KEY TAKEAWAYS
-
- Threat Actors can deploy stealer malware to obtain sensitive information from a wide range of victims
-
- Compromised data can include email/password combos, financial information, and cookie data allowing replication of sessions
-
- Data is sold openly over the clear and dark web, with corporate data given more value.
-
- Sale of corporate data opens the victim to increased risk of further cyber attacks, impacting them operationally, financially and reputationally.
-
- SOS Intelligence is routinely analysing large quantities of stealer log data to generate alerts for our clients to inform them when their data is at risk. This allows them to take action before the issue escalates
INTRODUCTION
The development of the digital age has allowed the world to become increasingly interconnected. Global entities can share information and data more freely, the scale and magnitude of which is ever increasing. The price of this era of booming interconnectivity is an enormous attack surface: every individual’s and organisation’s data is increasingly exposed to threat actors.
This is because, in a digital world, personal and sensitive data has value. To legitimate organisations and businesses, this data can be useful to provide better products and services to their customers. However, to a threat actor, this data represents an opportunity to learn about a victim, identify their digital weak spots, and exploit those vulnerabilities for financial gain. Stealer logs offer a convenient opportunity to a threat actor granting them authentication tokens and credentials where the attacker does not have to break in, they just log in.
While there is a multitude of methodologies available to a threat actor to make money through cybercriminal activity, this article will focus on stealer logs.
WHAT ARE STEALER LOGS
A stealer log is a collection of data assembled from a victim’s device. These logs are generated by malicious software on the target device (typically running a Windows OS). Once the victim is infected, the malware then proceeds to gather personal and sensitive data to exfiltrate this back to a server being controlled by the threat actor.
There are multiple varieties of stealer logs. We observe the most common to be Racoon, Redline, Titan, and Vidar, but many others can and do exist. While many strains of virus have been developed and utilised, their overall function remains consistent and the data they collect is similar across all variants. We discuss a typical log below:
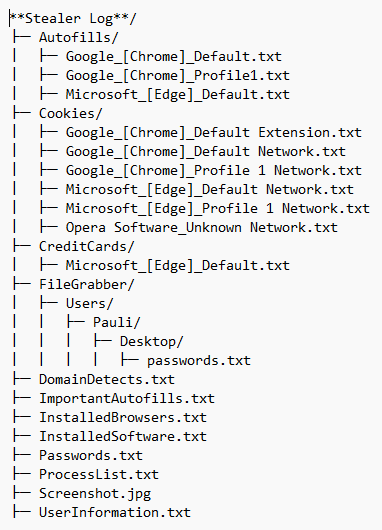
Fig. 1. – An example file tree of a typical stealer log
**Stealer Log**/
Naming conventions for individual logs vary from stealer to stealer, but this can include such details as victim country, victim hardware id (HWID), and the date and time of capture.
HWIDs are unique and are used as a security measure by Microsoft when Windows is activated. They are generated when an OS is first installed. Date and time details can be used to verify the veracity of the data.
├─ Autofills/
│ ├─ Google_[Chrome]_Default.txt
│ ├─ Google_[Chrome]_Profile1.txt
│ ├─ Microsoft_[Edge]_Default.txt
We input a lot of data into web browsers. To make this process easier, most now facilitate the auto-filling of data, saving the user considerable time. This data is stored within the browser for quick and easy recall when required. Stealer logs will routinely target this data, which can include:
-
- Names and DOBs
-
- Addresses
-
- Contact details (email addresses, telephone numbers etc)
-
- Partial credit card details
Access to this data poses a significant risk. Threat actors can and will use this gathered information to develop a profile of the victim, making it easier for them to launch successful, socially-engineered attacks.
├─ Cookies/
│ ├─ Google_[Chrome]_Default Extension.txt
│ ├─ Google_[Chrome]_Default Network.txt
│ ├─ Google_[Chrome]_Profile 1 Network.txt
│ ├─ Microsoft_[Edge]_Default Network.txt
│ ├─ Microsoft_[Edge]_Profile 1 Network.txt
│ ├─ Opera Software_Unknown Network.txt
Web browsers will also store temporary files or cookies. These will contain details about credentialed sessions on the browser, but not password information. The risk caused by the exposure of this data is that it allows a threat actor to replicate account access, potentially bypassing login details to access more sensitive information.
├─ CreditCards/
│ ├─ Microsoft_[Edge]_Default.txt
Web browsers may also save financial information, for ease of access when making online purchases. Some stealer malware variants will seek to extract this information. In this example, unredacted credit card details were saved in the Edge web browser, and extracted in full by the malware.
├─ FileGrabber/
│ ├─ Users/
│ │ ├─ Pauli/
│ │ │ ├─ Desktop/
│ │ │ │ ├─ passwords.txt
Some stealer malware variants possess the ability to extract a victim’s files. Typically, they will focus on file locations which are common across different devices and likely to hold valuable information, such as Desktop or Documents. The example above shows the victim had a text file saved on their Desktop, containing their usernames and passwords for various sites.
├─ DomainDetects.txt
This file is generated by the malware. It reads the extracted information and highlights the most common domains seen in the data. Threat actors use this analysis to identify logs of interest, i.e. those that are accessing websites and services that are of value or can be exploited further.
├─ ImportantAutofills.txt
This file is generated from parsed data from stored auto-fills. It seeks to extract data deemed most valuable to a threat actor, which can include sensitive Personally Identifiable Information (PII) and financial data.
├─ InstalledBrowsers.txt
Details all installed browsers, including version information. Identifying an old browser version could provide a threat actor opportunity to launch attacks using known exploits.
├─ InstalledSoftware.txt
Details all applications installed on a victim device, including version information. This too has value to a threat actor to identify potential vectors for exploitation.
├─ Passwords.txt
The holy grail for stealer malware. Passwords are extracted from web browsers and stored in this file, including the site name, username and cleartext password.
This file has the potential to be the most destructive for a victim and highlights the inherent risks in using native browser password storage, rather than more secure and reputable password managers.
├─ ProcessList.txt
This file contains an extract of the running processes at the time of infection. When used in combination with other gathered data, it can provide a threat actor with the opportunity to attack the device further, by utilising suitable exploits identified through this data.
├─ Screenshot.jpg
Not every stealer malware will do this, but some will take a screenshot of the victims’ screen at the point of infection. This provides some additional information regarding the victim and their habits and activities. This would have the potential to capture sensitive information if the victim is within a corporate network, or provide a threat actor with additional material for making blackmail or ransom threats. We’ve highlighted some examples below:
├─ UserInformation.txt
The last file will generate details regarding the victim’s device, including IPs, hardware, location, and date
SERIOUS ABOUT YOUR CYBER SECURITY?
Book a demo nowHOW IS DATA OBTAINED
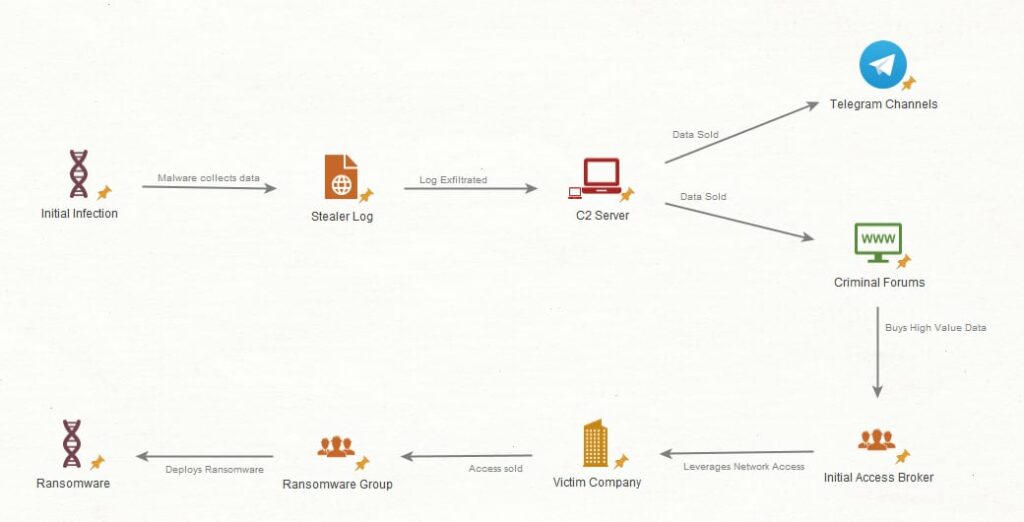
Stealer logs are the result of a malware infection on a victim’s device. Infection vectors cover a broad range of techniques, but typically threat actors will utilise cracked software downloads, illegitimate advertisements, or (spear)-phishing emails. Once installed on a device, the malware is designed to run silently to avoid detection.
Once established, the malware will initiate a connection with a Command and Control (C2) server operated by the threat actor. Here it can receive instructions, download further malicious software (to establish permanence on the system or leverage further attacks), and exfiltrate collected data.
The malware itself is often created by a third party. The author will rarely be the one to deploy it. Access to the malware is sold through forums on the clear and dark web.
HOW IS DATA DISPERSED
Stealer logs mostly derive from personal or home devices or those without the benefit of corporate-level cyber-security. Research conducted by Flare estimates that ~1% of logs pertain to corporate victims. However, millions of logs are obtained each week, so the risk to a corporate network is still viable, and corporate logs are a valuable prize to a threat actor.
Once obtained, logs are collated and dispersed using one of several methods:
-
- Online Marketplaces
Marketplaces on both the clear and dark web will contain sections for selling stealer log data. Low-value logs will be grouped and sold for a small fee. However, marketplaces are focussed more towards providing products for threat actors seeking specific accesses or data. Logs with more value (based on their content), especially those from corporate victims, will more likely be sold on an individual basis, on account of their use in further criminal activity. Value can range from $15 USD for basic logs, $95 USD for healthcare victims, and $110 USD for financial sector victims.
-
- Public Telegram Channels
These will provide a sample of the full collection a threat actor possesses, usually as a free download. This allows customers to determine the quality of the data before committing to purchasing full access. Access to a full collection is charged at a premium and accessed through private channels or a threat actor’s private site. It has been observed that most private channels or data clouds will eventually leak logs into public channels. In some cases, we have observed private channels that were created with a clear intention to bundle other more popular private channel sources and resell those logs as their own.
-
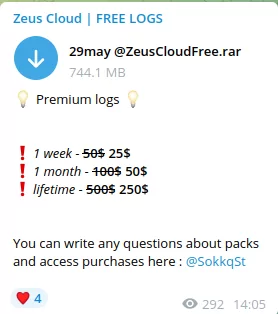
- Private Telegram Channels
Requiring payment to access, private telegram channels are used to disperse logs deemed to hold more value, based on the status of the victim and the contents of the log. Logs are often grouped into large collections, and may also be differentiated by the country of origin, or particular data sets they contain (e.g.containing credentials for premium streaming sites)
WHAT IS DATA USED FOR
Usage and pricing of this data is dependent on the victim.
Data of the private individual is of low value. An individual’s data is often used to steal access to premium services, e.g. video streaming, or utilise scareware/threatware tactics designed to blackmail users into granting further access or making payment. Email/password combos are used as a method to prove the threat actor appears to pose a legitimate threat.
Larger victims, particularly those in the financial, healthcare and government sectors, are more valuable. Data obtained via stealer malware can be used to leverage further access to a corporate network, by providing necessary information to conduct social-engineering attacks, send spear-phishing emails, or even access the corporate network remotely. From there, a threat actor can deploy other malicious software, to obtain network permanence, disrupt systems and/or steal sensitive data.
WHAT ARE THE RISKS TO YOU
The primary risk to any entity unfortunate enough to be targeted by stealer malware is data loss. The level of data stolen by stealer malware is and of itself not overly valuable but, particularly for larger, corporate victims, the real risk lies in what that data is used for after.
Corporate credentials and data can be used to target a company to establish access to a corporate network. In turn, this opens the network to exploitation by a threat actor, and it is common for this access to be exploited using ransomware and other malware tools to extract data and disrupt business activities. As covered in our webinars, this threat can have significant risk to a business, with impacts:
-
- Operationally – by not being able to conduct business
-
- Financially – by loss of income, payment of ransoms, and reparation costs
-
- Reputationally – from failure to maintain the confidentiality of sensitive and/or customer data
-
- Regulatory – from the imposing of fines as a result of data loss.
WHAT IS SOS INTELLIGENCE DOING, AND HOW CAN IT BENEFIT YOU
At SOS Intelligence, we understand the risk that stealer logs pose to the security of your data. What we can provide is early detection for when your data has been exposed. We are actively collecting and analysing stealer log data from multiple sources which feeds into our intelligence pipeline.
Within moments of ingestion, we can generate bespoke alerts for you to indicate when you may be at risk. Early detection is vital to allow you to take action before an issue becomes serious and impactful against your business.
Please don’t hesitate to get in touch or book a demo.
Photo by Towfiqu barbhuiya on Unsplash

