When conducting online research or gathering open-source intelligence (OSINT), it is often necessary to observe or interact with digital spaces without revealing your true identity. This is where sock puppet accounts come into play. A sock puppet is a fictitious online identity created to access information, join closed groups, monitor activity, or engage with targets while protecting the researcher’s real identity and intent.
Used properly, sock puppets are an essential part of an investigator’s toolkit. However, their creation and use come with both ethical and legal responsibilities. Misuse can lead to legal consequences, reputational damage, or compromised investigations. Practitioners must always follow legal guidance and act within clearly defined ethical boundaries.
In this blog, we will explore how to plan, create, and maintain effective sock puppet accounts for OSINT purposes. We will discuss key operational security (OPSEC) measures, common pitfalls to avoid, and strategies for maintaining a convincing online persona over time. Whether you are new to this practice or looking to refine your approach, this guide will help you lay a solid foundation for safe and responsible online research.

What Is a Sock Puppet Account?
A sock puppet account is a false or alternate online identity used to conceal the true identity of the user behind it. In the context of online investigations and intelligence gathering, sock puppets allow researchers to access and monitor digital spaces without drawing attention to their real-world affiliations or investigative purpose.
These accounts are beneficial in OSINT investigations where anonymity is critical. They may be used to:
- Access private or semi-restricted forums and groups
- Observe conversations on social media without alerting subjects
- Collect threat intelligence from Dark Web marketplaces or closed communities
- Engage with individuals or groups in a way that does not compromise operational security
While sock puppets can be powerful tools, their use must always be underpinned by legal and ethical awareness. Investigators should never use false identities to entrap, manipulate, or harass individuals. The goal is passive information gathering, not interference or provocation. Moreover, laws governing online impersonation, data protection, and computer misuse vary between jurisdictions, and it is the investigator’s responsibility to ensure compliance.
Wherever possible, work within organisational policies, maintain internal approval processes for sensitive research, and document all actions for accountability. Ethical OSINT hinges not only on what can be done, but on what should be done.
Planning Your Sock Puppet Strategy
Before creating a sock puppet account, it is essential to define a clear objective. What do you need the account to do? Your goal might be to passively observe a forum, monitor a social media group, or engage with a specific individual or community. The purpose of the account will shape every decision that follows, from the choice of platform to the construction of your online persona.
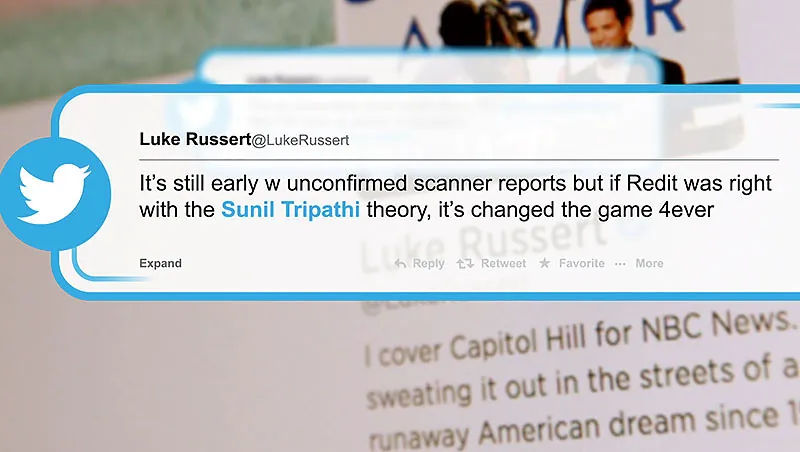
Understanding your target environment is a crucial part of this planning stage. Different platforms have different norms, verification processes, and levels of scrutiny. A persona that appears credible on Reddit might not be believable on LinkedIn. Consider regional factors as well: language, time zone, and cultural references all contribute to the authenticity of an account. An inconsistency in these details can quickly arouse suspicion.
With your objective and environment defined, you can begin to craft a suitable cover story. This should include a basic biography, a plausible location, interests relevant to the communities you plan to interact with, and a consistent tone of voice. Keep the persona simple, but detailed enough to withstand casual scrutiny. Avoid unnecessary complexity, which can increase the risk of contradictions or mistakes.
A well-planned sock puppet starts long before the account is created. By aligning your objectives with your operational context and building a realistic backstory, you lay the groundwork for a credible and sustainable online identity.
Creating the Sock Puppet Account
Once your planning is complete, the next step is to create the sock puppet account itself. This process involves selecting the right platform, crafting a believable identity, and ensuring that your setup maintains strong operational security from the outset.
Choosing the Right Platform
Select your platform based on the objective of the investigation. If you need to observe professional activity or gather company intelligence, LinkedIn might be appropriate. For community discussions, Reddit or Discord may be more useful. For threat intelligence gathering, forums or encrypted messaging apps could be more suitable. Each platform has its own registration process, verification requirements, and user expectations, all of which must be considered.
Crafting a Believable Identity
A convincing sock puppet needs to pass casual inspection. Start with a realistic username and a dedicated email address that fits your persona. Avoid using anything that resembles your real name or any identifiers linked to your organisation.
- Profile photo: Use AI-generated images or copyright-free alternatives. Tools like ThisPersonDoesNotExist or Generated Photos can be helpful, but check for anomalies that might raise suspicion.
- Biography and interests: Write a brief, plausible bio that fits the persona and platform. Add relevant interests or affiliations to make the account appear active and authentic.
- Posting behaviour: Mirror the tone, grammar, and posting frequency typical for the platform and user type. If your persona is a 30-year-old from Manchester, for example, ensure the language and topics reflect that identity.
- Language consistency: Stick to one language and dialect throughout. Switching between different styles or regions can be a clear indicator of inauthenticity.
Acquiring a Clean IP
To prevent your real identity or location from being linked to the sock puppet, use a clean and separate IP address. A reputable VPN or proxy service is essential, and in some cases, a dedicated virtual machine or separate device should be used. Avoid logging in to real accounts or using your usual browser within the same environment, as cross-contamination can compromise the entire operation.
Account creation is not just about filling in a form. Every detail, from your profile picture to your browser setup, contributes to the believability and security of the puppet. Take your time, document each step, and treat the identity as if it were real.

OPSEC Considerations
Operational Security (OPSEC) is critical to the effective use of sock puppet accounts. Without proper precautions, it is easy to leave digital traces that link back to your real identity or organisation. To maintain credibility and protect yourself, you must build strong habits around device use, network hygiene, and identity compartmentalisation.
Device and Network Isolation
Always use a dedicated environment for sock puppet activity. This might be a virtual machine (VM), a separate user profile, or an entirely distinct physical device. The key is to ensure that no personal data, saved credentials, or browsing habits from your real identity carry over into the puppet’s digital footprint. Similarly, connect via a trusted VPN or proxy with a location appropriate to the persona. Never use your home or work IP address when managing sock puppets.
Avoiding Contamination
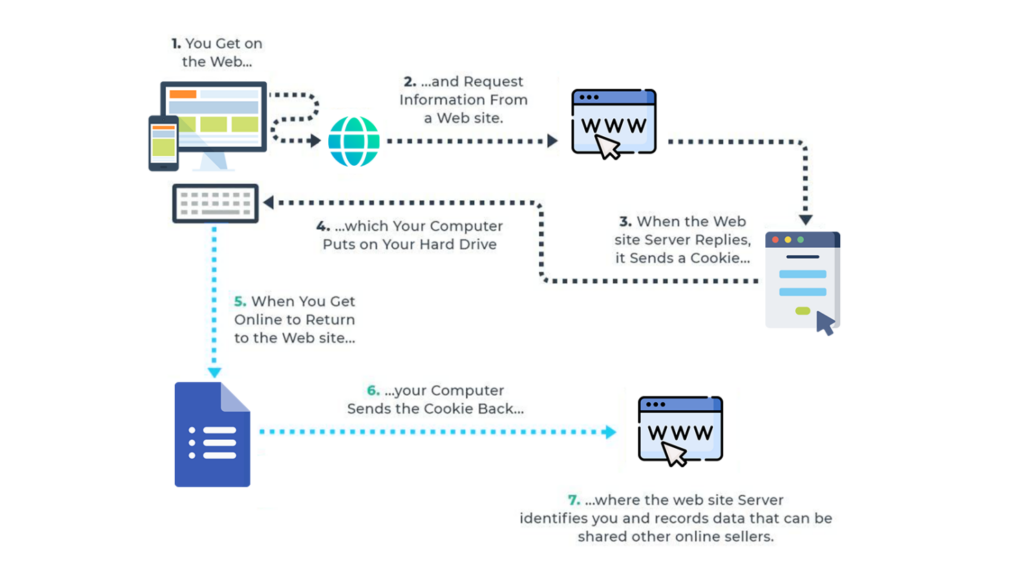
Cross-contamination with real accounts is one of the most common OPSEC failures. Use a clean browser instance with no saved cookies, autofill data, or extensions that may reveal identifying information. Consider using privacy-focused browsers or containerised browsing sessions to isolate activity. Disable features like browser synchronisation or automatic logins, which could leak personal credentials.
Using Burner Phones and Anonymous Email
When platforms require phone numbers for verification, use a burner device or a secure, anonymised SMS service, provided it complies with legal and policy requirements. Similarly, choose privacy-conscious email providers such as ProtonMail or Tutanota. The email address should align with the puppet’s identity and not reference any real-world details.
Password and Account Recovery Separation
Treat sock puppets as standalone entities. Use unique, complex passwords for each account and manage them using a secure password manager. Keep recovery options consistent with the identity—never link your real email or phone number. If using recovery questions, invent answers that match the puppet’s backstory and document them securely.
Logging and Documentation
Maintain secure records of your sock puppets, including account details, access credentials, personas, activity logs, and creation dates. This helps track usage over time, identify potential compromises, and safely retire or rotate identities when needed. Store this information in an encrypted format or within a secure password management tool.
Sock puppet OPSEC is not about one-time precautions—it requires ongoing discipline. A single mistake can expose your identity or compromise the entire investigation. Take a cautious, methodical approach and revisit your OPSEC practices regularly.
Maintaining Sock Puppets Over Time
Creating a sock puppet is only the beginning. To remain credible and useful over time, the account must appear active, consistent, and authentic. Dormant or obviously artificial profiles are more likely to be flagged by platforms or ignored by the communities you are trying to observe. Maintaining a sock puppet means simulating the behaviour of a genuine user, without attracting unnecessary attention.
Simulating Real Behaviour
Regular interaction is key to building a believable presence. Depending on the platform, this might include:
- Liking or sharing posts
- Following relevant accounts or joining groups
- Commenting or replying in a manner consistent with the persona
These interactions should be contextually appropriate and contribute to the puppet’s credibility. For example, a user who claims to be interested in cybersecurity might follow industry influencers, comment on relevant articles, or share news stories.
Scheduling Realistic Activity Patterns
Sock puppets should reflect normal online behaviour. Consider the timezone and daily schedule of the persona. If your puppet claims to be based in Berlin, it would be unusual for them to post at 3 a.m. local time. Avoid excessive or erratic posting, which can appear automated or suspicious. A light but consistent activity pattern over time is more convincing than bursts of high engagement.
Avoiding Automation Red Flags
Some platforms are aggressive in detecting and removing accounts that behave like bots. Avoid scripted or repeated actions, especially immediately after account creation. Do not mass-follow users or copy-paste identical comments across threads. Behave like a real person—slow, deliberate, and occasionally imperfect.
Regularly Updating Profile Content
Real users update their profiles from time to time. Refresh your puppet’s bio, add a new interest, or change a profile picture occasionally to reflect life events or shifting interests. These subtle changes reinforce the illusion of an active, evolving online identity.
Ultimately, a successful sock puppet account blends in. It should quietly accumulate a digital footprint that supports its cover story and gives you access to the information you need, without ever drawing attention to itself.
Risks, Red Flags, and Account Burnout
Even well-crafted sock puppets carry risk. Platforms continue to improve their ability to detect suspicious behaviour, and users themselves may flag accounts that appear inauthentic. Understanding common warning signs and knowing when to retire or rotate an identity is key to maintaining long-term operational capability.
Common Ways Sock Puppets Get Flagged or Banned
Sock puppets may be suspended or deleted for a range of reasons, including:
- Logging in from multiple geographic locations in a short space of time
- Sudden spikes in activity (e.g. mass liking, following, or posting)
- Use of stock or AI-generated profile images that resemble known fake accounts
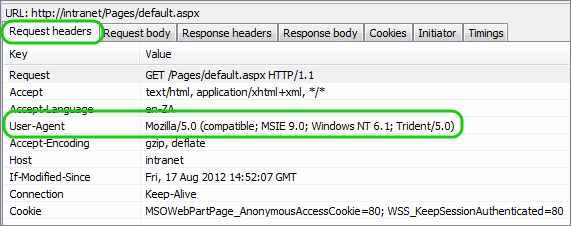
- Repeated use of the same contact details, browser fingerprint, or device setup
- Lack of meaningful interaction or organic growth over time
Even a single policy violation can draw scrutiny, particularly on mainstream social media platforms where automated systems are quick to act.

Avoiding Repetitive Patterns Across Accounts
If you operate multiple sock puppets, ensure that each has a unique and independent identity. Reusing the same backstory, writing style, or image sources across accounts can make them easier to detect and link together. Separate devices, email addresses, and behavioural traits help to isolate each puppet and reduce the risk of a cascading compromise.
When to Retire a Puppet and How to Replace It Safely
No sock puppet should be considered permanent. If an account is inactive, becomes untrustworthy, or begins attracting unwanted attention, it is often safer to retire it than to try and recover its credibility. Before deletion, remove any content that could be linked to other operations. Keep a log of why it was retired, and plan how a replacement will fill the same role with improved safeguards.
Having Backup Identities Ready
To ensure continuity, it is good practice to maintain a small number of standby identities. This is sometimes referred to as a “puppet farm”. These can be developed gradually in the background, gaining basic credibility over time, so they are ready to use when needed. In some cases, it may also be appropriate to establish layered personas, where one puppet supports or interacts with another to enhance realism.
Maintaining sock puppets is an operational task that requires regular attention. The digital landscape shifts constantly, and even the most convincing puppet may eventually outlive its usefulness. Being prepared to adapt is vital.
7. Tools and Resources
Successful sock puppet operations depend not only on planning and technique, but also on using the right tools to support anonymity, security, and realism. The following categories highlight essential resources for anyone managing online personas, with emphasis on privacy-focused solutions.
VPNs and Secure Browsers
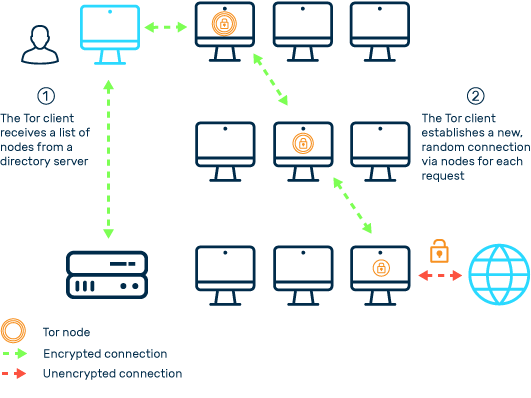
To prevent IP address leaks or location-based flags, always connect through a reliable virtual private network (VPN). Services such as Mullvad or Proton VPN offer privacy-focused features without logging user activity. In addition, using secure or privacy-hardened browsers, such as Firefox with privacy containers, Brave, or Tor Browser, can help prevent tracking and cross-contamination between real and sock puppet identities.
For advanced operations, consider launching sock puppets within secure environments such as Tails OS or a hardened virtual machine to reduce the digital footprint even further.
Image Generation Tools
Choosing a believable profile image is vital. AI-generated photo tools like ThisPersonDoesNotExist or Generated.Photos create unique images that are not traceable to real people, reducing the risk of impersonation claims. However, these images should be reviewed carefully for visual anomalies that might suggest they are artificial. Alternatively, use licence-free photo repositories where permitted.
Secure Email Services
Every puppet should have its own email address from a secure, privacy-conscious provider. Services such as ProtonMail, Tutanota, or Mailfence are widely used for this purpose. Avoid mainstream providers that require phone verification or link accounts to existing profiles. Where possible, create the email account using the same VPN and device you plan to use for the puppet itself.
Password and Identity Managers
Managing multiple identities requires strict separation and secure record-keeping. Tools like Bitwarden, KeePassXC, or 1Password can be used to store login details, backstory notes, recovery options, and activity logs in an encrypted format. Avoid reusing passwords or security questions across accounts, and clearly label each identity to avoid mistakes.
Burner Phone and SMS Services
Some platforms require phone number verification. Where legally permitted, use burner phones or temporary SMS services to meet this requirement. Options include physical SIMs with disposable devices or online services such as MySudo or Silent Link, though reliability and legality vary by region. Never use your personal or work number under any circumstances.
A well-prepared toolkit makes managing sock puppets more secure, efficient, and scalable. Review your tools regularly, keep backups where needed, and ensure you remain up to date with changes in platform behaviour or verification processes.
Final Thoughts and Best Practices
Sock puppet accounts are powerful tools for legitimate online research. When used responsibly, they enable investigators, analysts, and researchers to access vital information, monitor digital threats, and engage with online communities without exposing their true identity. However, with this capability comes a significant ethical and operational responsibility.
These accounts should never be used to deceive, manipulate, or harm individuals. Their purpose is to observe, gather intelligence, and support investigations that serve the public interest or protect organisations from threats. Operating within legal boundaries and upholding professional standards is essential.
The digital landscape is constantly changing. Platforms evolve, detection methods improve, and user behaviour shifts. This means sock puppet strategies must also be regularly reviewed and refined. What works today may not be effective tomorrow, so ongoing learning and adaptation are key to maintaining both access and security.
Finally, any organisation or individual engaging in this kind of work should develop their own standard operating procedures (SOPs). These should include clear guidelines for planning, creation, use, and retirement of sock puppet accounts. Testing identities in controlled environments before deploying them for real investigations can also help identify weaknesses before they become liabilities.
Used with care, discipline, and a strong ethical framework, sock puppets can provide valuable insight while keeping investigators safe and discreet.
Red flag photo by Paolo Bendandi and sock puppet photo by Natalie Kinnear.
















































Recent Comments