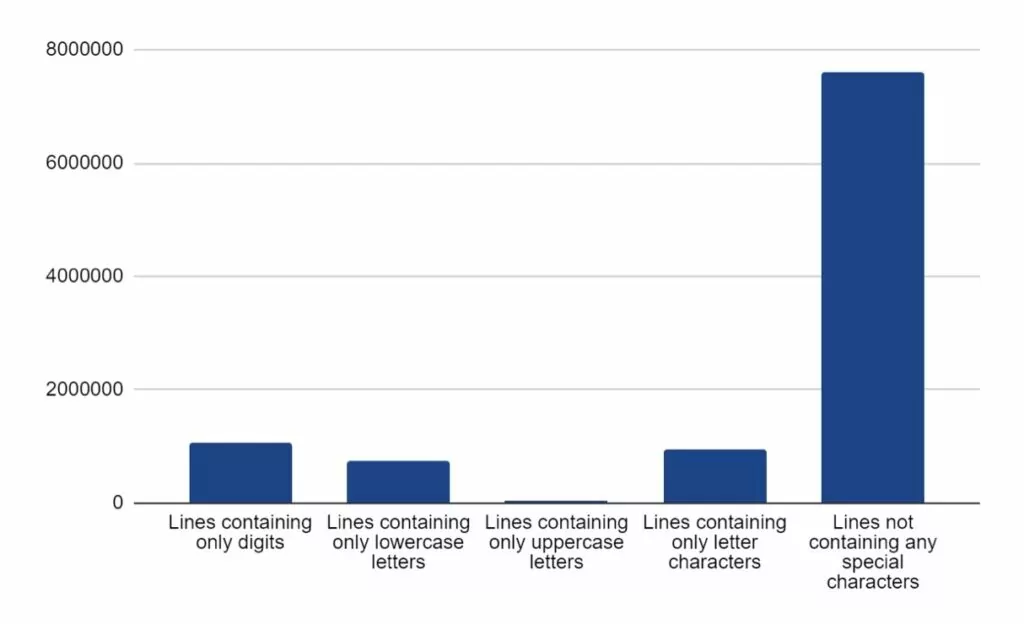
In the reporting period, SOS Intelligence has identified 439 instances of publicised ransomware attacks. These have been identified through the publication of victim details and data on ransomware blog sites accessible via Tor. Our analysis is presented below:
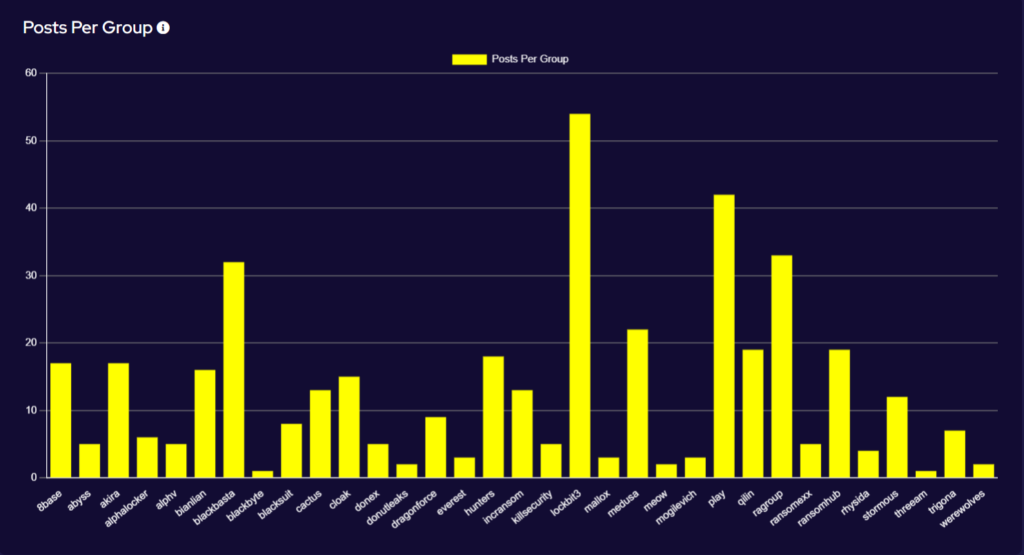
LockBit has maintained its position as the most active and popular ransomware strain, despite law enforcement activity against the group in February 2024. However, we are seeing a significant decrease in their activity level, which is to be expected. The impact of law enforcement activity against the group is still being monitored, but it has already been seen that the group has suffered significant reputation damage. Many affiliates have lost trust in the group to keep their data safe and their identities anonymous.
March also saw the sudden exiting of ALPHV/BlackCat from the scene, in what appeared an exit scam. Affiliates were left stunned when the group shut up shop shortly after receiving a significant ransom from UnitedHealth Group. As previously reported, the code for ALPHV/BlackCat was purported to have been sold, so a new group is expected to emerge using similar TTPs in due course.
As such, we have seen increases in activity amongst other high-profile groups. Most groups have seen small increases in activity over the last month. Still, BlackBasta, Medusa, Play, and RAGroup seem to have profited most from LockBit’s misfortune and ALPHV/BlackCat’s sudden disappearance. All have been operating for at least 12 months and have carved their own niche in the space vacated by these high-profile group.
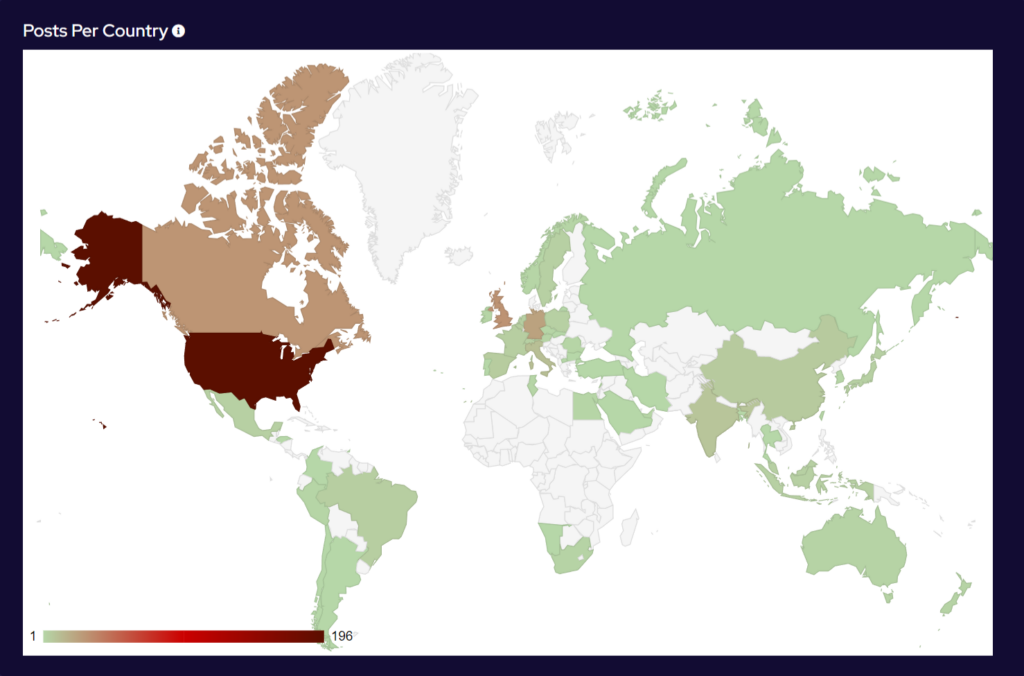
Group targeting continues to follow familiar patterns in terms of the victim’s country of origin.
Attacks have increased in South American countries, particularly in Argentina, which may be a response to presidential elections in November 2023 in which the far-right libertarian Javier Milei was elected. Brazil remains a popular target, as the most economically developed country in the region
Targeting continues to follow international, geopolitical lines. Heavy targeting follows countries that have supported Ukraine against Russia. Attacks against Sweden continued as it pressed ahead with preparations to join NATO. This highlights the level of support ransomware groups continue to show towards the Russian state, and they will continue to use cyber crime to destabilise and weaken Western and pro-Ukrainian states.
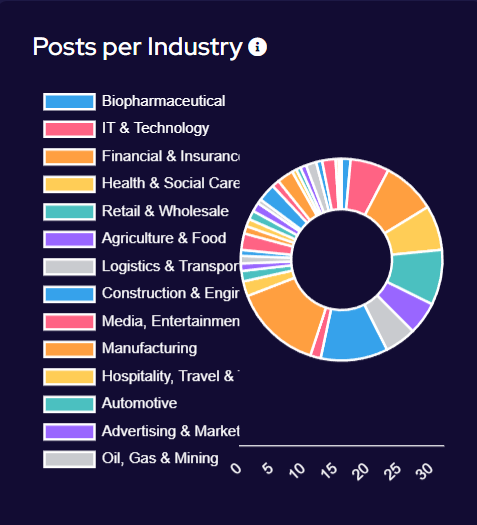
Manufacturing and Construction & Engineering have remained the key targeted industries for March. These industries would be more reliant on technology to continue their business activities, so it logically follows that they would be more likely to pay a ransom to regain access to compromised computer systems. The Financial, Retail & Wholesale, Legal, and Education sectors have also seen increased activity over the period. Health & Social Care has seen a significant increase over the period. This is likely in response to several groups, reacting to law enforcement activity and allowing their affiliates to begin targeting these industries.
We are seeing a shift in tactics for certain industries, particularly those where data privacy carries a higher importance (such as legal or healthcare), where threat actors are not deploying encryption software and instead relying solely on data exfiltration as the main source of material for blackmail and extortion.
Significant Events
Targeting against the UK took an aggressive turn, with NHS Scotland (INC Ransomware) and media outlet The Big Issue (Qilin) amongst the most high-profile victims. This highlights ransomware groups’ apathy towards who they target, and the secondary impacts that that targeting can have.
The Oceania arm of Nissan suffered a significant data breach, which was associated with the Akira ransomware. The attack was limited to operations in Australia and New Zealand but did have a significant impact on distribution, marketing, sales, and services.
New Groups
March saw the emergence of three new groups; Donex, Kill Security (5 victims each) and RedRansomware (12 victims). Kill Security has shown some aggressive public-sector targeting, including police services in India and Romania.
Vulnerability Exploitation
BianLian and Jasmine groups have been observed exploiting CVE-2024-27198 (CVSS 9.8). This is a vulnerability in JetBrains TeamCity CI/CD server products up to version 2023.11.4, which allows a remote unauthenticated attacker to execute arbitrary code to take complete control of affected instances. This would allow threat actors to gain access and maintain permanence within an affected network, while conducting reconnaissance, exfiltrating data, and uploading ransomware payloads.
JetBrains has implemented a fix for the impacted system, so it is advised to update to the latest available version.






Recent Comments