Ransomware – State of Play
June 2024
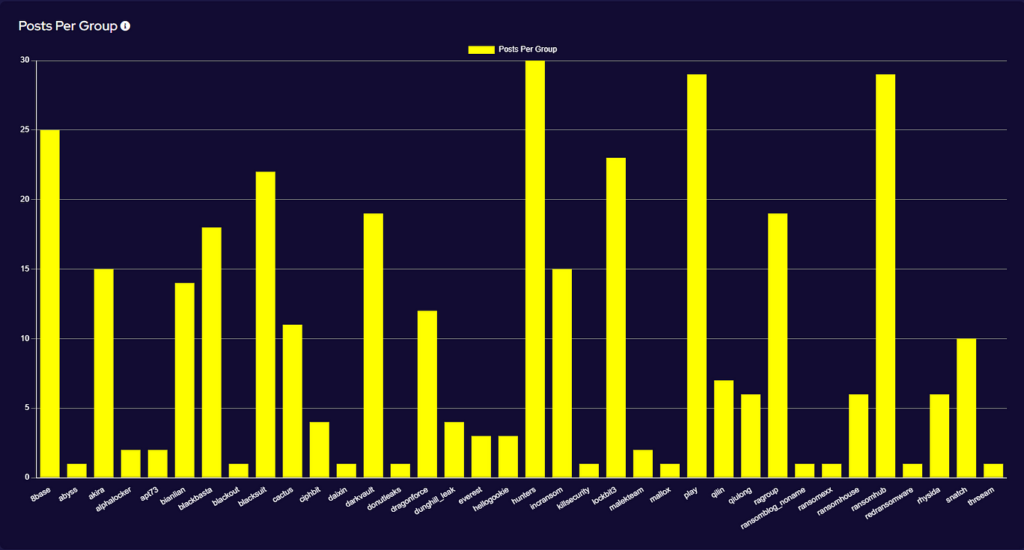
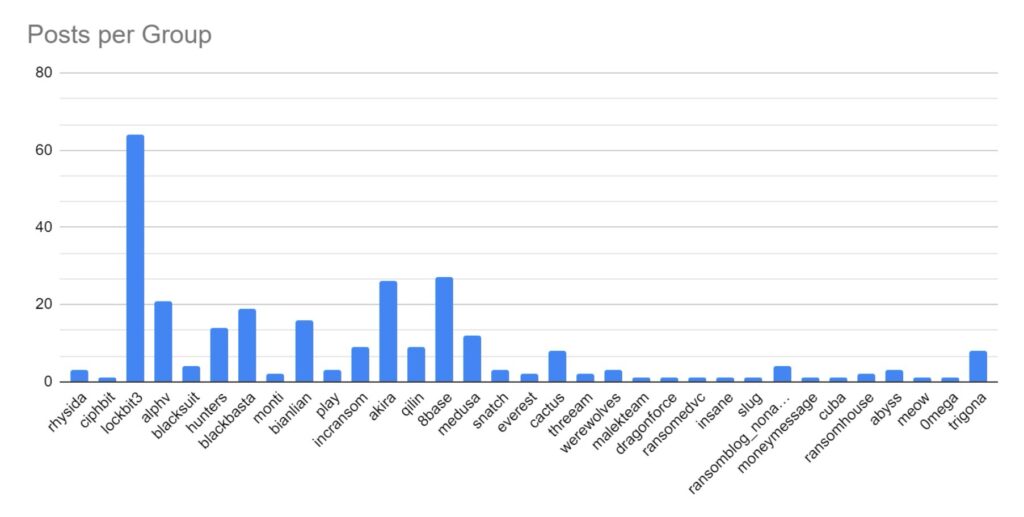
SOS Intelligence is currently tracking 199 distinct ransomware groups, with data collection covering 393 relays and mirrors.
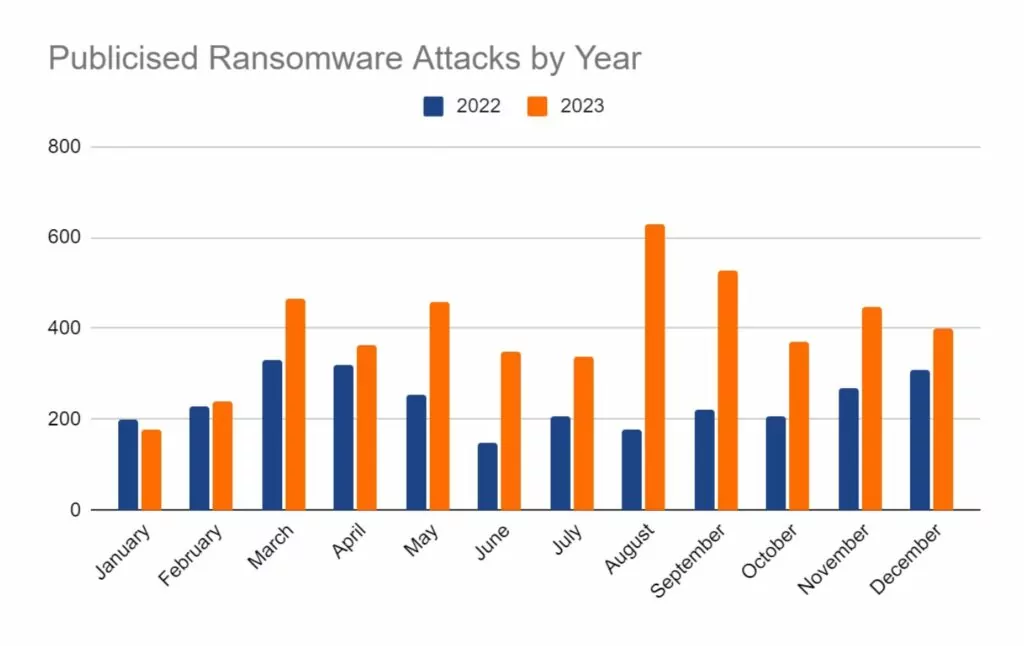
In the reporting period, SOS Intelligence has identified 381 instances of publicised ransomware attacks. These have been identified through the publication of victim details and data on ransomware blog sites accessible via Tor. While this data represents known and publicised data breaches and ransomware attacks, the nature and operation of these groups means that not every successful attack is published and made public, so true figures on the volume of attacks are likely to be higher. Our analysis of available public data is presented below:
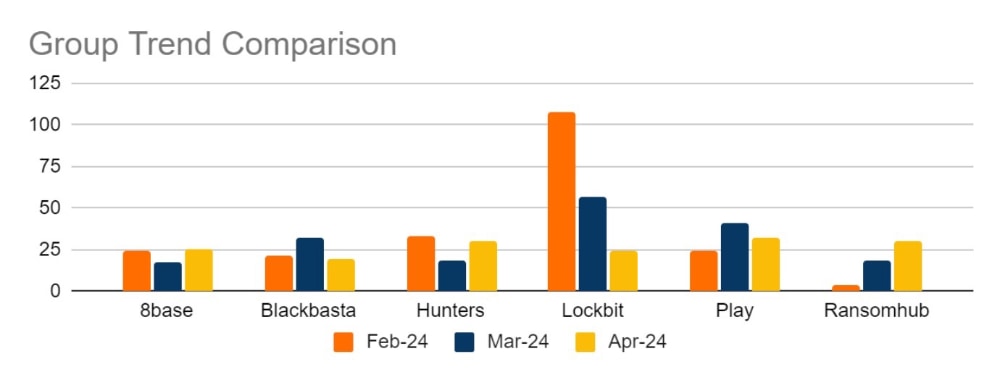
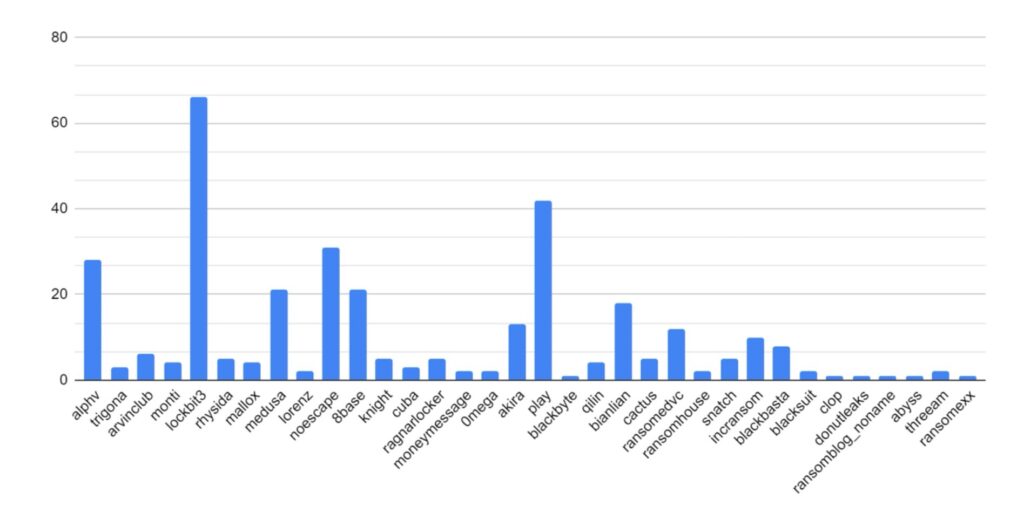
Threat Group Activity and Trends
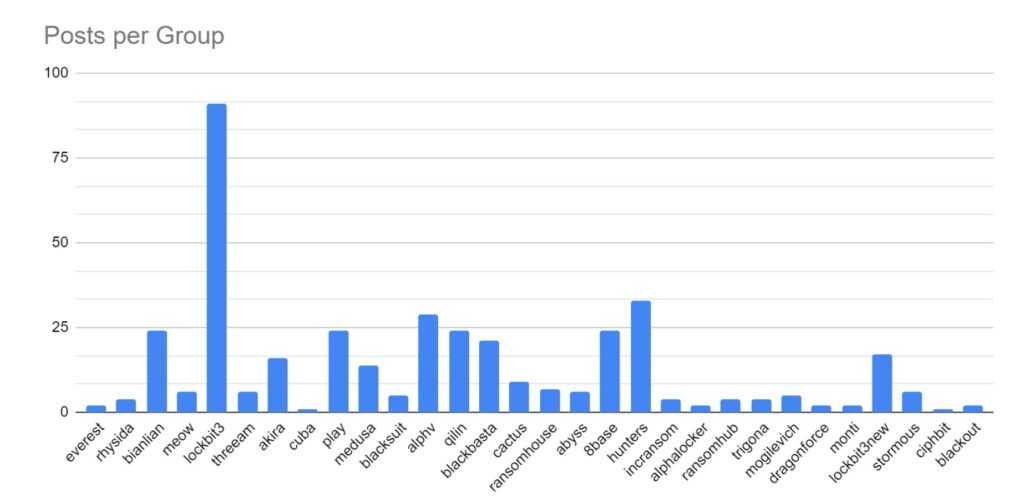
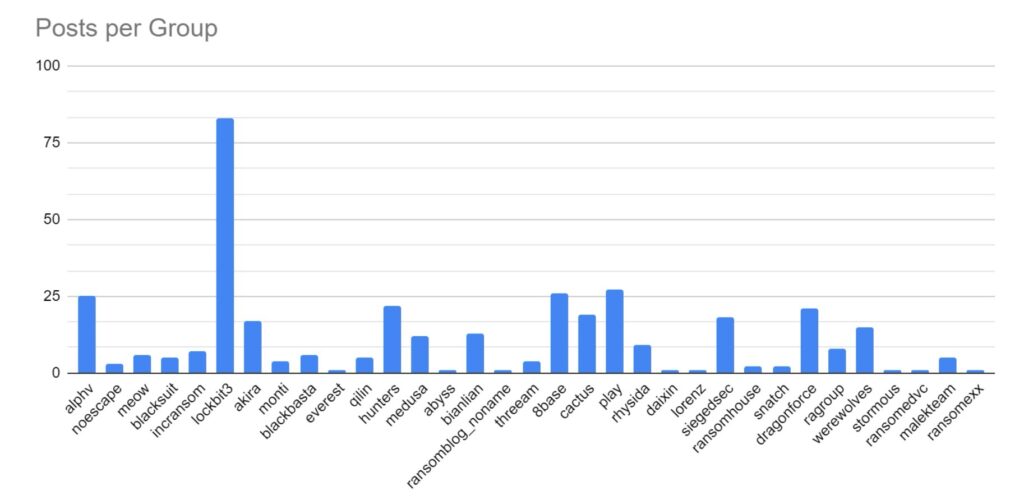
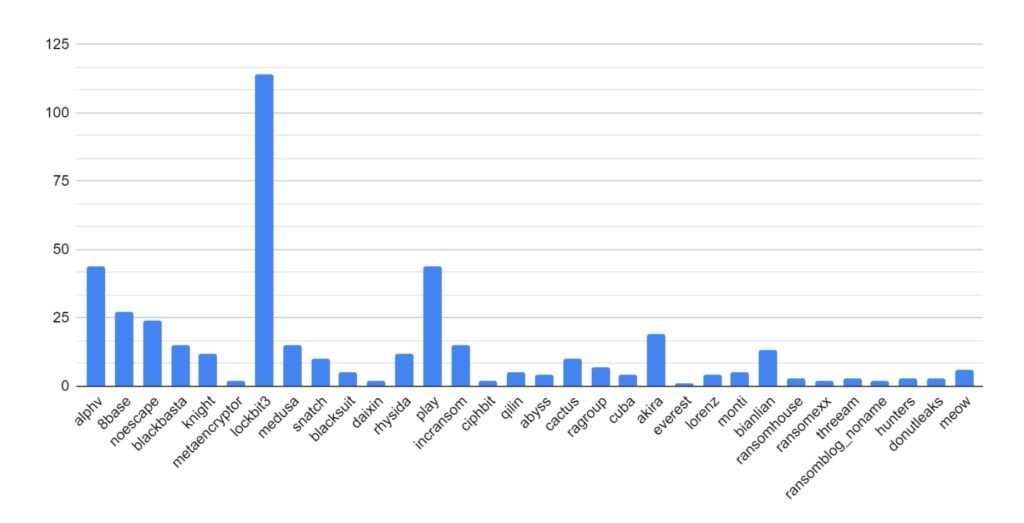
Ransomware activity showed a 20% decrease in June when compared to the previous month, but a 10% increase in activity when compared to the previous year. Furthermore, the number of active groups has decreased to 34 from 37 the previous month.
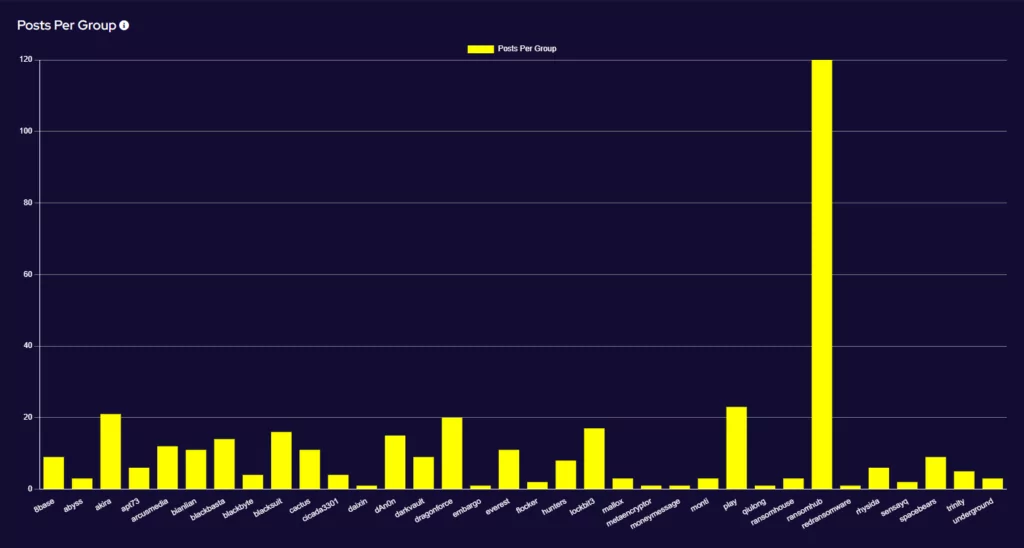
This month has seen a significant increase in activity from Ransomhub, making a significant charge to fill the void left by LockBit. Data for this strain may be skewed, however, by the group using multiple data leak sites to advertise and disseminate stolen data.
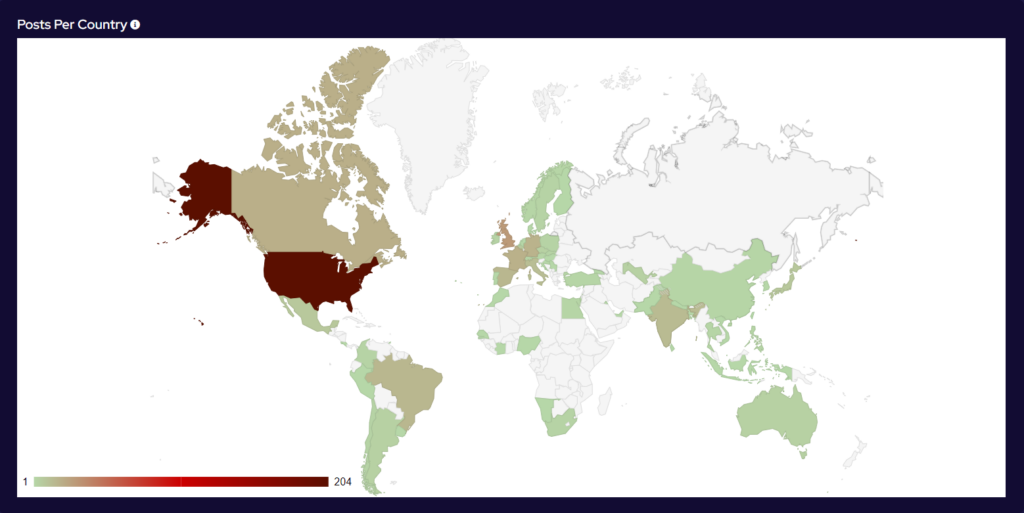
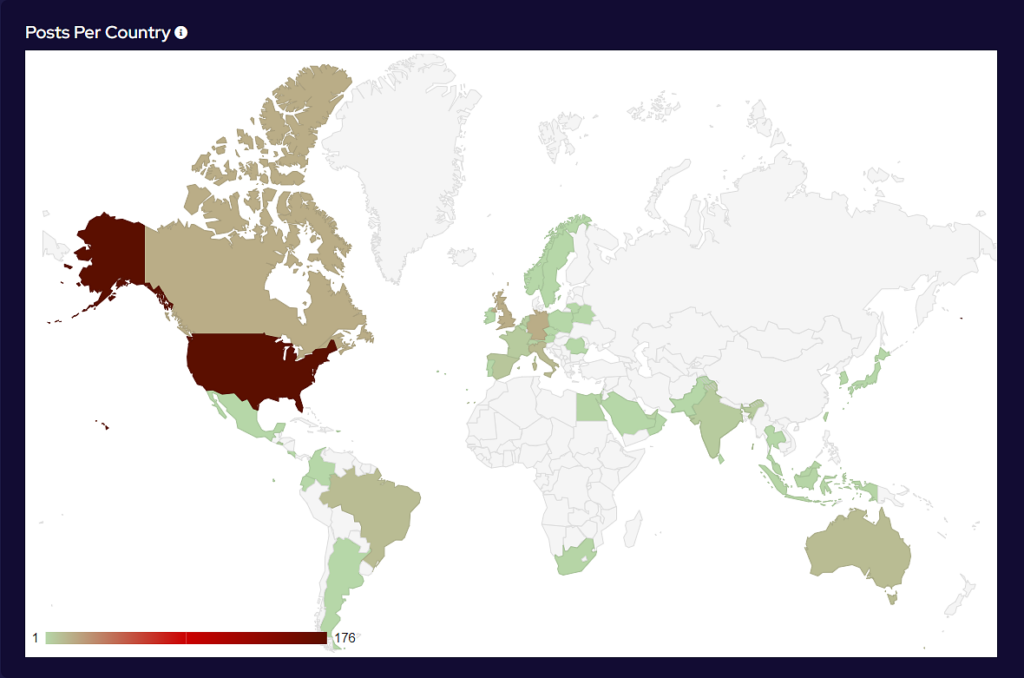
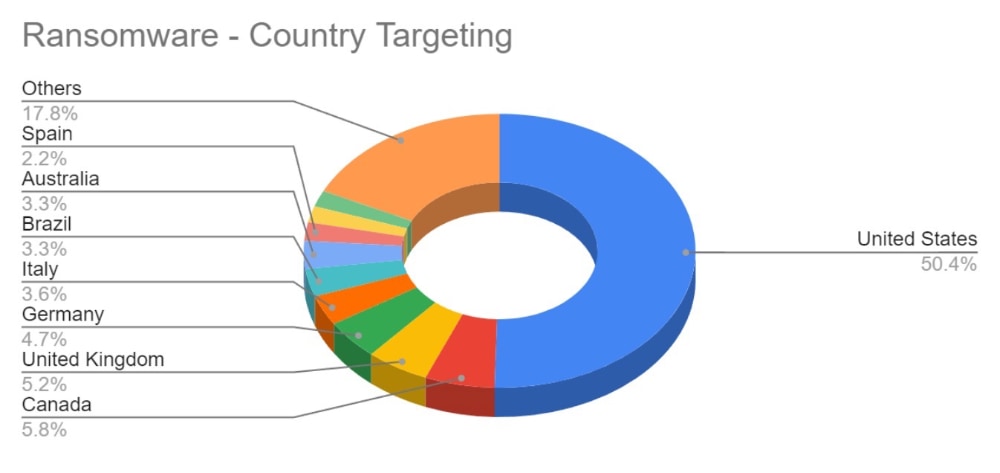
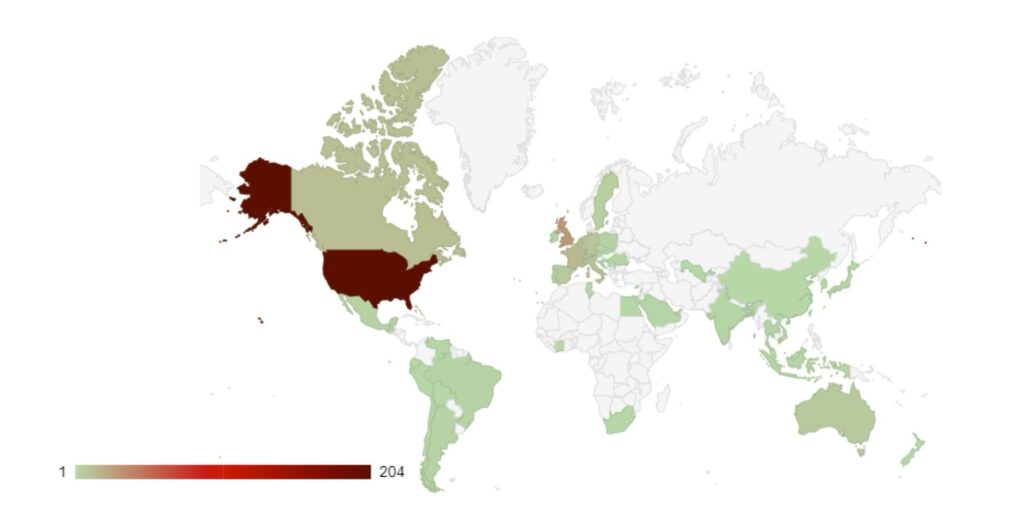
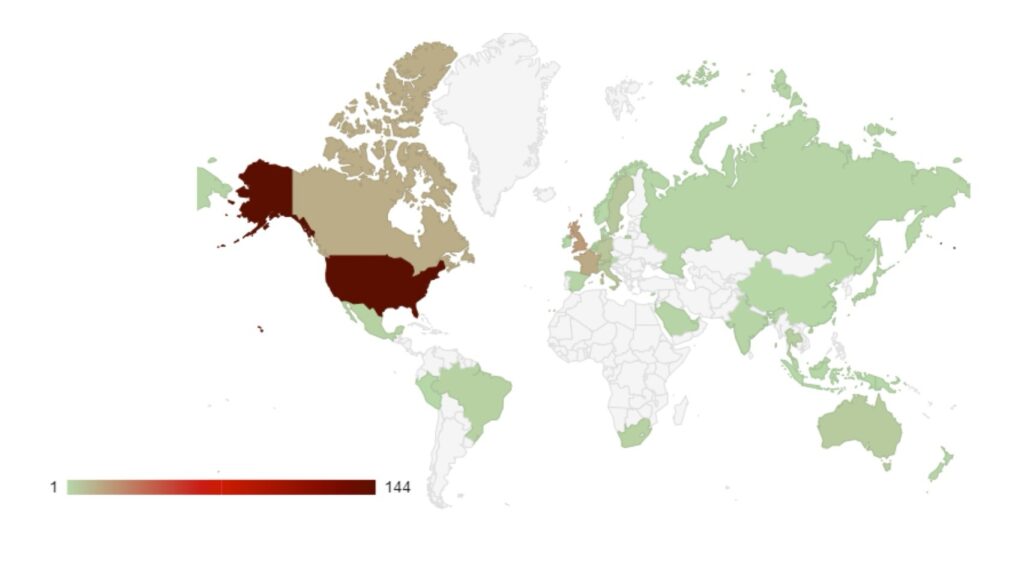
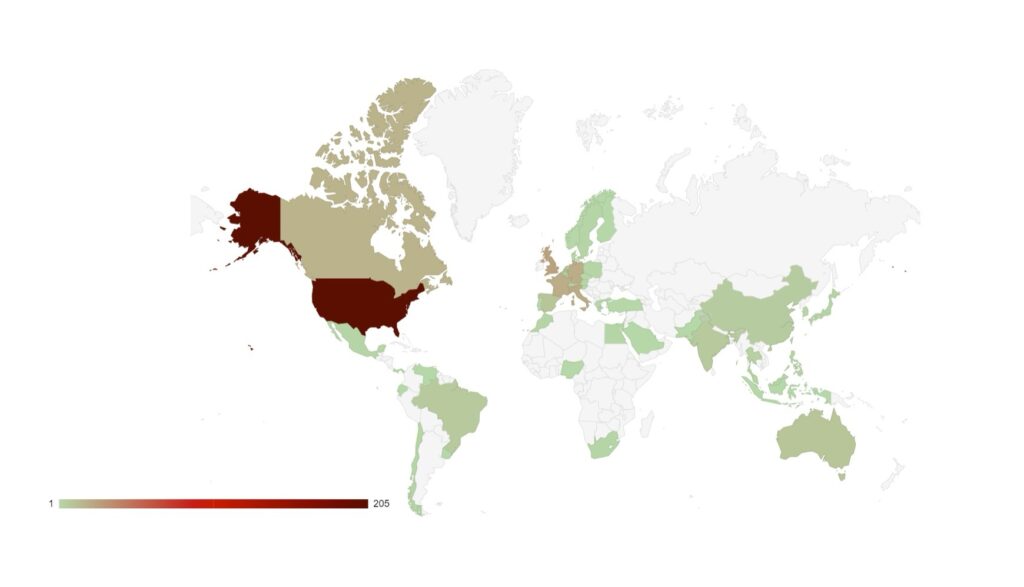
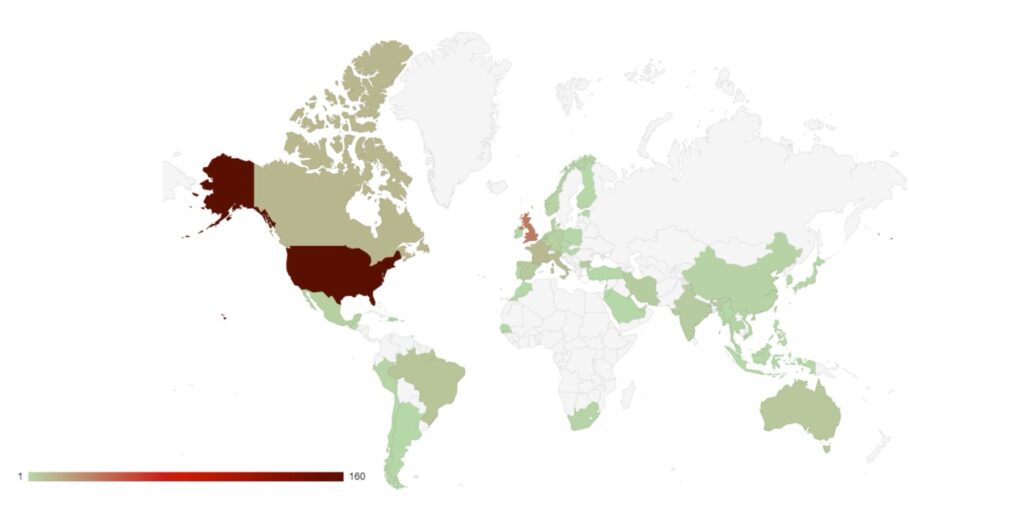
Analysis of Geographic Targeting
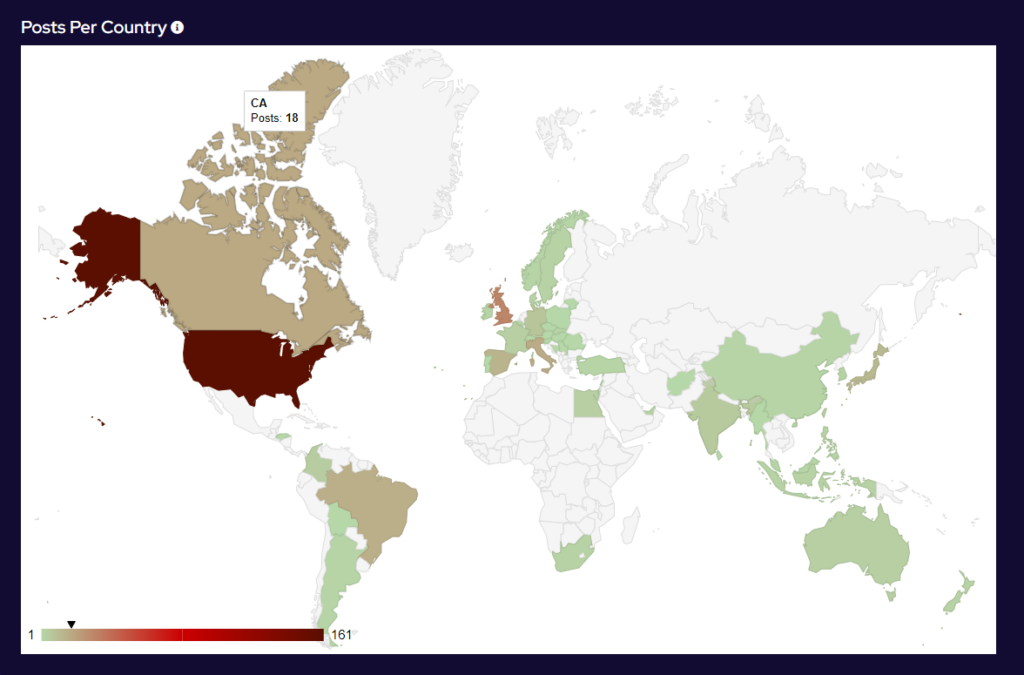
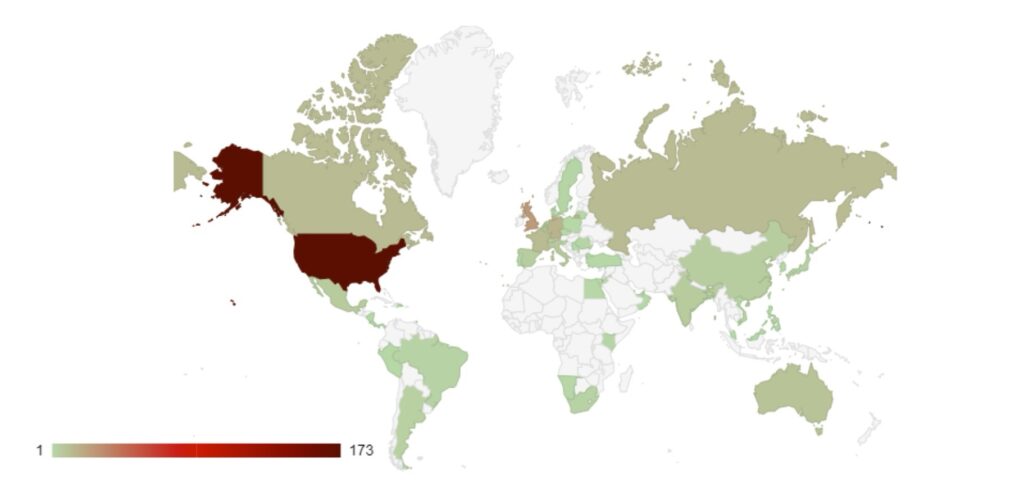
Over the last month, the percentage volume of attacks against the US dropped by 7%. Targeting continues to follow financial lines, with the majority of remaining attacks targeted at G7 and BRICS bloc countries.
Compared to May, 22% fewer countries were targeted in June. Our data is also showing interesting geographic targeting data. We have observed emerging or developing strains targeting developing countries in Southeast Asia, Africa and South America, whereas more established variants focus more on North America, Western Europe and Australia.
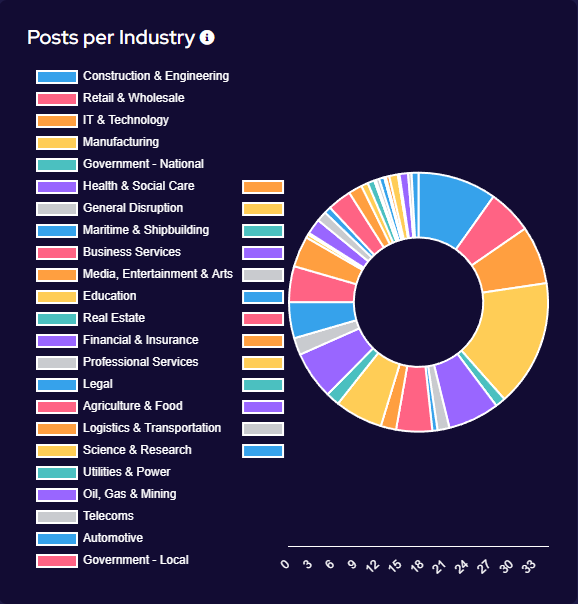
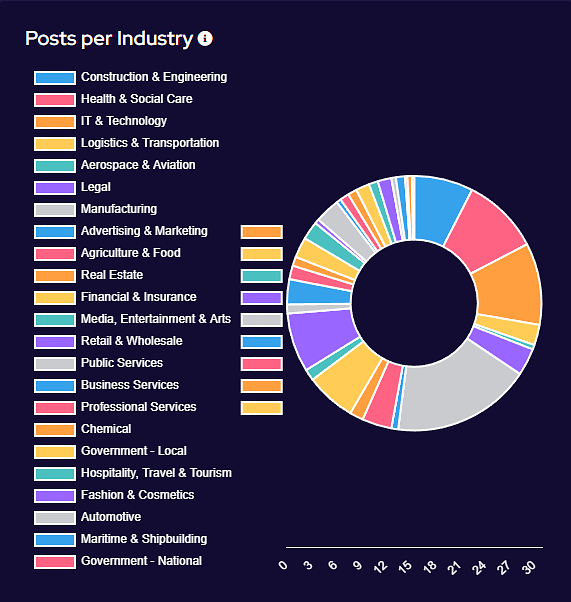
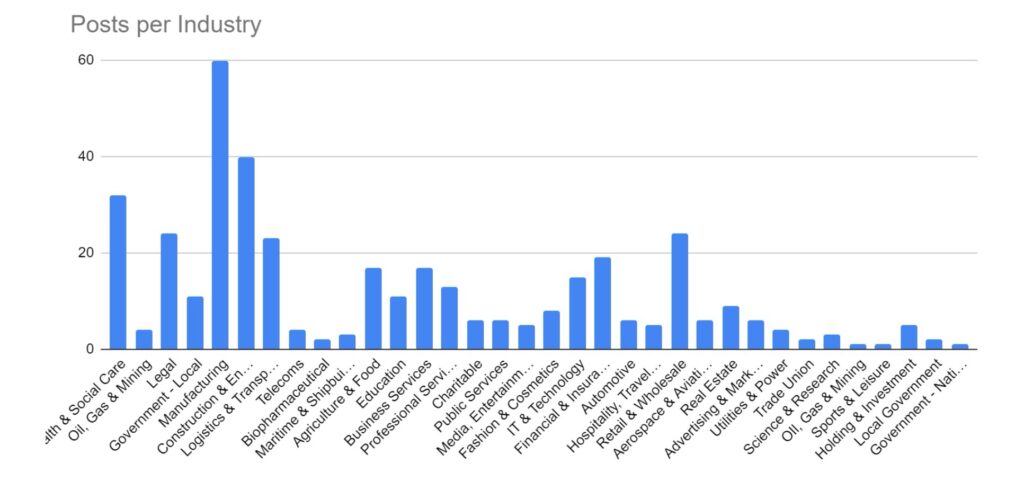
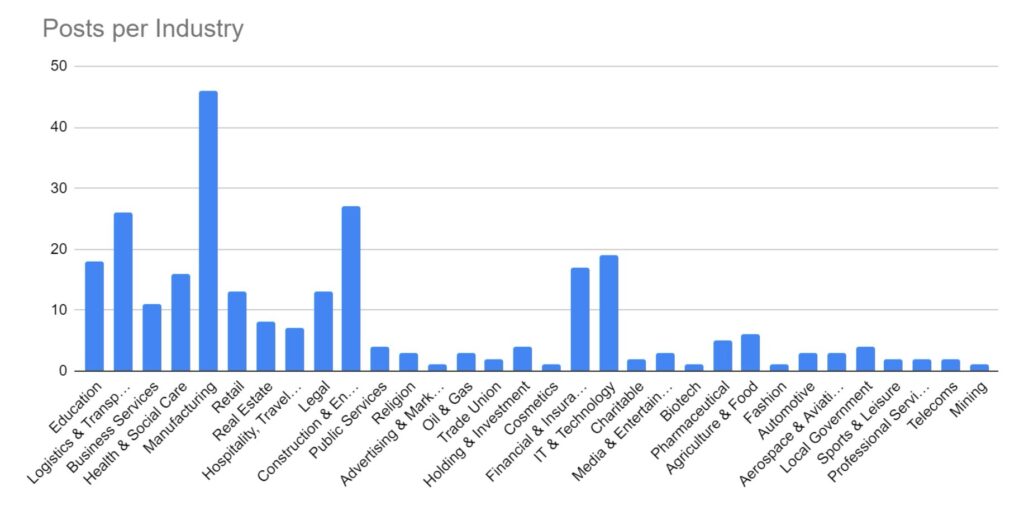
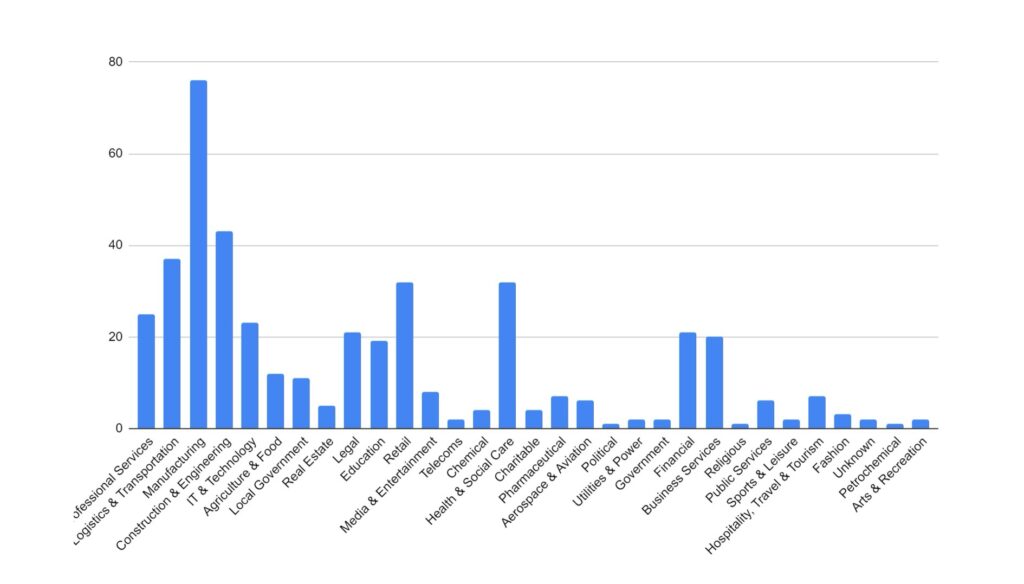
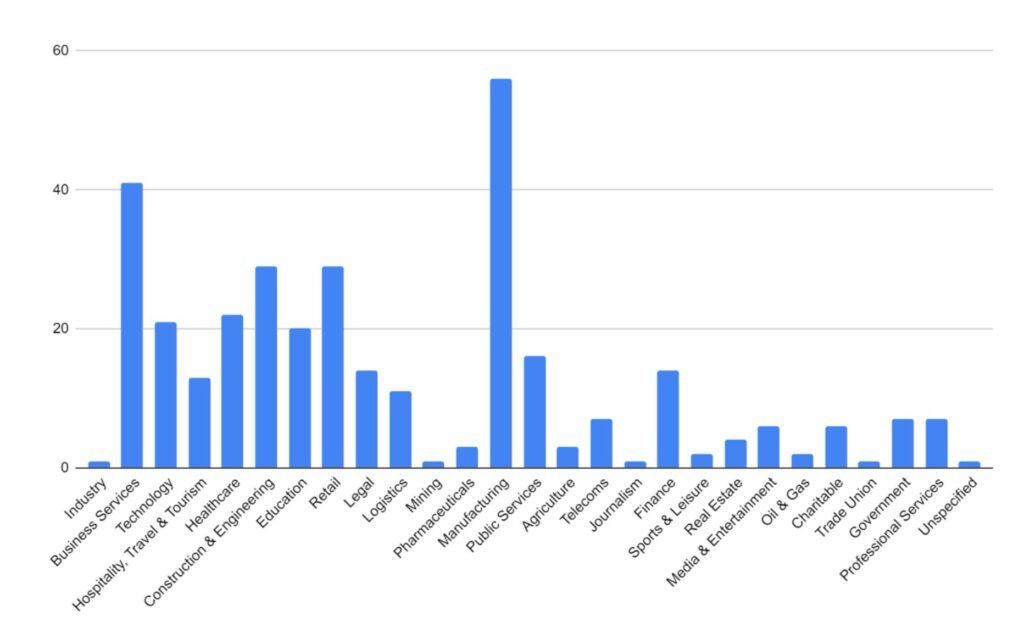
Industry Targeting
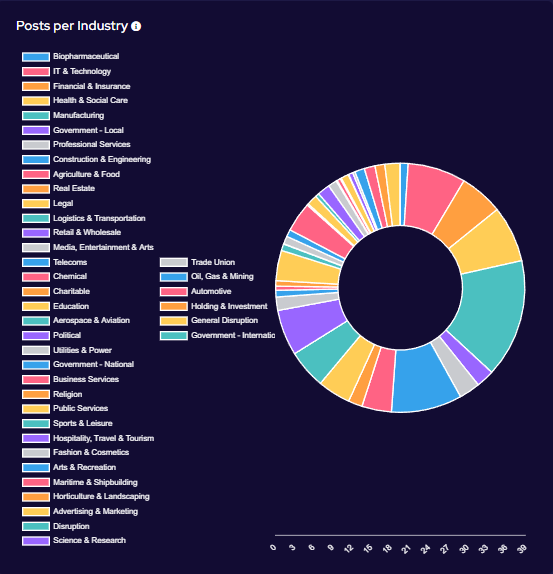
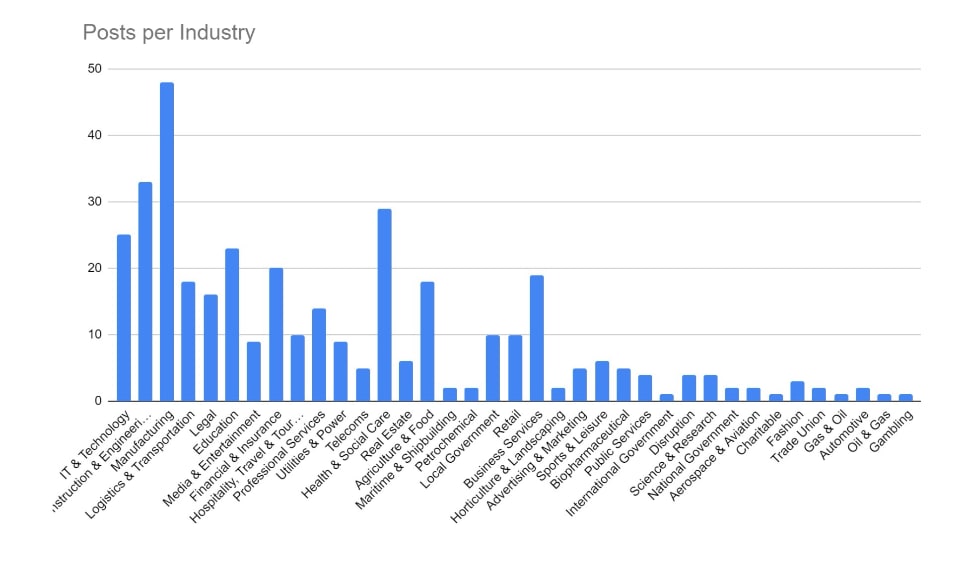
Targeting has broadly increased across all victim sectors, however significant increases have been seen in the Manufacturing, Construction & Engineering and IT & Technology industries.
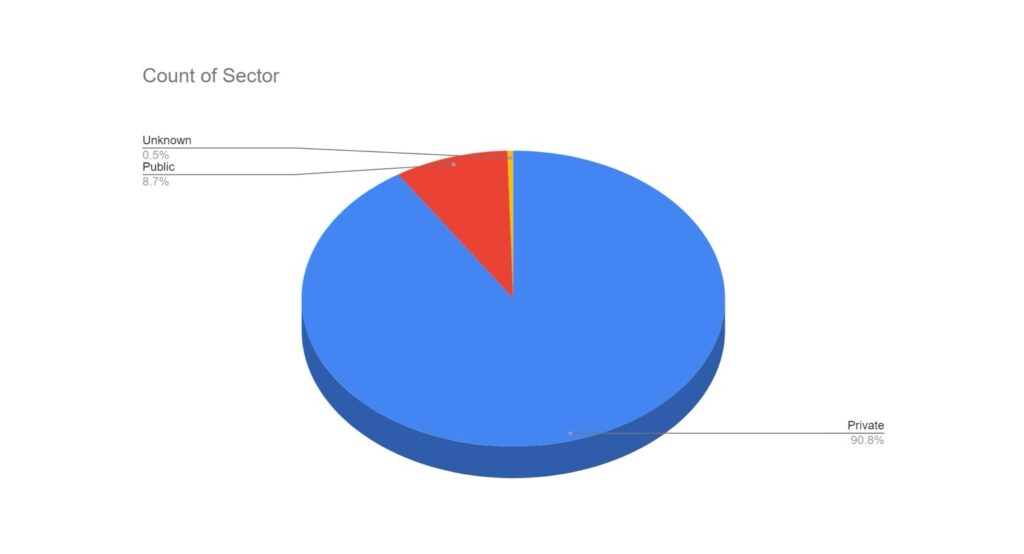
Notably, there appears to have been increased targeting against public-sector entities. This is likely a result of many groups abandoning their affiliate rules on targeting of such victims.
Significant Events
Australian Mining Company Reports Breach
Northern Minerals, an Australian rare earth exploration firm, reported a security breach where data was stolen and later appeared on the dark web. The stolen information includes corporate, operational, and financial data, as well as details about personnel and shareholders. The company informed authorities and affected individuals. Despite the breach, its mining operations continue uninterrupted. The BianLian ransomware group claimed responsibility and published the data after Northern Minerals refused to pay the ransom.
Black Basta Hits Keytronic
Keytronic, a leading PCBA manufacturer, suffered a major data breach due to the Black Basta ransomware gang. The attack halted operations in the U.S. and Mexico for two weeks. Black Basta leaked 530GB of stolen data, including personal and corporate information. In an SEC filing, Keytronic reported that the breach would significantly impact their fourth-quarter financials, with expenses of around $600,000 for external cybersecurity services. The company is notifying affected parties and regulatory agencies as required by law.
Conti and LockBit Ransomware Specialist Arrested
Ukrainian cyber police have apprehended a 28-year-old Russian in Kyiv for assisting Conti and LockBit ransomware groups. The individual specialized in making their malware undetectable and also carried out a ransomware attack himself. The arrest, part of ‘Operation Endgame,’ was the result of a Dutch police investigation. The suspect could face up to 15 years in prison.
Qilin Targets Healthcare Sector
A ransomware attack by the Qilin group disrupted multiple London hospitals by targeting Synnovis (formerly Viapath). This affected operations at Guy’s and St Thomas’ NHS Foundation Trust and King’s College Hospital NHS Foundation Trust. Over 800 surgeries and 700 appointments had to be rescheduled, with IT system recovery expected to take months. The attack caused shortages in blood supplies, especially O-positive and O-negative types, prompting urgent donation appeals from NHS Blood and Transplant.
Ransomhub Makes Headlines
British auction house Christie’s faced a data breach by the RansomHub ransomware group, resulting in the theft of sensitive client information. Christie’s quickly secured their network, enlisted external cybersecurity experts, and notified law enforcement. The breach affected potentially 500,000 clients. Christie’s is offering a free twelve-month subscription to an identity theft and fraud monitoring service for those impacted. RansomHub, known for its data-theft extortion methods, claimed responsibility and announced the sale of the stolen data on their dark web auction platform.
New & Emerging Groups
El Dorado Ransomware
In mid-June 2024, researchers identified a new ransomware group named El Dorado. This variant, derived from the LostTrust ransomware, encrypts files and appends the “.00000001” extension to filenames. It also generates a ransom note titled “HOW_RETURN_YOUR_DATA.TXT.”
Cicada3301
Cicada3301 has recently emerged as a significant cyber threat, targeting organizations worldwide. Known for their sophisticated attack methods, they have been involved in several high-profile ransomware attacks. Their operations typically involve detailed reconnaissance and exploiting network vulnerabilities, especially those neglected in IT security protocols. As of this report, the group has listed four victims, with all the companies’ data leaked on their site.
SenSayQ
SenSayQ is a new ransomware actor recently observed in the threat landscape. While their exact methods remain unclear, they are known to use double-extortion tactics, involving both data exfiltration and file encryption. SenSayQ utilizes a variant of LockBit ransomware, leaving ransom notes in most folders. Currently, the group has two victims listed on its leak site.
Trinity
Trinity is a newly identified ransomware variant, believed to be an updated version of “2023Lock.” This malware encrypts files and appends the “.trinitylock” extension. Trinity shares some of its code with another variant known as Venus. The threat actors behind Trinity use double extortion techniques, exfiltrating confidential files and threatening to release them publicly if their demands are not met. By mid-June, the group listed five victims, but this was later reduced to three, suggesting possible ransom payments or data sales to third parties.
VULNERABILITIES EXPLOITED IN JUNE 2024 BY RANSOMWARE GROUPS
| CVE | CVSS | Vulnerability Name | Associated Threat actor |
| CVE-2024-4577 | 9.8 | PHP-CGI OS Command Injection Vulnerability | TellYouThePass ransomware |
| CVE-2024-26169 | 7.8 | Microsoft Windows Error Reporting Service Improper Privilege Management Vulnerability | Blackbasta |







Recent Comments