Dark Web Statistics 2023
At SOS Intelligence we routinely scrape and monitor the dark web to provide fast-time intelligence and alerting for our customers. The dark web is a constantly evolving digital entity, and through the data we collect and analyse, we can develop an accurate picture of what the dark web looks like.
What is the Dark Web?
The idea of the dark web is as old as the internet itself although the current terminology did not pick up its general meaning until the early 2000s. As the global need for digital interconnectivity has grown and expanded, so too has the need to communicate and share data privately. The expansion of the “clear web” has therefore been accompanied by a growth in “dark web” services and protocols. But what is the dark web, and where has it come from?
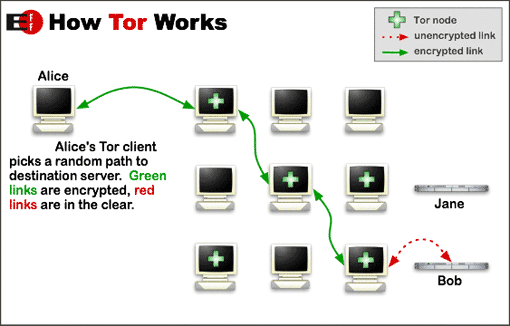
It’s first helpful to consider what the dark web is; sites and content that exist on a dark net. A dark net is an independent network overlaid over the internet as a whole and is only accessible using specially configured software and authorisations. The most prominent example of this is The Onion Router or Tor.
The Onion Router (Tor)
Tor was developed in the 1990s by the US Navy as a means of sharing sensitive information online more securely. In 2004 it was released to the public, such now that anyone with an internet-enabled device can access it. Downloading Tor installs a specially configured browser on the device which can connect to the Tor network. The network itself is made up of approximately 7000 volunteer nodes, which allow traffic to enter, pass through and exit the network.
The principle of Tor is to limit the possibility of online sites tracing data or actions back to a specific user. It is key to note that Tor doesn’t claim to offer full anonymity. Confidentiality on Tor is obtained using encryption. The data to be sent is encrypted and sent into the Tor network. From there, it is sent on a random path of nodes until it exits at another point. In transit, the data has multiple layers of encryption, so that when it arrives at a node and is decrypted, that node can only see where the data has come from, and where to send it next. Using this method, the person receiving the data would only see it originating from the last node in the Tor network. These layers are how onion routing got its name.
Electronic Frontier Foundation – https://www.torproject.org/about/overview.html.en, https://media.torproject.org/image/official-images/tor_design_archive.zip
Dark Web Statistics
At SOS Intelligence we have been collecting content and data regarding the dark web for many years to support our clients’ needs. This has allowed us to collate a wealth of metadata regarding dark web services and sites. For this report, we’ve taken a look at data covering the last 12 months (August 2022 – August 2023) and present our analysis to you below.
Most Commonly Used Dark Web Languages
Below we have highlighted the most commonly used non-English languages today, compared to our data collections from 2018 and 2021.
Although English is by far the most dominant language on the dark web the language distribution across the rest of the domains has remained surprisingly stable since we began indexing in 2018.
- English accounts for 99.20% of language on the Dark Web
- Russian is second with 0.42%
| 2018 | 2021 | 2023 |
|
|
|
The stability of English as the primary language of choice within the Dark Web is likely down to its status in the world as a universal language: it is the most widely spoken language in the world. Increasingly strict internet laws within Russia, particularly pertaining to access outside of the Russian sphere of influence is one possible reason for it remaining the second most popular language. However, this could also be down to the usage of Russian in the most dangerous and high-profile cyber-crime forums.
Dark Web Server Technology
Our indexing technology allows us to collect highly granular data about the Dark Web domains we find.
Here we can see the predominant server technologies powering the Dark Web.
This tells us that Nginx, the popular free and open-source software released by Igor Sysoev in 2004, accounts for 95.77% of all Dark Web server technology. Nginx is an incredibly popular reverse proxy so it is no wonder it has a significant market share as the front for most websites on the internet and Dark web.
| Server Tech | Live | % Use | Change since 2021 | |
| nginx | 42667 | 95.77% | +4.77% | ↗ |
| Apache | 1001 | 2.25% | -5.75% | ↘ |
| lighttpd | 492 | 1.10% | +0.91% | ↗ |
| openresty | 179 | 0.40% | +0.33% | ↗ |
| Microsoft-IIS | 21 | 0.05% | -0.05% | ↘ |
| SimpleHTTP | 19 | 0.04% | New Entry | 🆕 |
| Caddy | 15 | 0.03% | -0.03% | ↘ |
| OpenBSD httpd | 15 | 0.03% | -0.01% | ↘ |
| OnionShare | 14 | 0.03% | New Entry | 🆕 |
| LiteSpeed | 7 | 0.02% | New Entry | 🆕 |
Compared to our previous analysis of this data in 2021, nginx has increased its usage among dark web services.
Dark Net Web Technologies
We also look at the different tools and techniques used in the process of communication between different devices over the dark net.
Analysing this data lets us see not only which versions are out there, but how potentially vulnerable some of these systems are. From collecting web technology information we can gain insights into the most popular frameworks, and their versions and develop an understanding of how up-to-date some websites are.
Overall PHP is the most popular web framework on the Dark web. Of particular note in our data is the range of PHP versions still in use. The majority of observed services using PHP are still using PHP 5.* or PHP 7.*, which reached end of life in 2018 and 2022 respectively.
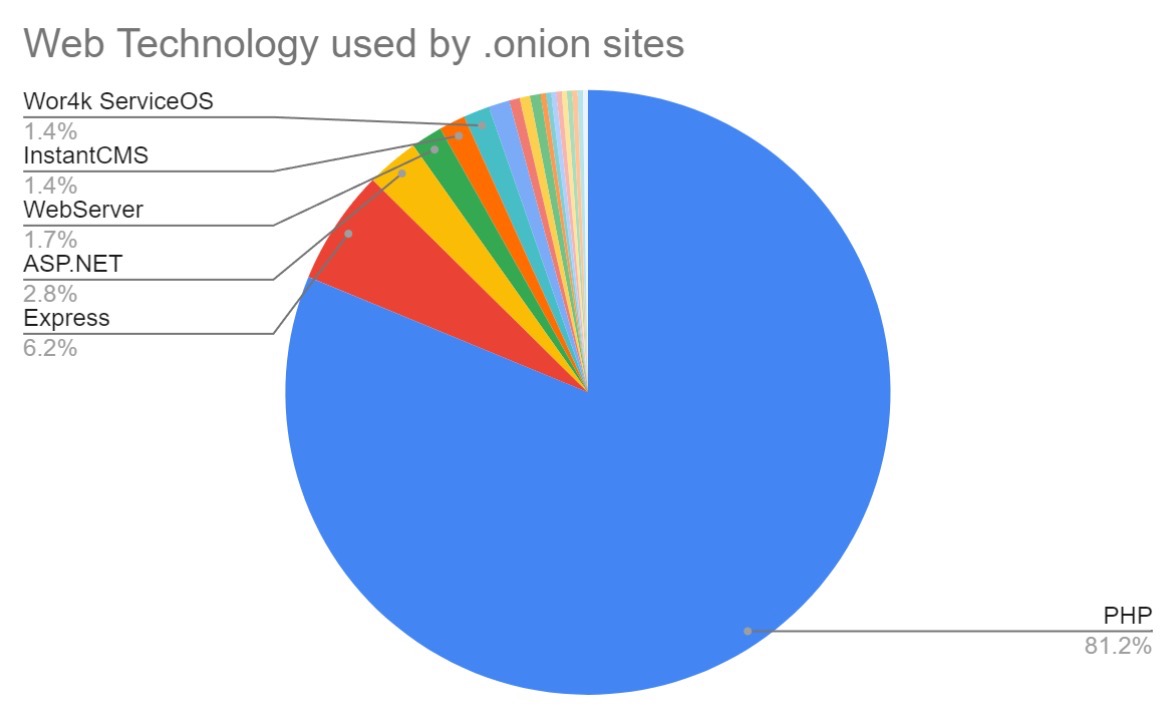
So why PHP? The prominence of PHP is likely down to its relative ease of use. Generally, services and sites on the dark web are created for single, simple purposes and so don’t require a great deal of coding creativity or maintenance to achieve their aims
Common open ports
As SOS Intelligence gathers more and more content from the Dark Web, we also collect metadata regarding the services and sites we scrape. This includes open ports on the host server. This data allows us to glean a surprising amount of information about the servers used to exploit organisations via network compromise, data theft and ransomware.
Port 80 (used for HTTP traffic) and its common alternatives, port 81 and port 8080, account for 99.93% of all open ports observed in our data. Of this, 99.92% of observed open ports are port 80. Second on our list, representing 0.05% of all open ports is port 2082, the default used by cPanel for web hosting control.
How many Onions are live on the Dark Web right now?
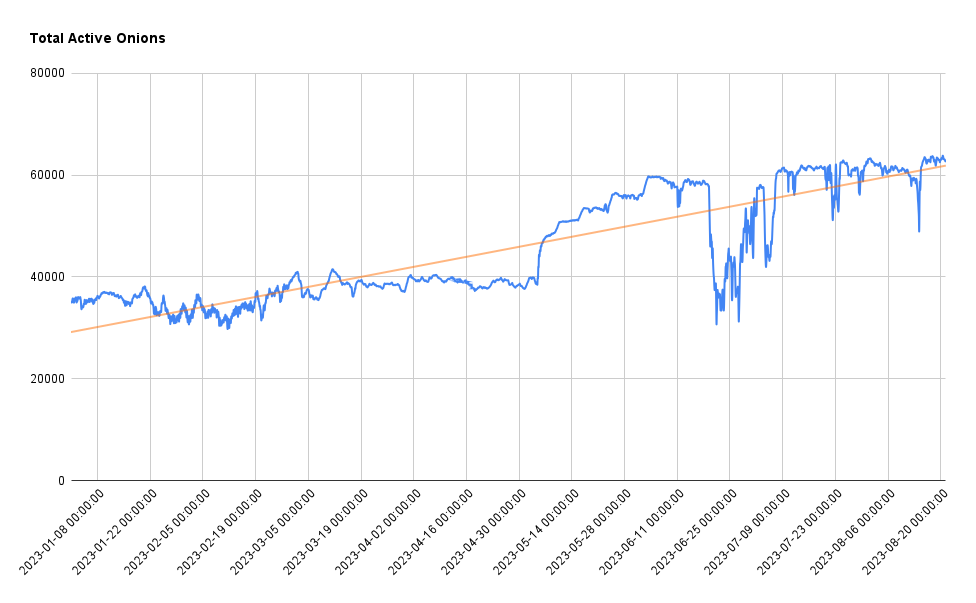
At the time of data collection, we estimate there to be approximately 13,883,010 .onion domains in existence. Of those only about 63,000 are active and online.
As the graph shows, there has been a significant expansion of available .onion sites on the dark web in the past year, an increase of nearly 100% since January 2023. One possible reason for this may be the expansion of ransomware operations, and the newer tactics of generating a unique Onion for each victim.
Learn more about reducing your risk
Book a demo nowRansomware
One of the most prolific users of the dark web are ransomware groups. Sites utilised for ransom payment, and victim and data publication are hosted via the dark web to maintain the anonymity of those behind the attacks.
Ransomware groups come and go, whether through movement onto other tactics or interdiction by law enforcement. Some groups who maintain a more professional, business-like approach, and have maintained the highest operational security, have managed to persist for several years. As of Q2 2023, the following groups have been the most prevalent:
- LockBit3.0 (248 victims – 20.66 per week)
- MalasLocker (172 victims – 14.33 per week)
- AlphV (132 victims – 11 per week)
- Bianlian (118 victims – 9.83 per week)
- 8Base (107 victims – 8.92 per week)
Data courtesy of CyberInt
Ransomware attacks have seen a significant increase over the year to date, from 831 in Q1 to 1386 in Q2 (an increase of 67%). A similar increase has also been observed within the same Q2 period from last year, increasing from 708 to 1386 (an increase of 97%).
Targeting is focused on the US (574 victims), with the UK (60), Canada (56), Germany (48) and Italy (47) filling the top five. One possible reason for this targeting of Western countries could be their NATO membership and continued support of Ukraine in its war with Russia.
The top ten targeted sectors are as follows:
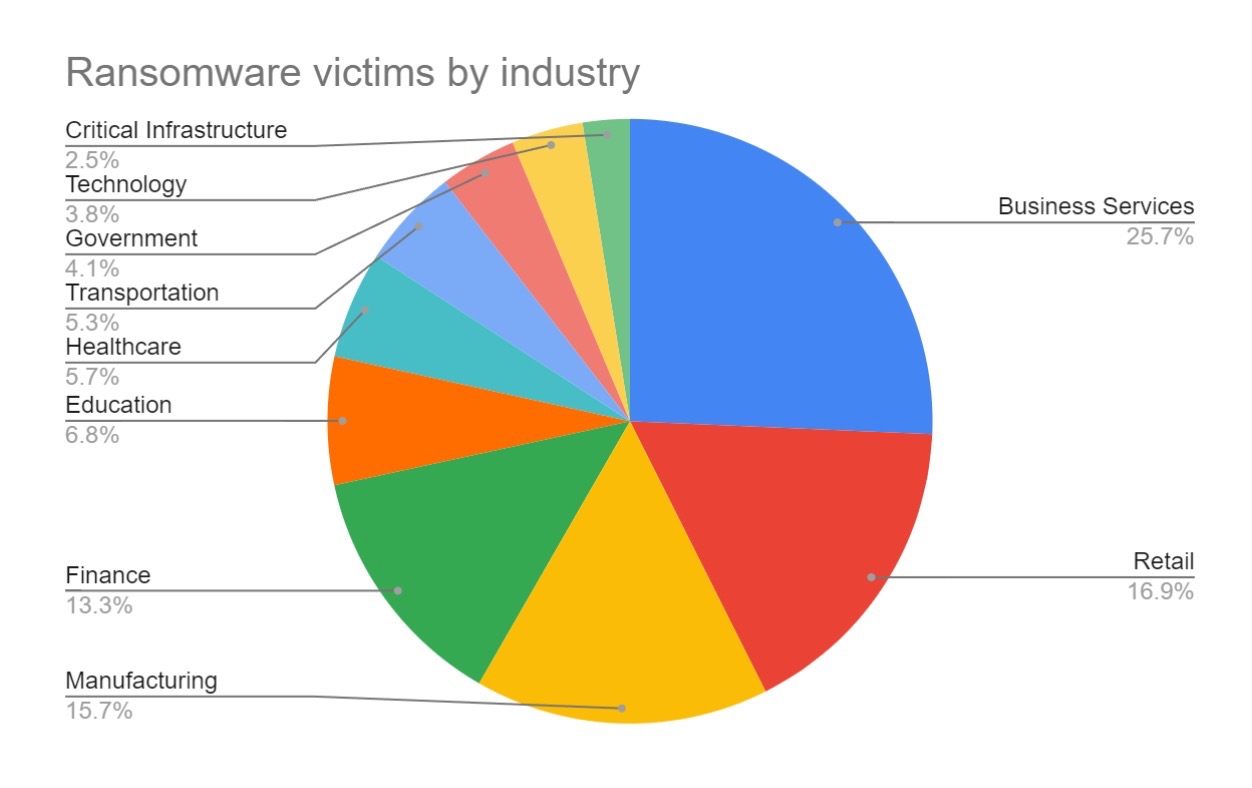
The spread of industry targeting suggests the threat actors’ motivations to be primarily financial. Corporate victims are targeted substantially more, and this is likely due to their level of available funds and the likelihood of paying a ransom.
DARKMAP
As part of our analytical capabilities, we have developed DARKMAP. DARKMAP sits within our analytical platform and provides a graphical representation of the Dark Web: the sites that sit within it and the links they have to others. We can then analyse how popular or accessible a site is based on where it sits within the map.
Sites are grouped based on their “social network”. This means that sites with mutual links are collated together and this is represented by their colour on the chart. Proximity to the centre of the map indicates an increased level of connectivity, whereas those with a single link are pushed to the edge.
We have taken this data and come up with the following hypothesis:
Ransomware blogs belonging to groups with larger numbers of victims will inversely have fewer links, owing to their notoriety providing sufficient advertisement for their public-facing online activity
We’ve utilised data from Darkfeed to give a broad account of the number of attacks by ransomware groups since 2022. In total, we’ve analysed 49 different groups, contributing 5,286 attacks in the last 21 months.
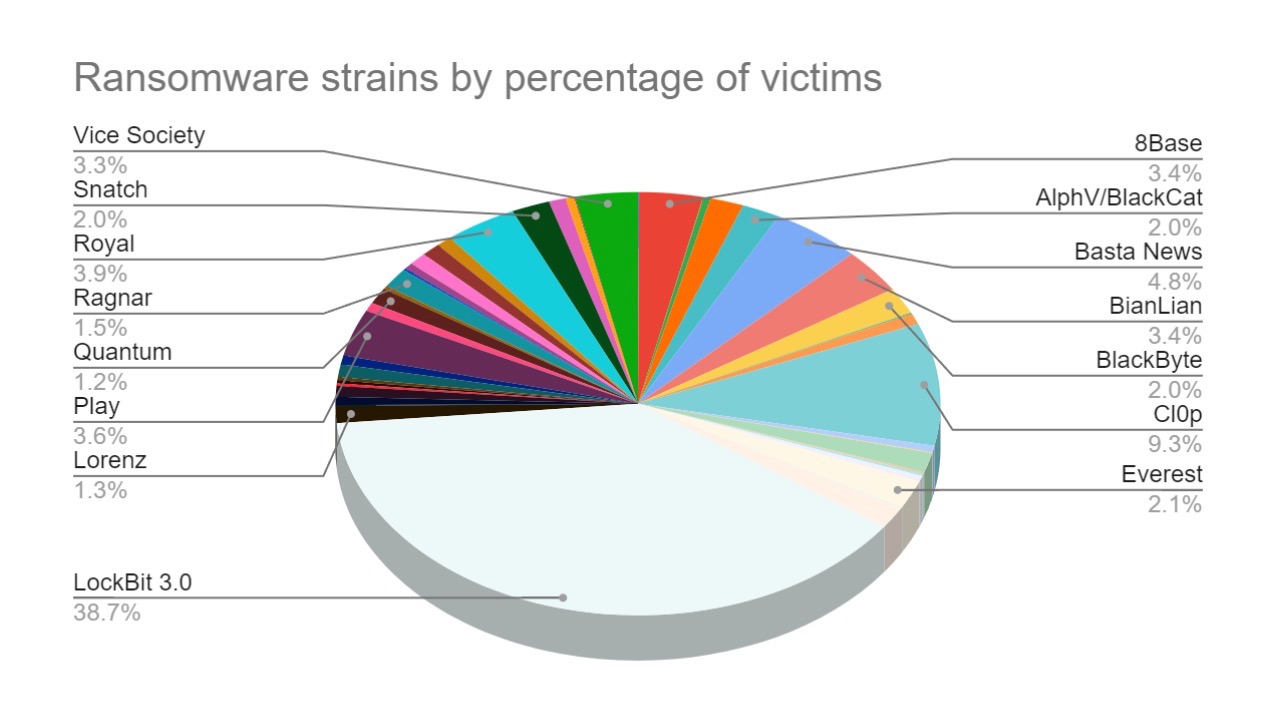
The collected data shows a significant number of attacks attributed to LockBit, accounting for 2044 (or 38.7%) of all attacks within the data range. This is followed by Cl0p with 494 (or 9.3%) and BlackBasta with 253 (or 4.8%).
During the data period, these groups have been some of the most prominent and discussed in cyber-security circles. Therefore, our hypothesis would suggest a limited number of links to their dark web sites. We can utilise the functionality of DARKMAP to test this hypothesis.

Lockbit shows a number of links, both inbound and outbound. Inbound links appear primarily from low-connectivity aggregator sites – those which publish links to other dark web sites. Outbound links are primarily to other Lockbit-controlled sites. Within DARKMAP it is assigned a PageRank of 4.502×10-5.

Cl0p also shows a considerable number of inbound links from aggregator sites. Differing from Lockbit, it only has two outbound links, neither of which contain any data when visited through ToR. The Cl0p site has been assigned a PageRank of 6.993×10-6.

BlackBasta shows a similar profile to Cl0p: it has many incoming links from aggregator sites, but in this case, no outbound links. The site has been assigned a PageRank of 6.650×10-6
Already looking at the three most active ransomware groups, we are seeing that the data is disproving our hypothesis: more popular ransomware groups do have more linked sites and therefore a higher PageRank. When we include data from smaller ransomware groups, this trend can be seen further:
| Group | # of Attacks | % of Attacks | PageRank |
| Lockbit | 2044 | 38.7 | 4.50E-05 |
| Cl0p | 494 | 9.3 | 6.99E-06 |
| BlackBasta | 253 | 4.8 | 6.65E-06 |
| RagnarLocker | 80 | 1.5 | 6.87E-06 |
| Mallox | 33 | 0.62 | 6.34E-06 |
| Monti | 13 | 0.25 | 6.56E-06 |

