Home » The Dark Web
It started with a tweet.
The dark web has long been associated with illegal activities and the sale of illicit goods and services. Among the many services offered on the dark web, hacking services are particularly prevalent.
We had our PIR and got to writing an Intelligence Requirements sheet following the PESTLEP model and that allowed us to prioritise our Collection Plan.
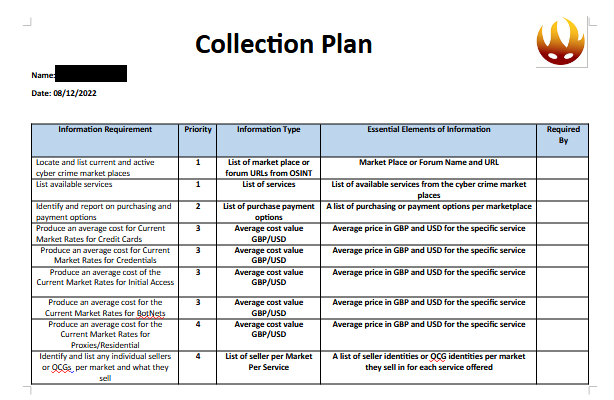
With which we were able to start our collection process and begin answering Daniel Card’s Tweet.
The collection process consisted of using the SOS Intelligence platform to identify current active market places for the specific IR areas we had to answer to.
Our platform has the capability to scan the dark web very quickly, with the ability to rotate around all active Onion services within 24-48 hours. This gives us a clear view of current and active Onion services.
In addition SOS Intelligence has a broad range of automatic closed and open forum collection giving us a real time view into purchases and sales.

The research for this article looked at around 40 different current dark web marketplaces and clear web and dark web forums, where hacking services are commonly offered for sale. The average prices for the services mentioned were determined based on the information gathered from these sources.
According to our research, the average price for a stolen credit card on the dark web is around $243.15.
This may seem like a low price, but the value of a stolen credit card can vary depending on the country it was issued in and the remaining balance on the card. For example, a credit card from the United States may be worth more than one from a less economically developed country. To keep things as like for like as possible we took the average card limit for a USA bank.
Counterfeit money is also commonly available on the dark web, with the average price per $1,000 coming in at around $396.24.
This may seem like a high price, but it’s important to remember that producing high-quality counterfeit money can be a time-consuming and expensive process.
Botnets, which are networks of compromised computers used to launch distributed denial of service (DDoS) attacks, are also commonly available on the dark web.
The average price for a botnet or DDoS attack is around $382.41.
Another common service offered on the dark web is the sale of so called residential proxies, which are more difficult to detect and block as they “proxy” a cyber criminals connection out through a residential ISP. These proxies are used to mask the true IP address of the user and are often used by hackers to avoid detection.
The average price for a residential proxy is around $645 per month.
Finally, initial access to a target network is often available for sale on closed forums and marketplaces. This can include login credentials or vulnerabilities in a network that can be exploited to gain access, Initial Access or AI is typically the first ‘open door’ into a victim’s network and can lead to ransomware.
Prices for this service ranged wildly from a few hundred dollars to tens of thousands, due to wide ranging victims and seller motivations, varying greatly depending on access offered, method of access and compromised company.
The average price for initial access to a network is around $7,700.
In conclusion, the dark web is a hub for a wide range of hacking services, from stolen credit card information to initial access to target networks.
While the prices for these services may seem steep, it’s important to remember that at least for some of the services offered there is a more demand than supply.
It is also important to note that there is no guarantee with any of the services provided and the sellers or marketplaces themselves could be scams or scammers although a majority do offer purchase through escrow.
Header photo by Jefferson Santos on Unsplash.
We thought it would be interesting to show you something we generate every now and again…
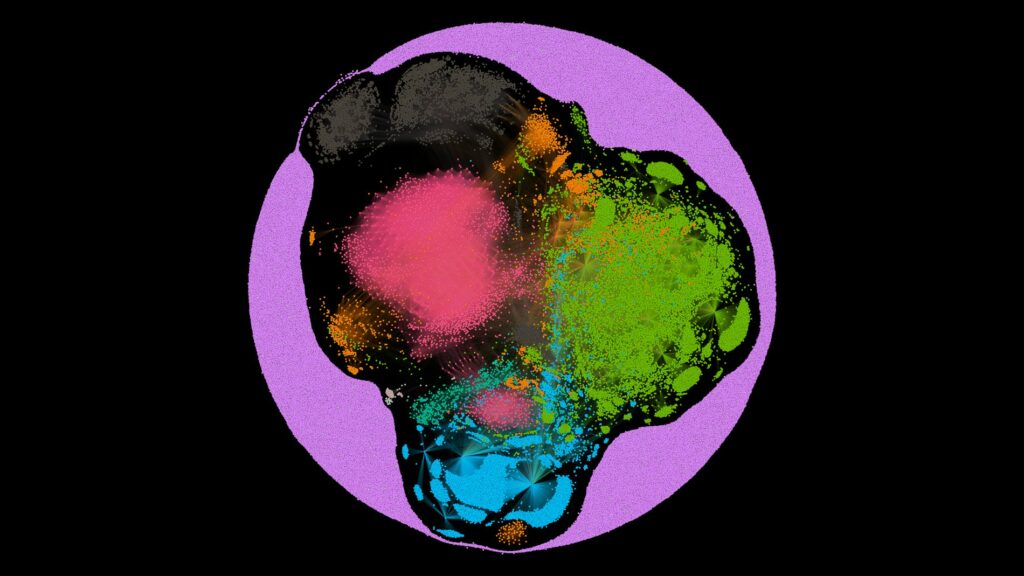
That is our representation of the SOS Intelligence Dark Web Index, the physical placement of the nodes represents the interconnectivity between onion services on the Dark Web (Tor).
It is an energy model of the network structure of the Dark Web.
The diagram is a visual representation of an energy model of the network structure for interconnecting onion services
Essentially, If a node has a lot of links, it has a heavier weight applied to it.
If a node has fewer links, it has a lighter weight applied to it and has less weight represented. The more links, the more central we represent that node on the map. Therefore onion services with fewer inbound or outbound links get ‘pushed’ outward to the edges of the map. Onions with more links weigh more so are positioned more centrally.
The colour is a computed modularity class – the social network of the nodes. We have calculated the community networks of the nodes. i.e. how likely it is that a node is linked to other nodes within the network.
What we get is a spatial representation and social network of around 43000 nodes in the past 24 hours.
The colour itself is random, but the membership of the colour is representative of their social network. What we don’t mean is their Facebook membership, but rather their community connections within the Dark Web.
The visualisation is stunning when seen on a large screen so we have made this available to download here in 4K.
If you are feeling kind, a tweet or short blog post about this would be much appreciated 🙂
Another week and yet another cyber-attack on a major UK company. The Guardian broke the news yesterday highlighting that Go-Ahead are facing problems with their back office systems, including bus services and payroll software.
Fortunately it is only affecting the bus services they run and not their rail business.
There are a couple of important things to note here. Firstly, the UK and other countries are seeing more threats to government organisations, transport and infrastructure companies. Infrastructure, by it’s nature, is vital to the smooth running of a countries’ daily life and an interruption to this can cause serious problems.
One of the most infamous cyber attacks to infrastructure took place last year when hackers breached the Colonial Pipeline using a compromised password.
The key aspect of this case was that investigators suspect hackers got password from dark web leak. This scenario is a perfect demonstration of how SOS Intelligence could have helped, alerting the company to this in time and possibly preventing what happened.
In the UK, companies have faced sizeable fines when they have been the subject of a breach and lost customer data.
British Airways was told in July 2019 that it faced a fine of £183m after hackers stole the personal information of half a million customers. Eventually they paid £20M, still a considerable amount.
If you are reading this and wonder if we can help, we probably can. You can book a call and demo here.
Data breaches are not good for anyone (excluding the cyber criminals), but breaches are particularly bad for industries that handle sensitive information. Unfortunately companies that often handle sensitive data typically do not take their security threats seriously. The pharmaceutical and medical sectors saw a 20% increase in cyber attacks in 2021, costing them, on average, $45,000 per hour of downtime.
The medical industry is not the only industry handling sensitive data. Legal firms hold a tremendous amount of personal data on, not only clients, but also anyone involved in their respective cases.
For threat actors, legal firms hold a treasure trove of data that they can use for criminal activities such as, financial fraud, extortion, or even just crude doxxing.
Unlike hospitals and pharmaceutical companies legal firms typically are not held to the same security and data privacy standards and regulations. In the United States acts like HIPAA and GLBA require any company that handles certain information to abide by set security standards. But, regardless of the law, a data breach looks good for no one.
Defensive security measures like proper data storage and encryption are a must for any legal firm, but these measures can only go so far. In order to take your security to the next level proactive measures are needed.
Luckily for us, threat actors are often very open about their upcoming or ongoing attacks. Hackers will post on dark web forums or even in public chat rooms.
Collecting and aggregating this information can be difficult for a small legal firm with less resources. This is where SOS Intelligence comes in. SOS Intelligence can offer your legal firm – small or large – tools to bolster your proactive security measures.
Due to the nature of established and emerging threat actors, defensive measures like proper data encryption and storage is not enough. Threat actors will always be able to find a way around these defences.
Whether it involves paying an insider for access to your network or exploiting a n-day vulnerability in your VPN software, SOS cyber threat intelligence will be able to provide insider intelligence not found anywhere else.
Our Dark Web monitoring tool can be utilised for searching for hackers discussing your company. You can quickly build a profile on threat actors targeting your firm then proactively adapt your defensive measures to compensate.
Getting a sense for threat actors targeting your firm will do wonders for both your cyber defence and – in the case of a breach – can assist incident response. SOS Intelligence offers tools that can actively pull information from common dark web forums and chat rooms.
Our tools can also grab messages from closed source forums and chats. Dark web monitoring will be able to offer a different perspective than the hundreds of various defensive tools. The SOS Intelligence toolkit will allow you to see through the eyes of a hacker. It’s time to take your security to the next level, try out the SOS toolkit today.
If you are a legal firm who would like some advice on what you need to be doing plus a demo of how we can help you, then click here now to book some time with Amir, our founder. We promise this is something you won’t regret.
Photo by Tingey Injury Law Firm on Unsplash
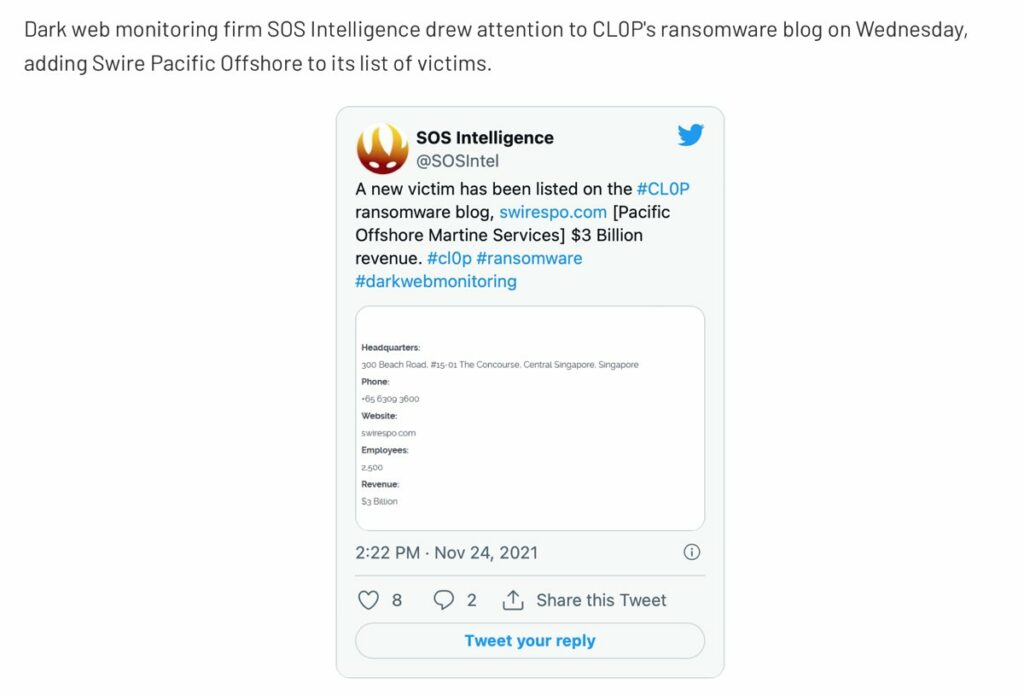
We’ve been featured again over on ITPro. This time it’s about the latest CL0P ransomware group and the news that they have been busy compromising Swire Pacific Offshore (SPO). They announced it had fallen victim to a cyber attack with “some confidential proprietary commercial information” along with personal information believed to be stolen.
Sadly, this is an all to common occurrence and one which is increasing in frequency.
If you are concerned about your cyber security and need to monitor the Dark Web, then please schedule a demo. The best 30 minutes you’ve ever spent cold possibly be a slight exaggeration, but you never know!
You can also follow us on Twitter – @sosintel
This blog post will attempt to give a high-level overview of how we go about automating typically manual Cyber HUMINT ( “a category of intelligence derived from information collected and provided by human sources.”) collection.
Significant elements of this blog will have to be described in general, non-specific, terms or redacted. Due to the nature of the work that we do, keeping our tradecraft methods, tactics and techniques private is important. The methods employed by us are not only commercially sensitive but over disclosure of specific details may render the methods ineffective.
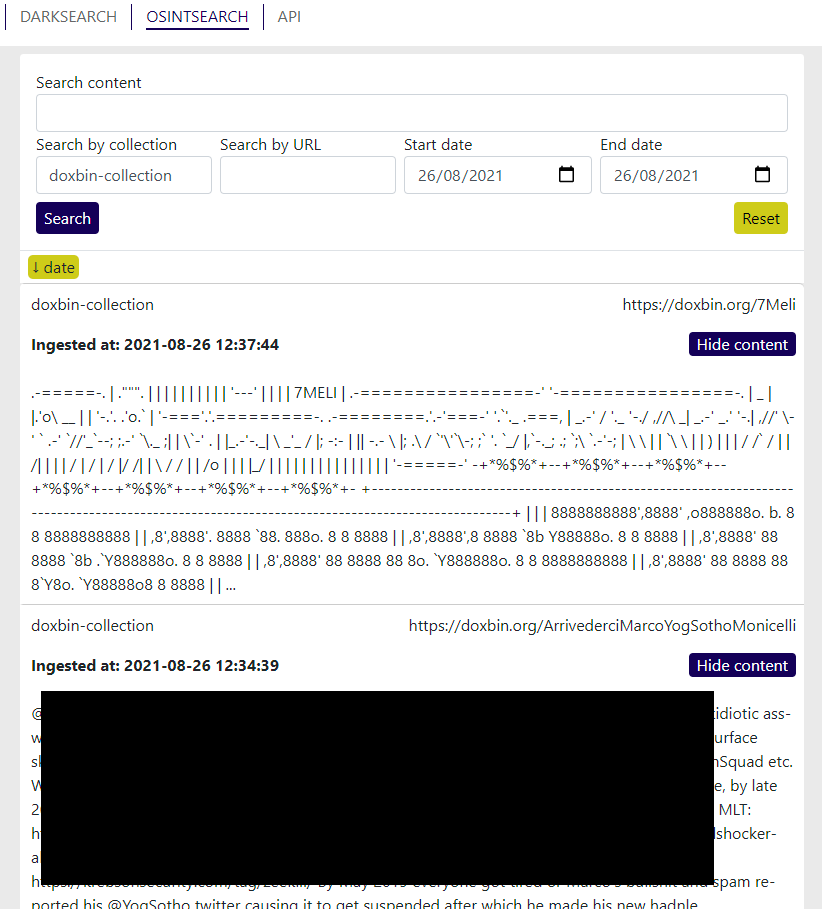
A fair amount of thought and research goes into selecting our OSINT (Open Source INTelligence) sources. For the most part, ideal collection sources would be ones that offer an API (Application Programming Interface) for information scraping and do so without significant restrictions.
For example, Pastebin with a paid account grants access to a reasonable scraping API. Using this API we’ve been able to create a custom collection to download each paste, analyse it for relevant customer keywords and, if any matches found, store the paste & alert our customers.
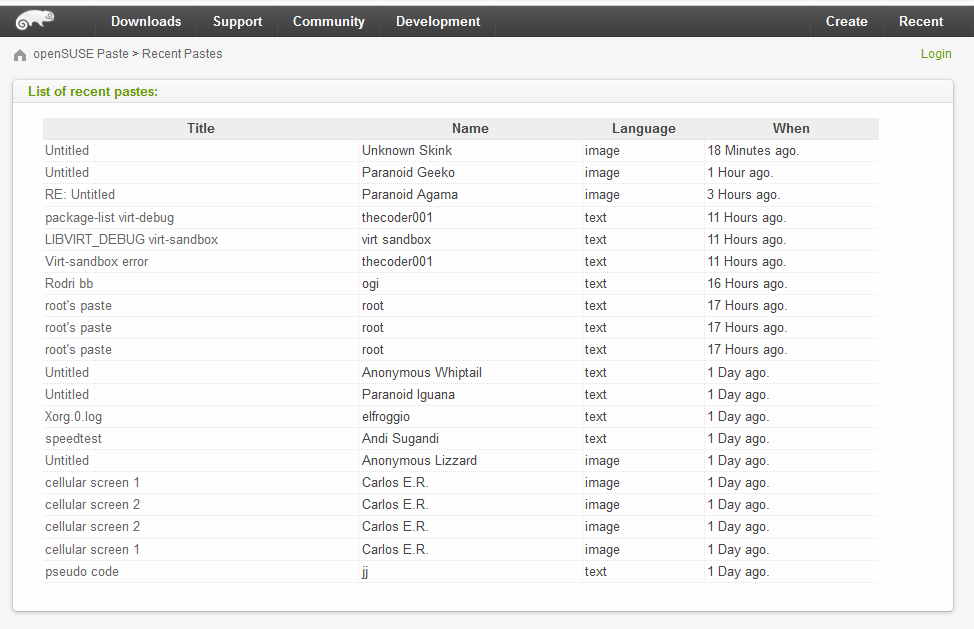
In most cases, however, paste sites typically have no available APIs. Where these sites have a rolling list of new pastes posted, and those pastes can be enumerated & are publicly accessible, further development of a custom collection is required.
An automated process is used to periodically check for new and available pastes, fetch those pastes in a raw format where possible, perform keyword matching and store where needed. A significant number of paste sites that we collect from, either on the internet or Dark Web, fall into this category. Generally there are no significant technical challenges other than the creation of a bespoke collection for each specific source type.
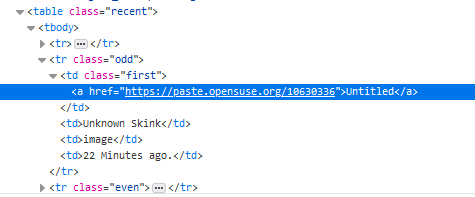
As a general rule, for websites that do not have any specifically designed automated collection or scraping method, we apply a high degree of courtesy and do not aggressively scrape the site.
Since the paste enumeration and paste collection is a fairly lightweight process, and given that pastes in general are uploaded every so often, there is no need for any aggressive polling of a target site.
Some of the sources we collect from are closed, member only, Dark Web or internet hacking forums. Without going into too much detail as to how accounts are created on these forums, an account is essential since we must be able to access topics and posts as well as a roll of recent posts.
In most cases forums helpfully provide a feed of new content by way of RSS (Really Simple Syndication) feed. This can in part, like an API, assist in the creation of a custom automated collection for that source. An additional caveat to this being that the collector passes credentials to the forum so as to appear to be a “logged in” user, e.g. simply viewing posts or browsing the forum.
A good 30% of all the OSINT sources we collect from are authenticated. To maintain continuous automated collection, we ensure that we have a sufficiently well stocked array of back up accounts for each of the forums we collect from.
In some cases the sources we collect from deploy DDoS or Bot Protection. The purpose of this is typically not to prevent scraping or automated collection but more to prevent the site from high volume denial of service attacks.
The bypass for this defence varies depending on the source. In some cases, for example collection from Doxbin, we employed a CloudFlare challenge bypass method that essentially consists of:
Even when fairly advanced bot/browser verification defences have been deployed by the target source, these have thus far all been mitigated and not prevented our automated OSINT collection.
As for the Doxbin example, the challenge of bypassing their new bot protection was significant and on balance, considering the quality of the OSINT source, might not have been warranted. It was, however, still a challenge that couldn’t be left unmatched!
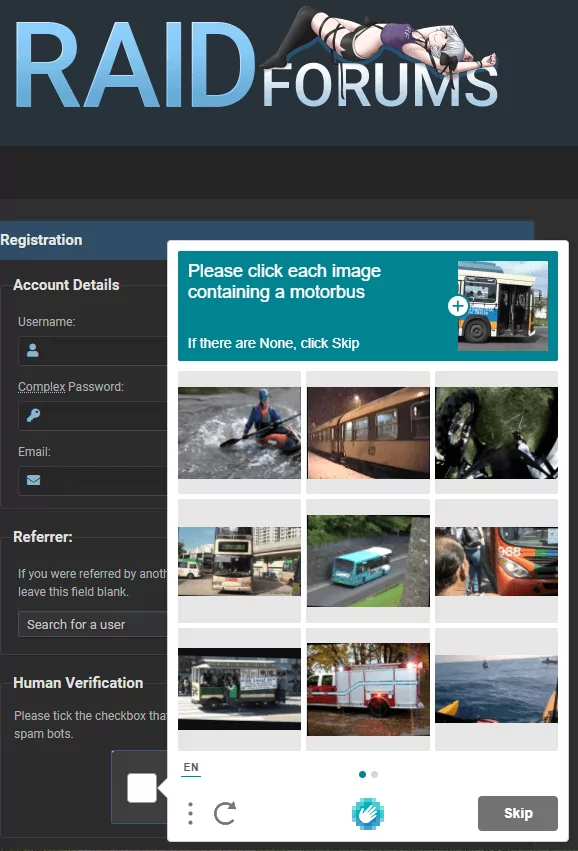
Automated solving of CAPTCHAs is tricky and is probably the toughest bypass we’ve had to solve so far. The amount of detailed technical information that we can share for how we go about bypassing CAPTCHA is very limited. However, it runs along similar lines to the browser challenge process, whereby detection of a CAPTCHA and the solving of it are tied into the automated collection functions.
So far there are very few OSINT sources that employ this type of challenge and we’ve been able to mitigate these in all cases whilst maintaining automated collection.
As with the above topic, it is tricky to discuss and share in any level of detail our methods for remaining “undetected“. However, in general we ensure that the accounts we use do not raise any significant cause for concern to the forum operators.
In most cases, accounts with no post count after a number of months (or sooner!) are deleted. This means that our accounts must have some level of interaction with the forum, however minimal, to ensure their persistence.
We try, wherever possible, to use Tor to access content. This helps preserve our anonymity in as much as not pinning our collectors down to one location. We also ensure we rotate things like user agents and other fingerprints to ensure relative anonymity.
Then important aspect to blending in with the noise is ensuring that collection is not overly aggressive and not overly routine. We achieve this by randomising the frequency and timings of either enumeration of new posts, fetching / viewing posts or pastes. The key is to appear sufficiently “human“. This has afforded us the ability, in some cases, to collect with the same account for a year or more without administrator intervention.
This can be even more challenging than bypassing CAPTCHA challenges. The goal for us is to ensure we have sufficiently robust detections for whenever a logged in session expires; a challenge pass expires; the very likely and common scenario of an overloaded website itself going offline or a Tor circuit is struggling.
To ensure the best chance of successfully reaching a website over Tor, we employ a number of load balanced Tor routers that are themselves proxied and balanced to cater for our crawling services and automated collection.
But things do go wrong, Tor is not the most reliable tool so our collection processes that utilise it have sufficient retry intervals and “back-off” intervals programmed into them. Should one of our requests result in a gateway time out the system will simply retry, hoping it is balanced to a less utilised Tor relay.
At times we do get detected and blocked by forum administrators. In such instances, the system will attempt to detect any “authentication loops” and select another account to continue automated collection with.
Some of the fault detection is relatively simple, such as enumerating how many pages a collection source has and iterating through each page until all pages have been collected.
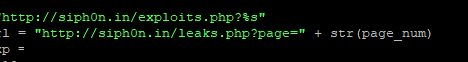
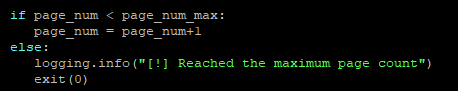
The process is not always perfect, but we try to monitor it and optimise wherever possible. We spend a lot of time on the initial development phases of a collection ensuring that all possibilities, within reason, are accounted for and once a collection goes into production that any following “cat and mouse” changes required are as minimal as possible.
We hope this gives an insight into how SOS Intelligence works. We have a number of plans available and if you would like to schedule a demo, please click here.
Thanks for reading!
Amir
PS If you enjoyed this, we think you also enjoy An investigation into the LinkedIn data sale on hacker forums.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |


Recent Comments