29 July – 4 August 2024
CVE Discussion
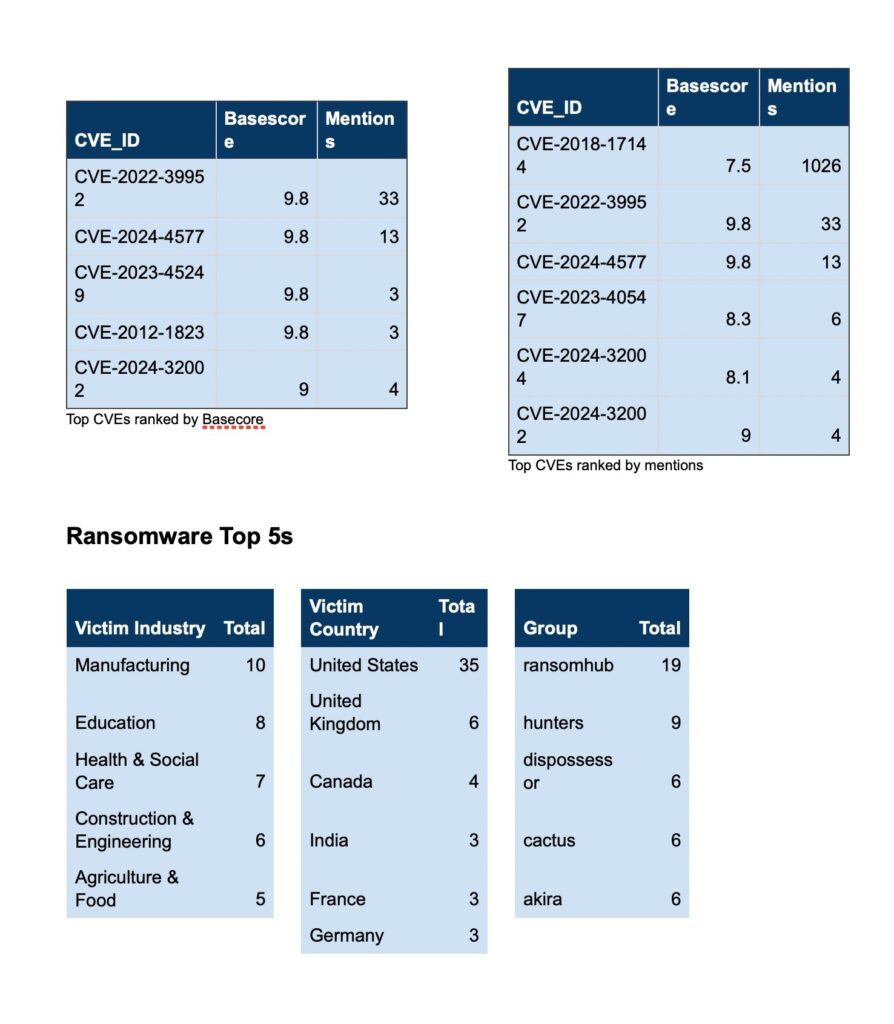
Over the past week, we’ve monitored our vast collection of new data to identify discussions of CVEs.
News Roundup
Linux Servers Exposed to Data Exfiltration from TgRat
The TgRat trojan, first discovered in 2022, is now targeting Linux servers to steal data. Controlled via a private Telegram group, it can download files, take screenshots, execute commands remotely, and upload files. TgRat verifies the computer name’s hash upon startup and establishes a network connection if it matches, using Telegram to communicate with its control server.
Due to Telegram’s popularity and the anonymity it provides, TgRat’s use of it as a control mechanism makes detection difficult. It executes commands via the bash interpreter, encrypted with RSA, and manages multiple bots using unique IDs.
This unique control mechanism complicates detection, as typical network traffic to Telegram servers can mask malicious activity. Installing antivirus software on all local network nodes is recommended to prevent infection.
Threat Actors Using Fake Authenticator Sites to Deliver Malware
Researchers from ANY RUN identified a malware campaign called DeerStealer, which uses fake websites mimicking legitimate Google Authenticator download pages to deceive users. The primary site, “authentificcatorgoolglte[.]com,” looks similar to the genuine Google page to trick users into downloading malware. Clicking the download button on this fake site transmits the visitor’s IP address and country to a Telegram bot and redirects users to a malicious file on GitHub, likely containing DeerStealer, which can steal sensitive data once executed.
The Delphi-based DeerStealer malware employs obfuscation techniques to hide its activities and runs directly in memory without leaving a persistent file. It initiates communication with a Command and Control (C2) server by sending a POST request with the device’s hardware ID to “paradiso4.fun.” Subsequent POST requests suggest data exfiltration.
Analysis revealed the use of single-byte XOR encryption for transmitted data, uncovering PKZip archives containing system information. Researchers also linked DeerStealer to the XFiles malware family, noting that both use fake software sites for distribution but differ in their communication methods.
Threat Actors Abusing TryCloudflare to Deliver Malware
Cybercriminals are increasingly using TryCloudflare Tunnel to deliver Remote Access Trojans (RATs) like Xworm, AsyncRAT, VenomRAT, GuLoader, and Remcos in financially motivated attacks. TryCloudflare allows developers to experiment with Cloudflare Tunnel without adding a site to Cloudflare’s DNS, which attackers exploit to create temporary infrastructures that bypass traditional security controls.
This tactic, initiated in February 2024, has intensified, posing a significant threat due to its rapid deployment and evasion capabilities. Recent campaigns often use URL links or attachments to download malicious files, which execute scripts to install RATs and other malware.
Campaigns frequently target global organisations, using high-volume email campaigns with lures in multiple languages, often exceeding the volume of other malware campaigns. Attackers dynamically adapt their attack chains and obfuscate scripts to evade defences, demonstrating a sophisticated and persistent threat.
By abusing TryCloudflare tunnels, attackers generate random subdomains on trycloudflare.com, routing traffic through Cloudflare to avoid detection. For example, on May 28, 2024, and July 11, 2024, targeted campaigns used tax-themed lures and order invoice themes, respectively, to deliver AsyncRAT and Xworm via malicious email attachments and PowerShell scripts, providing remote system access and data exfiltration capabilities.
Ransomware Threat Actors Exploiting VMWare ESXi
Microsoft researchers have identified a critical vulnerability in VMware’s ESXi hypervisors, CVE-2024-37085, which allows ransomware operators to gain full administrative permissions on domain-joined ESXi hypervisors. This flaw, associated with the “ESX Admins” group, enables any domain user who can create or rename groups to escalate their privileges, potentially gaining full control over the ESXi hypervisor. Exploiting this vulnerability can result in the encryption of the hypervisor’s file system, access to virtual machines, data exfiltration, and lateral movement within the network.
Ransomware groups such as Storm-0506, Storm-1175, Octo Tempest, and Manatee Tempest have been observed exploiting this vulnerability, deploying ransomware like Akira and Black Basta to encrypt ESXi file systems.
A notable attack by Storm-0506 involved using Qakbot and exploiting a Windows vulnerability to elevate privileges, followed by deploying Black Basta ransomware. In response, VMware has released a security update to address CVE-2024-37085. Microsoft urges organisations to apply this update, validate and secure the “ESX Admins” group, deny access or change administrative group settings, use multifactor authentication for privileged accounts, and secure critical assets with the latest security updates and monitoring procedures.
Photo by Joshua Hoehne on Unsplash

