09 – 15 September 2024
CVE Discussion and Exploitation
Over the past week, we’ve monitored our vast collection of new data to identify discussions of CVEs.
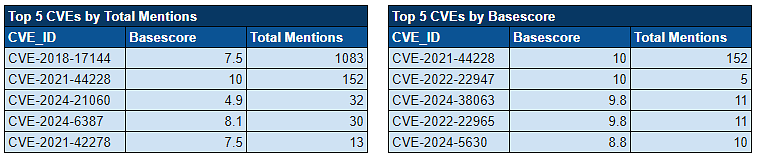
Noteworthy Exploitation of New CVEs by Threat Actors:
- Cisco ASA SSL VPN Vulnerability (CVE-2024-40200): This RCE vulnerability is being exploited by Chinese and Russian state-sponsored APTs to gain unauthorized access to sensitive data transmitted over SSL VPNs. Targets include government agencies and critical infrastructure, particularly in APAC, making it a priority for patching.
- Citrix Gateway RCE Vulnerability (CVE-2024-40321): Exploited by APT29 (Cozy Bear), this flaw allows unauthenticated remote code execution. The group has used it to gain persistent access to enterprise networks in attacks against multinational corporations and financial institutions, underscoring its rapid adoption by espionage actors.
- Sophos XG Firewall Vulnerability (CVE-2024-41107): Iranian-linked threat actors have exploited this to bypass security controls and gain footholds in MENA-region networks. This is part of broader espionage activities targeting government and defense organizations.
- Zimbra Collaboration Suite Vulnerability (CVE-2024-40998): APT28 (Fancy Bear) is actively exploiting this flaw to steal sensitive emails and credentials. Zimbra is widely used by universities and government agencies, making this CVE highly dangerous for academic and public sector institutions.
Key Takeaways:
- Cisco ASA SSL VPN and Citrix Gateway vulnerabilities are seeing heavy exploitation in cyber-espionage campaigns, with state-sponsored actors using these flaws to target critical infrastructure and government agencies.
- Sophos XG Firewalls and Zimbra Collaboration Suite vulnerabilities are being actively exploited by APT groups, focusing on data theft and long-term persistence within sensitive networks, particularly in the Middle East and academic sectors.
Ransomware Activity
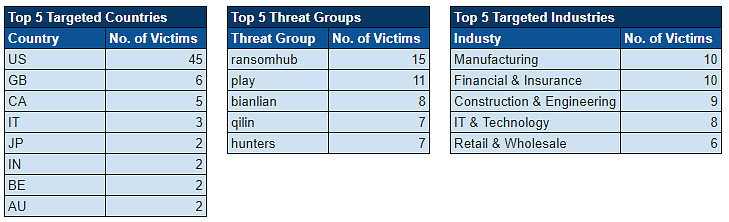
Over the past week, we’ve captured 82 ransomware incidents, affecting victims in 23 countries across 24 industries.
Ransomware Top 5s
Advancements in Ransomware Tactics:
- Advanced EDR Evasion Techniques: Ransomware operators, particularly RansomHub, have been deploying sophisticated tools like Kaspersky’s TDSSKiller to bypass endpoint detection and response (EDR) systems. This reflects the growing use of Bring Your Own Vulnerable Driver (BYOVD) strategies, which are increasingly being employed to disable security measures before deploying ransomware.
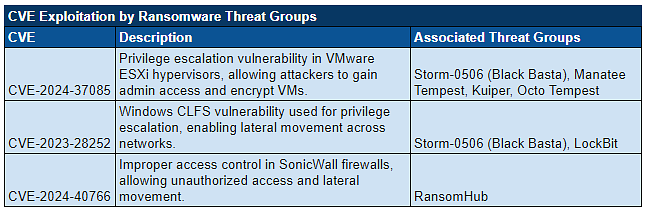
- Targeting Virtualized Infrastructures: Groups such as Storm-0506 and Manatee Tempest have turned their attention toward VMware ESXi hypervisors, exploiting vulnerabilities like CVE-2024-37085. This allows them to rapidly encrypt multiple virtual machines, expanding their attack surface by compromising critical server environments.
Emerging Threat Actors:
- Helldown: A newly surfaced group, Helldown, made its mark by listing 17 victims on its leak site in a short period, indicating it may quickly become a more prominent player. Their focus has been on exploiting unpatched vulnerabilities to target a broad array of victims.
- Manatee Tempest: This relatively new group has been gaining attention for its focused exploitation of ESXi vulnerabilities, joining the ranks of emerging ransomware gangs that prioritize attacks on virtualization technologies.
Key Ransomware Incidents:
- Storm-0506 (Black Basta) Attack on Engineering Firm: Storm-0506 conducted a high-profile attack against a North American engineering firm, exploiting CVE-2023-28252 (a Windows CLFS vulnerability). The group leveraged advanced credential-stealing tools like Cobalt Strike and Pypykatz to compromise administrative accounts and encrypt virtual machines, causing widespread operational disruption.
- Meow Ransomware Group Resurgence: The Meow ransomware group has shifted its focus from Russian targets to U.S. entities, marking a resurgence in its activity. Using Conti’s leaked ransomware code, Meow has been increasingly active, showing adaptability in its targeting strategy and operational methods.
News Roundup
Payment Provider Breach Exposes Credit Card Data
On September 10th, 2024, payment provider Slim CD disclosed a significant data breach affecting 1.7 million users. The breach resulted in the exposure of sensitive credit card information, raising concerns about customer financial security. Slim CD reported the breach promptly, triggering investigations into how the attackers were able to bypass existing defences. The company is urging affected customers to monitor their financial statements closely for any suspicious activity and is working with cybersecurity experts to fortify its systems.
Meta Scrapes User Data to Train AI
On September 12th, 2024, Meta (formerly Facebook) admitted to scraping user data, including images and posts, from Australian profiles to train its AI models. Worryingly, this data collection also included content from minors featured on adult profiles, prompting privacy concerns. Australian regulators and privacy advocates have voiced concerns about the scope of Meta’s data-gathering efforts and the lack of transparency. The incident has reignited debates on data privacy and the ethical use of personal information in AI training.
RansomHub: A New Threat in Ransomware
US authorities issued a joint advisory on the growing threat of RansomHub, a ransomware-as-a-service group that has gained prominence throughout 2024. Formerly known as Cyclops and Knight, the group has attacked over 200 organisations since February 2024, targeting critical sectors such as water, manufacturing, and government services. Authorities recommend organisations implement multi-factor authentication and enhance phishing detection to defend against this rapidly evolving threat.
Zero-Day Vulnerabilities in Ivanti EPM
On September 11th, 2024, researchers revealed that critical vulnerabilities in Ivanti Endpoint Manager (EPM) were being actively exploited in the wild. These zero-day flaws, rated CVSS 10, allow remote attackers to take full control of affected systems. Ivanti has urged organisations to apply patches immediately to mitigate the risk of exploitation. The vulnerabilities have been leveraged by both criminal groups and nation-state actors, targeting critical industries such as healthcare, government, and energy.
AppleCare+ Scam Exposed
A new scam surfaced on September 13th, 2024, where attackers used GitHub repositories to create fake AppleCare+ websites, tricking users into providing personal and financial information. The scam involved impersonating legitimate Apple services, offering fraudulent tech support and extended warranties. Security experts warn that this technique, leveraging trusted platforms like GitHub, represents an evolution in phishing tactics. Users are advised to verify the legitimacy of any unsolicited AppleCare+ communications and avoid clicking on suspicious links.

