19 – 25 August 2024
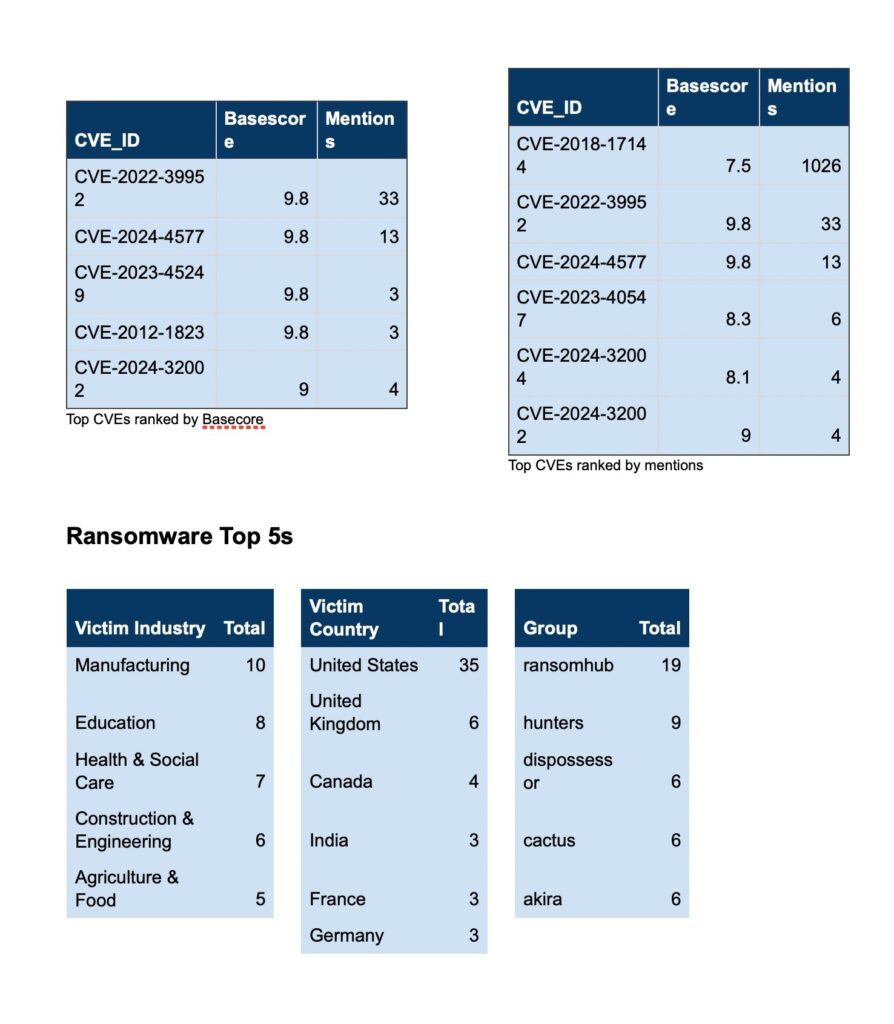
CVE Discussion
Over the past week, we’ve monitored our vast collection of new data to identify discussions of CVEs.
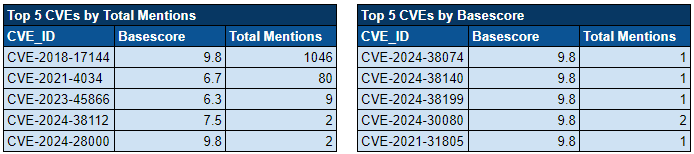
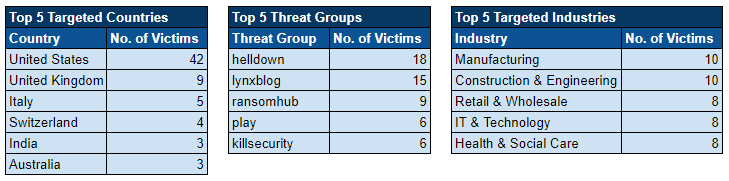
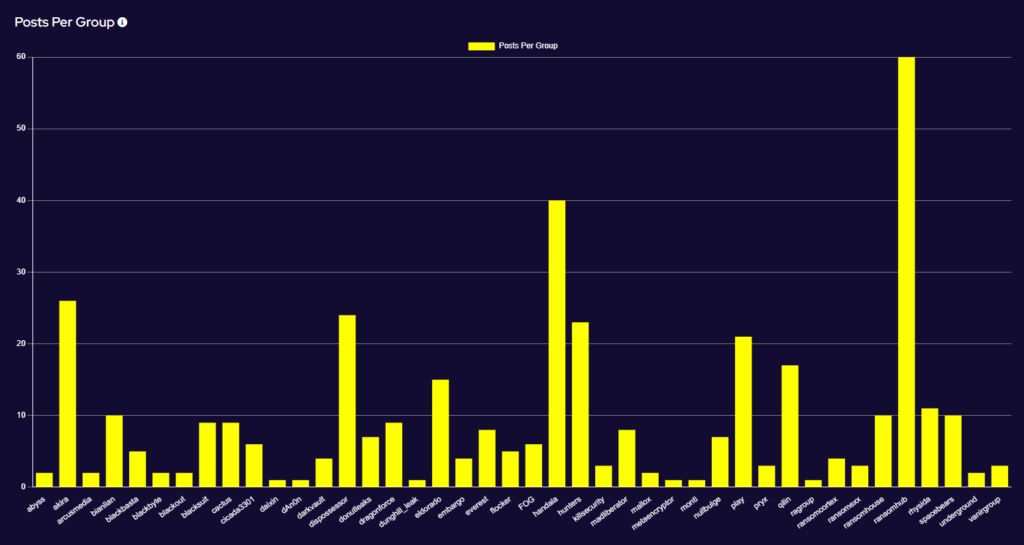
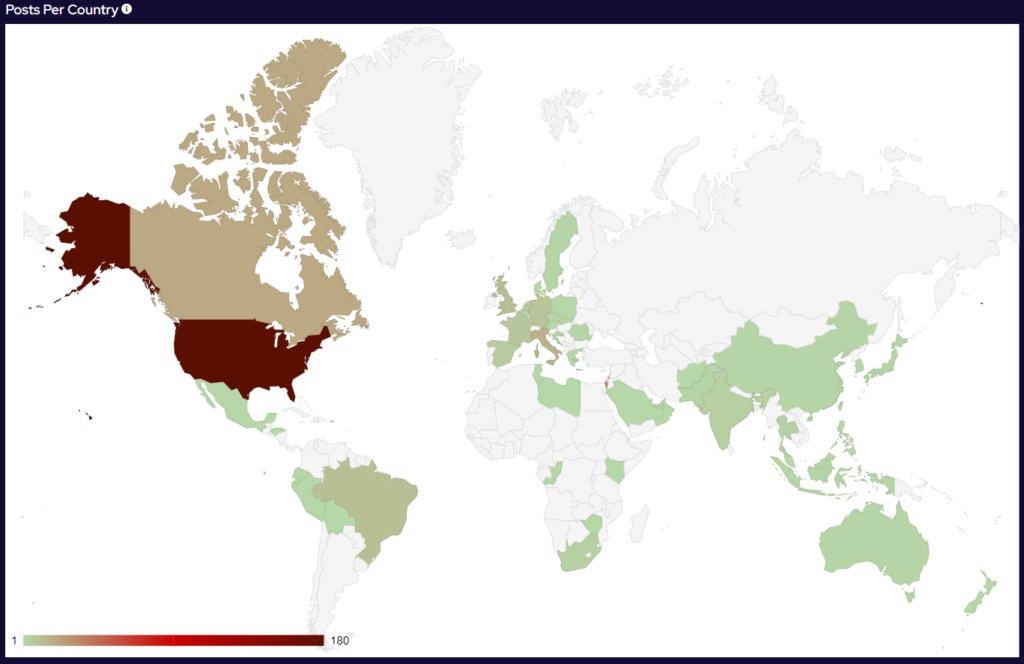
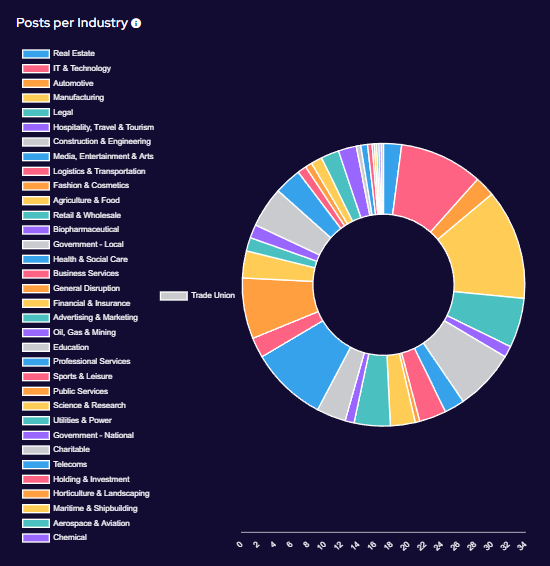
Ransomware Top 5s
News Roundup
Emergence of New Stealer Malware: QWERTY & Styx
A new strain of malware, named “QWERTY Info Stealer,” has been identified as a significant threat to Windows systems, utilising advanced anti-debugging techniques and data exfiltration capabilities. Hosted on the domain mailservicess[.]com, the malware is designed to evade detection, making it particularly dangerous for both individuals and organisations. Discovered on a Linux-based server in Frankfurt, Germany, the malware is distributed via the URL hxxps://mailservicess[.]com/res/data/i.exe.
QWERTY Info Stealer employs multiple anti-debugging strategies, such as using Windows API functions like IsProcessorFeaturePresent() and IsDebuggerPresent(), and the lesser-known __CheckForDebuggerJustMyCode function. These techniques enable the malware to terminate if it detects a debugging environment, complicating efforts by security researchers to analyse its behaviour. After bypassing these checks, the malware begins collecting data, including system information and browser data, which it stores in specific directories on the infected system. It then communicates with Command and Control (C2) servers, downloading additional payloads and exfiltrating data using HTTP POST requests, underlining its sophistication and the ongoing threat it poses to cybersecurity.
Cybersecurity researchers at Check Point have uncovered a new malware strain called “Styx Stealer,” designed to steal browser and instant messenger data. Emerging in April 2024 and based on the Phemedrone Stealer, Styx Stealer enhances its predecessor’s capabilities with features like crypto-clipping, real-time clipboard monitoring, and auto-start functionality. It targets Chromium and Gecko-based browsers to extract sensitive information such as passwords, cookies, and cryptocurrency wallet data, while also compromising Telegram and Discord sessions. The malware resists analysis by antivirus programs and sandboxes, making it a formidable tool for cybercriminals.
Styx Stealer was developed by a Turkish hacker known as “Sty1x,” who marketed it via Telegram, charging between $75 per month and $350 for unlimited access. An operational security lapse exposed his identity and connections with a Nigerian cybercriminal linked to an Agent Tesla campaign. This revelation highlighted the broader network of cybercriminals involved in various illicit activities, including targeting Chinese firms. Despite Sty1x’s efforts, there are no confirmed victims beyond their own systems and a few security sandboxes, suggesting that their attempts to widely distribute Styx Stealer were largely unsuccessful.
New Phishing Attack Targets Android & iOS Users
A new phishing attack targeting both Android and iOS users has been discovered, combining traditional social engineering techniques with the use of Progressive Web Applications (PWAs) and WebAPKs. First identified in November 2023, the attack primarily targets clients of Czech banks, though cases have also been reported in Hungary and Georgia, indicating a wider spread. The attackers employ various delivery methods, such as automated voice calls, SMS messages, and social media ads, which often use official bank mascots and logos to lure victims to a phishing link mimicking a Google Play page. If accessed via a mobile device, the page prompts the installation of a phishing app disguised as a legitimate banking application.
This phishing app, installed as a PWA or WebAPK, is almost indistinguishable from the real banking app, leading victims to a fake login page that captures their banking credentials. The stolen information is then transmitted to the attackers’ Command and Control (C&C) servers, which are operated by two distinct groups—one using a Telegram bot for real-time logging, and the other using a traditional C&C server. The attackers have managed to evade detection by frequently changing domains and launching new campaigns. To mitigate the risk, users should be cautious when installing apps, verify the authenticity of downloads, and keep their devices updated with the latest security patches.
Linux Kernel Vulnerability
Researchers have identified a vulnerability in the Linux kernel’s dmam_free_coherent() function, caused by a race condition during the process of freeing DMA (Direct Memory Access) allocations and managing associated resources. This flaw can lead to system instabilities, as DMA is essential for allowing hardware devices to transfer data directly to and from system memory without CPU involvement. The vulnerability arises from an improper order of operations within the function, which could result in incorrect memory access, data corruption, or system crashes.
The vulnerability is particularly concerning because an attacker could exploit the race condition by timing their operations to coincide with the freeing and reallocation of DMA memory. If successful, this could cause the devres_destroy function to free the wrong memory entry, triggering a WARN_ON assertion in the dmam_match function, which is part of the DMA management subsystem. This issue occurs when a concurrent task allocates memory with the same virtual address before the original entry is removed from the tracking list, potentially leading to significant system errors.
To address this vulnerability, Greg Kroah-Hartman committed a patch (CVE-2024-43856) authored by Lance Richardson from Google, which modifies the dmam_free_coherent function. The patch swaps the order of the function calls, ensuring that the tracking data structure is destroyed before the DMA allocation is freed, thereby preventing the race condition. The patch has been tested on Google’s internal network encryption project and has been approved for inclusion in the mainline Linux kernel, mitigating the risk associated with this vulnerability. Exploiting this vulnerability to achieve arbitrary code execution would be complex and would likely require additional vulnerabilities or precise control over the target system.
Zero-day Vulnerability in Google Chrome
Google recently patched a high-severity zero-day vulnerability in its Chrome browser, CVE-2024-7971. This flaw, found in the V8 JavaScript engine, is a type confusion issue that can be exploited to execute arbitrary code. The vulnerability was reported by the Microsoft Threat Intelligence Center (MSTIC) and the Microsoft Security Response Center (MSRC) on August 19, 2024, and it is actively being exploited in the wild. In response, Google quickly released updates to mitigate the risk, urging users to update their browsers to the latest version.
The latest Chrome update, version 128.0.6613.84/.85, addresses a total of 38 security vulnerabilities, including several high-severity issues. Among these are CVE-2024-7964, a use-after-free vulnerability in the Passwords component; CVE-2024-7965, an inappropriate implementation in the V8 engine; and CVE-2024-7966, an out-of-bounds memory access flaw in the Skia graphics library. Each of these vulnerabilities could allow attackers to execute arbitrary code, leading to serious security breaches or system compromises.
Users are strongly advised to update to the latest version of Google Chrome to ensure protection against these vulnerabilities. While Chrome generally updates automatically, users can manually check for updates via Settings > About Chrome. Additionally, those using Chromium-based browsers such as Microsoft Edge, Brave, Opera, and Vivaldi should also apply the latest security updates as they become available. This patch highlights the need for vigilance and prompt action in the face of zero-day exploits in widely used software.
Chinese Hackers Exploiting Cisco Zero-day
A sophisticated cyber espionage group known as Velvet Ant, linked to China, has been found exploiting a zero-day vulnerability in Cisco NX-OS Software to deploy custom malware on network switches. The vulnerability, identified as CVE-2024-20399, was discovered by cybersecurity firm Sygnia during a forensic investigation and promptly reported to Cisco. This flaw, with a CVSS score of 6.0, allows an authenticated local attacker with administrative privileges to execute arbitrary commands as root on the affected devices due to insufficient validation of arguments passed to specific CLI commands.
Velvet Ant exploited this vulnerability to install a custom malware, dubbed VELVETSHELL, on compromised Cisco Nexus devices. The malware, which combines elements of the TinyShell Unix backdoor and the 3proxy tool, enables attackers to execute arbitrary commands, upload and download files, and create tunnels to proxy network traffic. Sygnia’s investigation revealed that Velvet Ant has been operating for approximately three years, targeting inadequately protected network appliances like outdated F5 BIG-IP systems to maintain long-term access and steal sensitive information.
Cisco has released software updates to patch the vulnerability and strongly advises customers to apply these updates immediately. Experts warn that network appliances, especially switches, are often under-monitored, with logs rarely forwarded to centralized logging systems, making it difficult to detect and investigate such malicious activities. To mitigate this threat, organizations are urged to apply Cisco’s updates, enhance monitoring of network appliances, regularly update administrator credentials, and adopt stringent security practices to prevent unauthorized access.





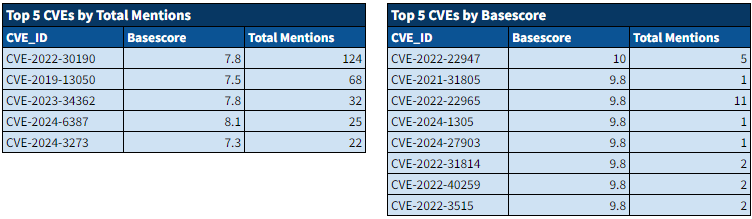
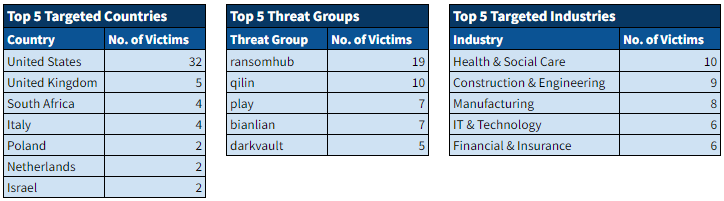




Recent Comments