Ransomware – State of Play
July 2024
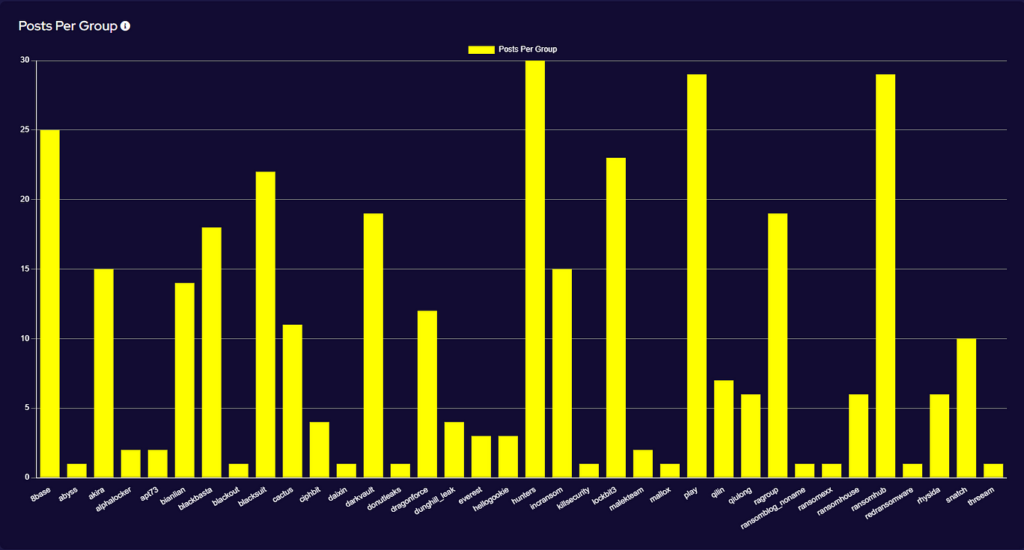
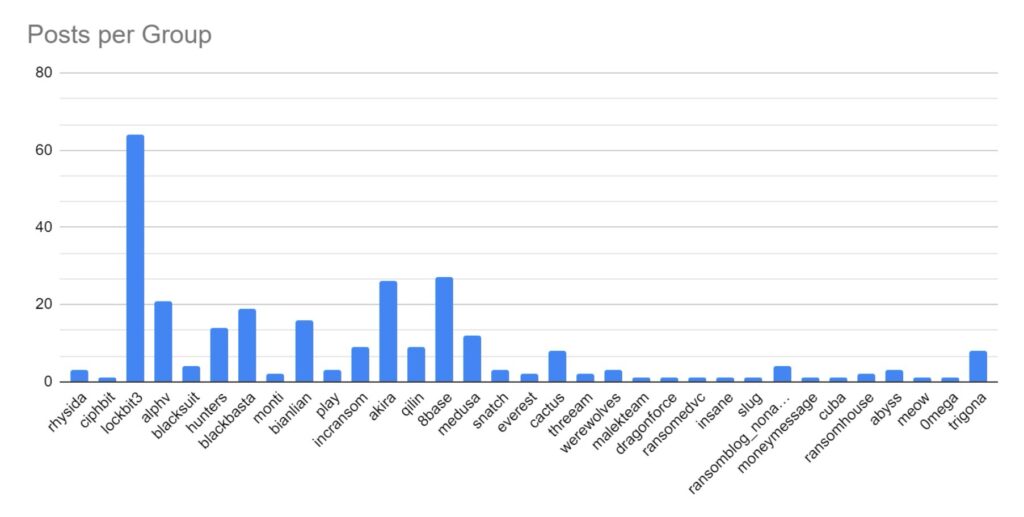
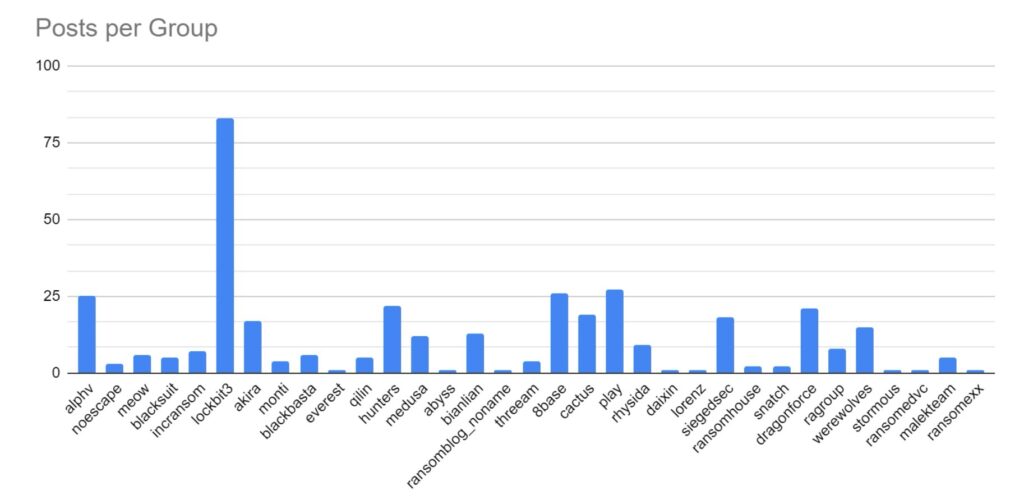
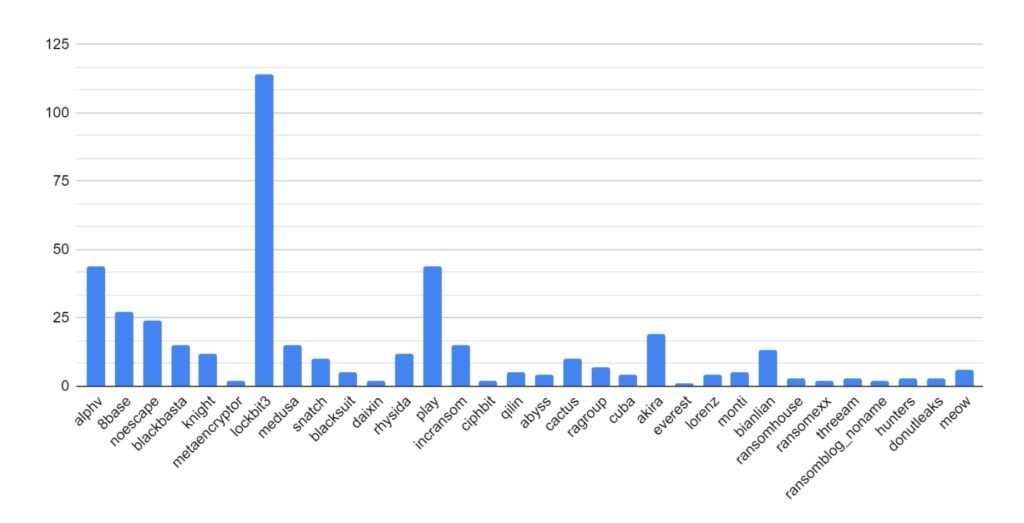
SOS Intelligence is currently tracking 206 distinct ransomware groups, with data collection covering 424 relays and mirrors.
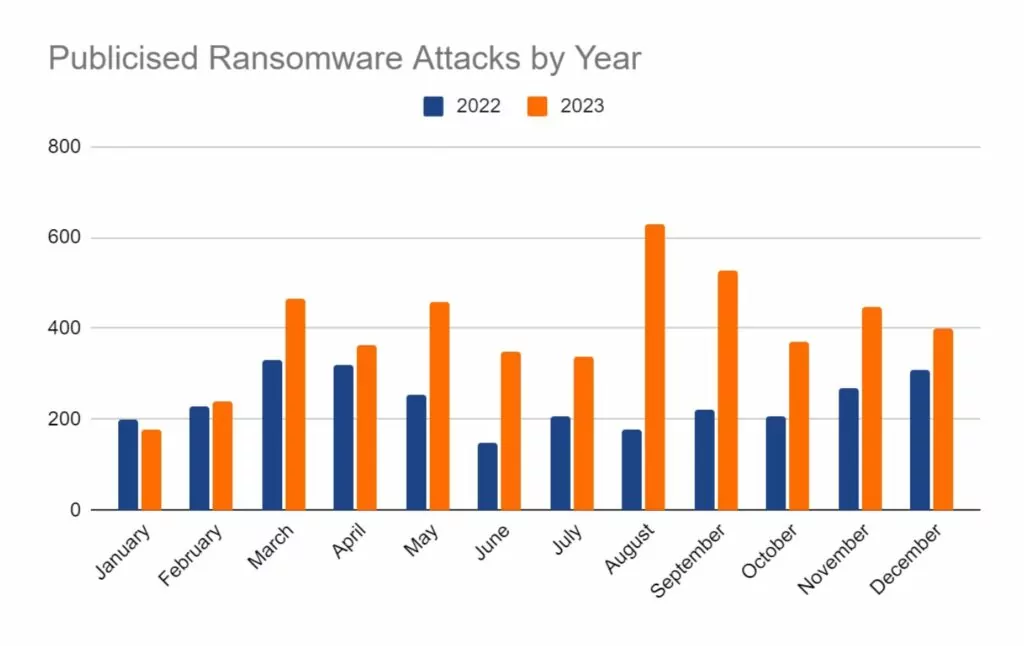
In the reporting period, SOS Intelligence has identified 388 instances of publicised ransomware attacks. These have been identified through the publication of victim details and data on ransomware blog sites accessible via Tor. While this data represents known and publicised data breaches and ransomware attacks, the nature and operation of these groups means that not every successful attack is published and made public, so true figures on the volume of attacks are likely to be higher. Our analysis of available public data is presented below:
Threat Group Activity and Trends
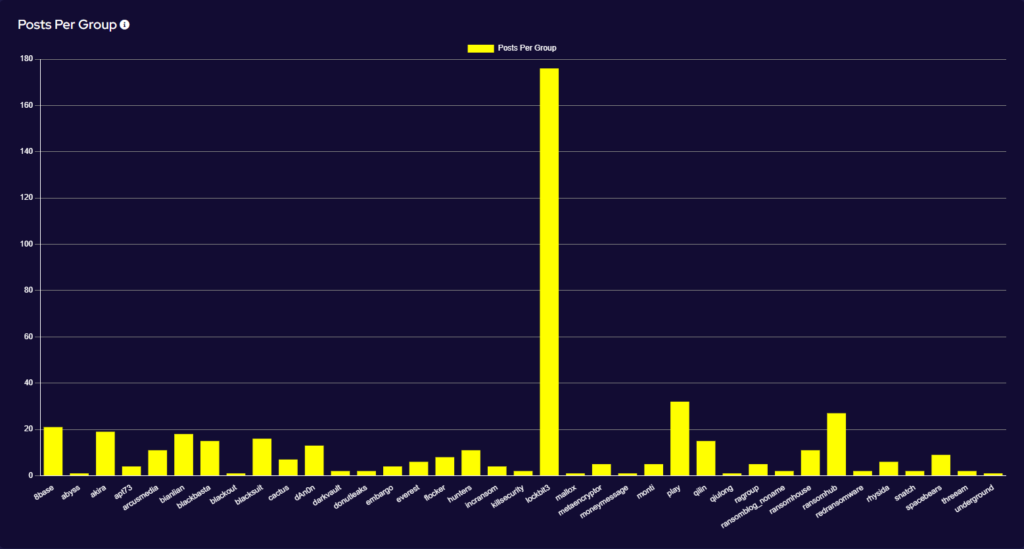
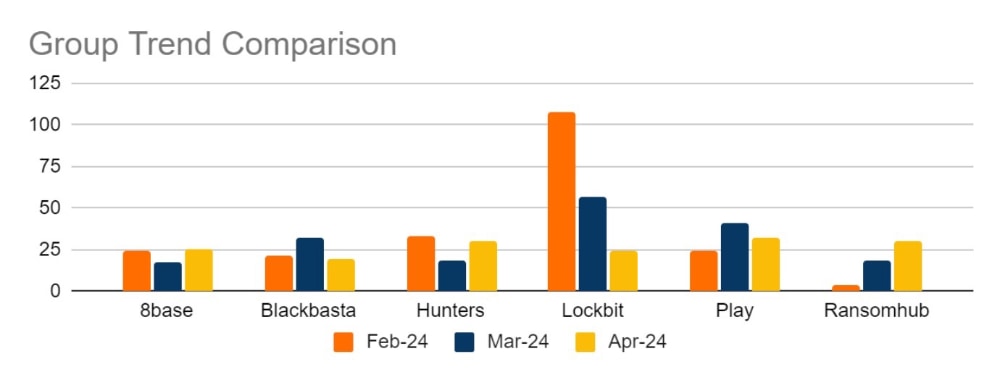
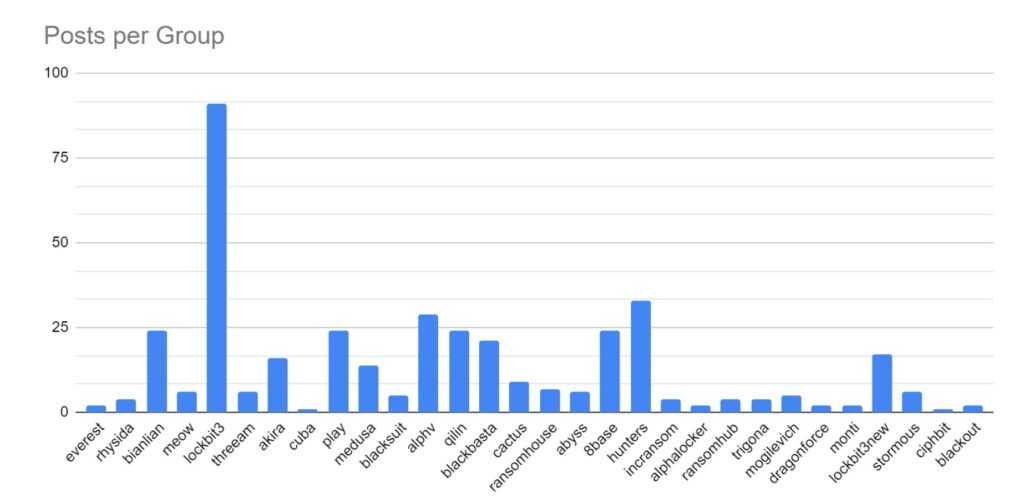
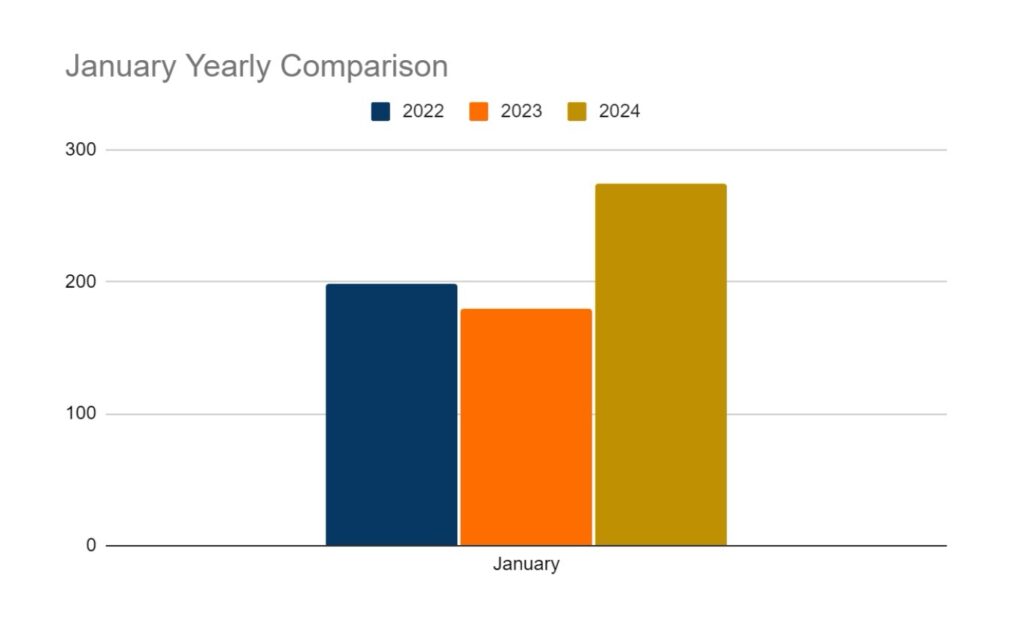
Ransomware activity showed a 2% increase in July when compared to the previous month, and a 16% increase in activity when compared to the previous year. Furthermore, the number of active groups has decreased to 34 from 37 the previous month.
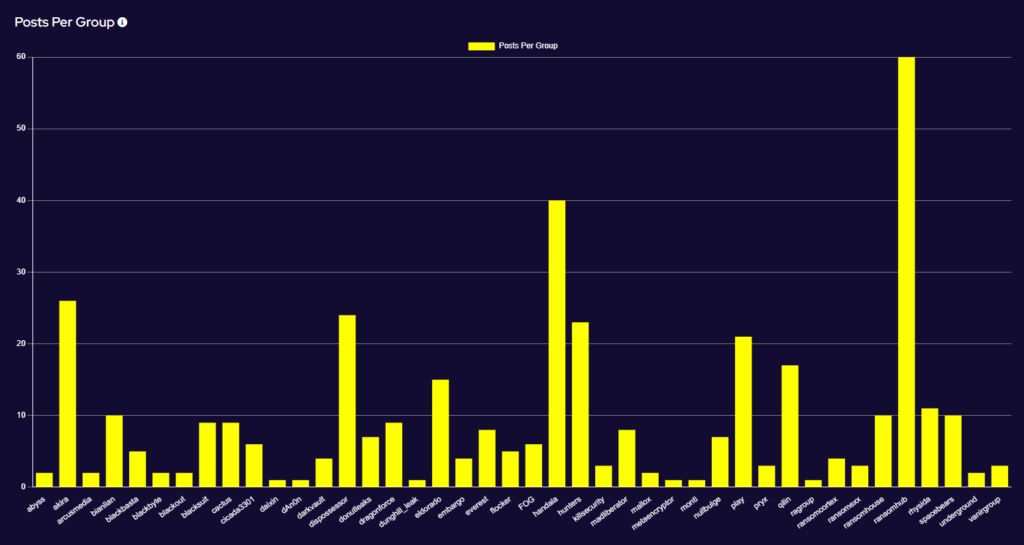
This month has seen a significant increase in activity from Ransomhub, making a significant charge to fill the void left by LockBit. Data for this strain may be skewed, however, by the group using multiple data leak sites to advertise and disseminate stolen data.
Significant activity has been noted from the Handala group, who have exclusively targeted Israel and Israel-based entities over the month. Handala (Arabic: حنظلة) is a prominent national symbol and personification of the Palestinian people, so this activity is highly likely a response to the continued conflict in the Middle East. Handala has been increasing activity against Israel throughout the year, including significant attacks against Zerto, and allegedly Israel’s Iron Dome air defence system.
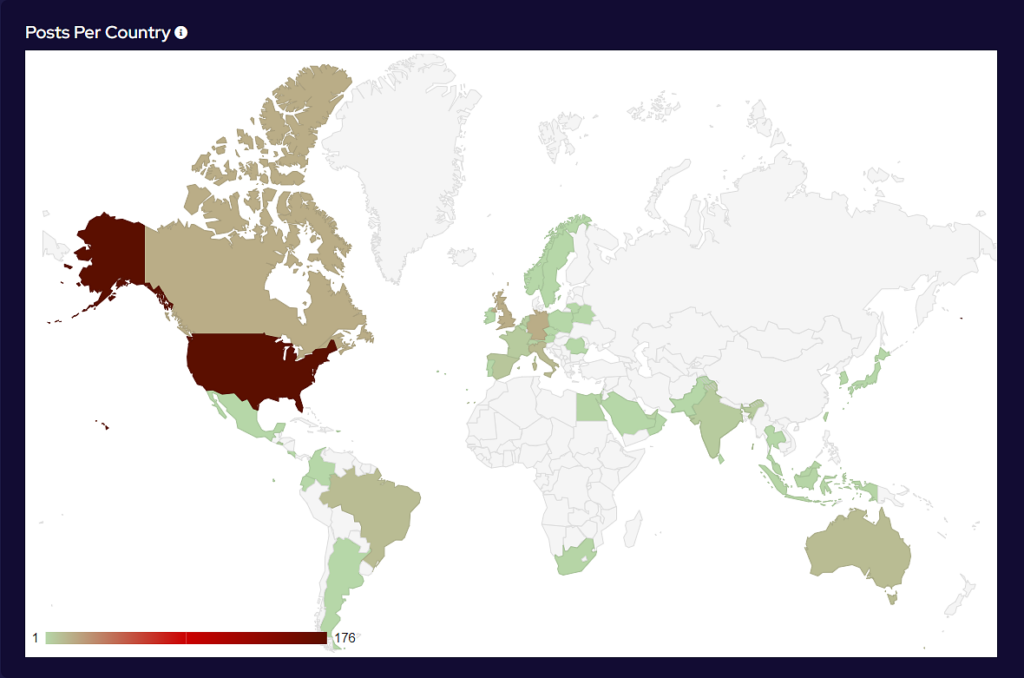
Analysis of Geographic Targeting
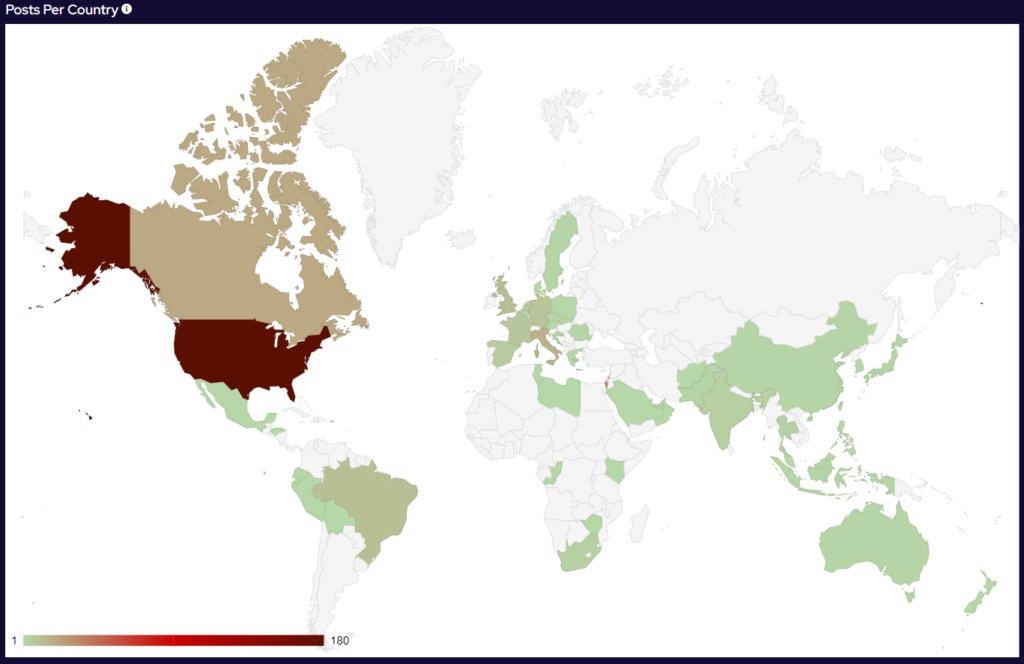
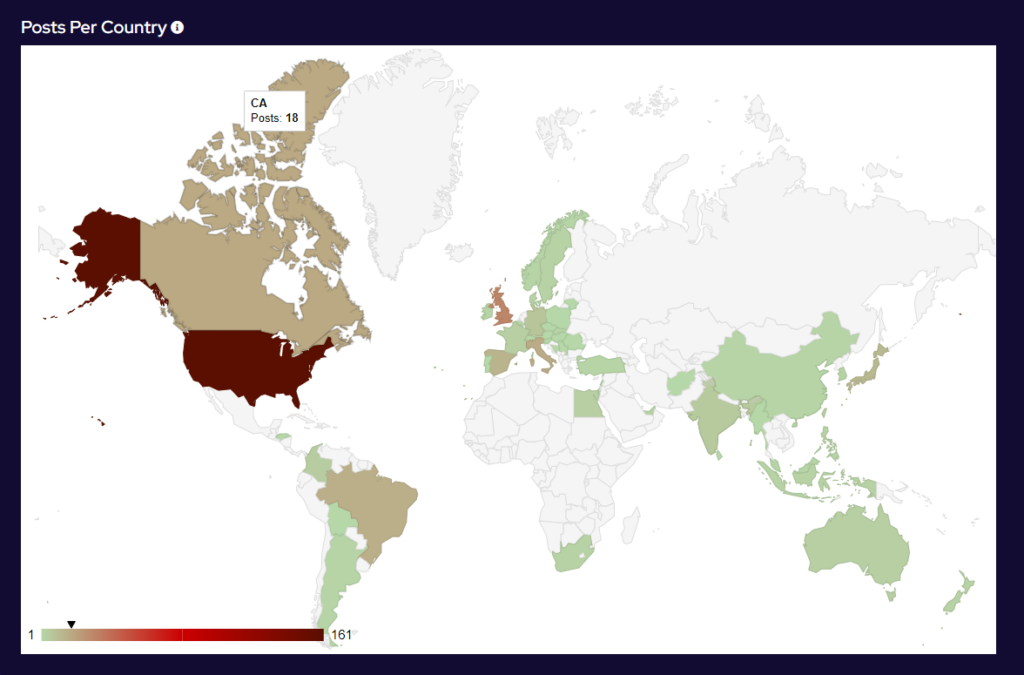
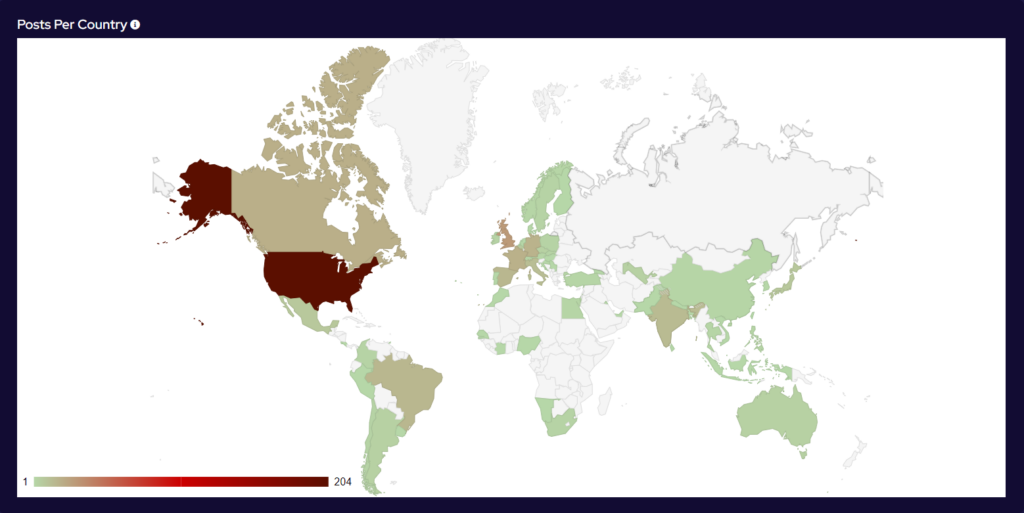
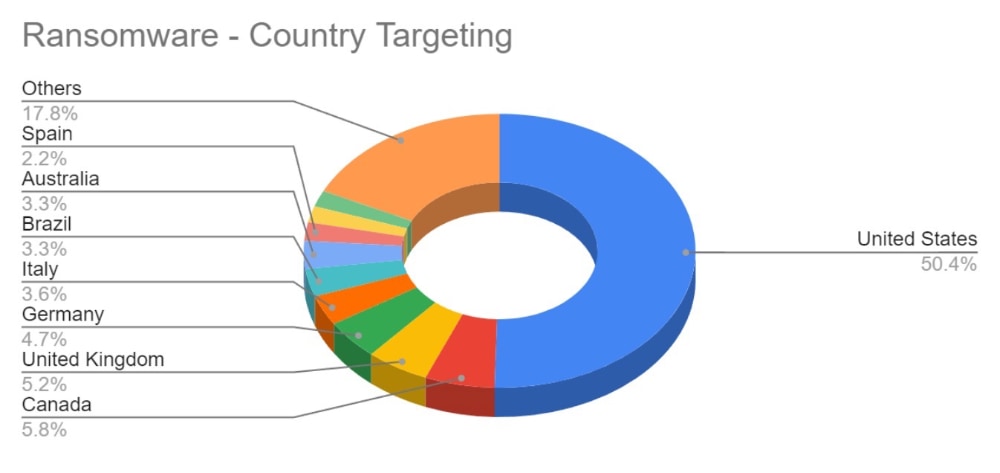
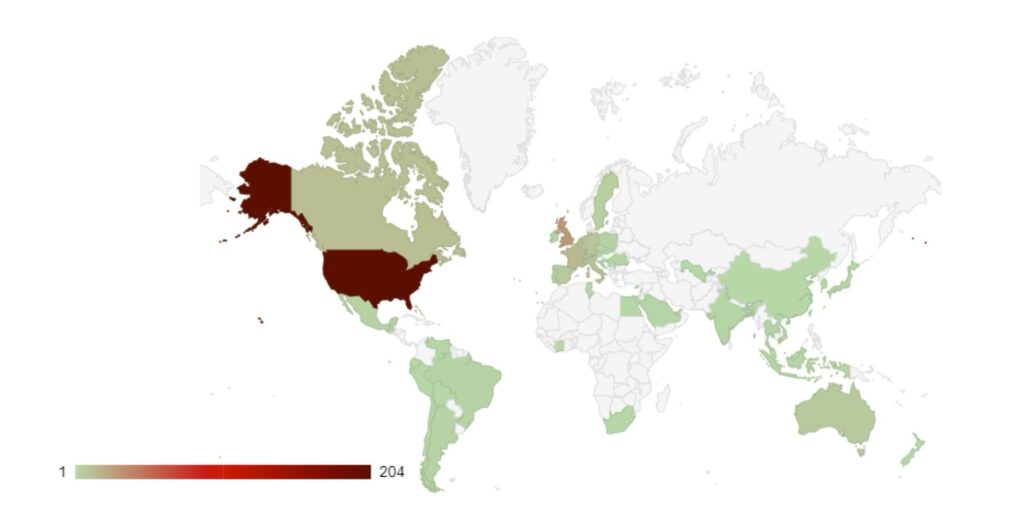
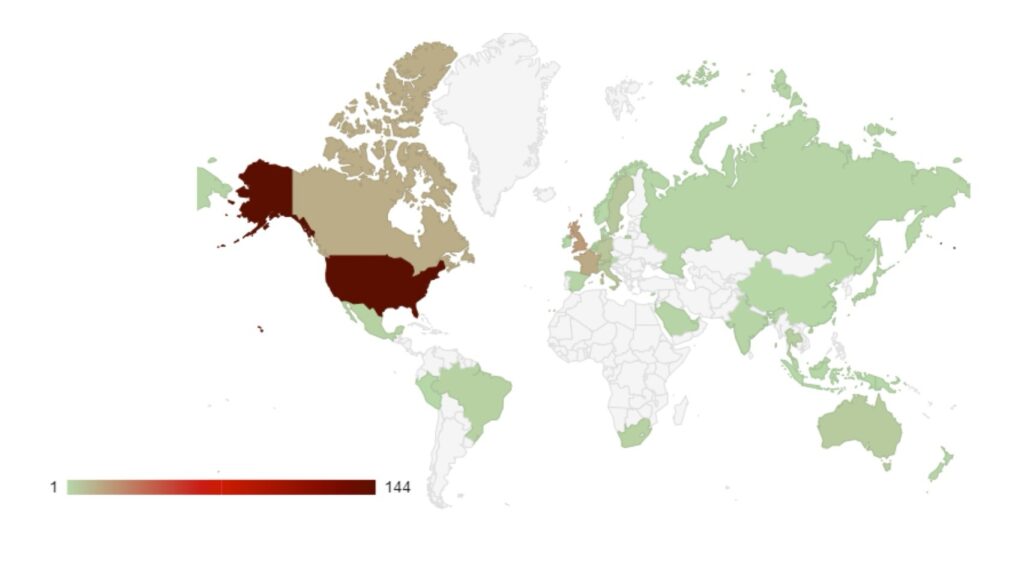
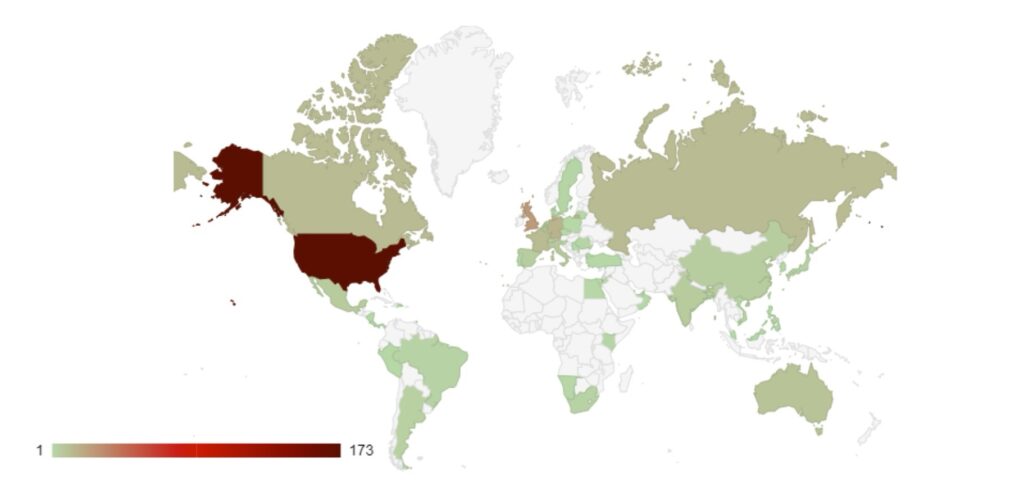
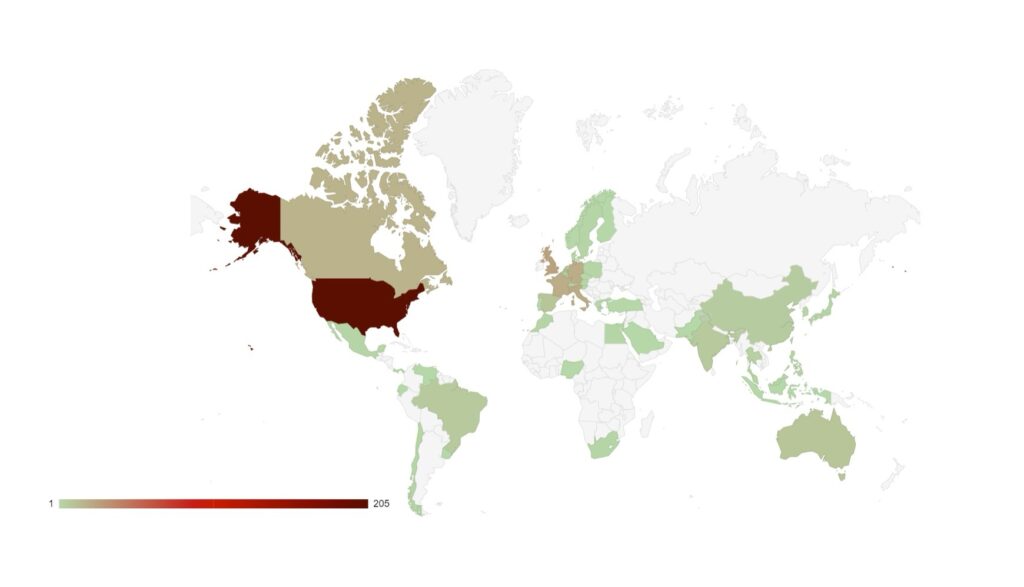
Over the last month, targeting continues to follow financial lines, with the majority of attacks targeted at G7, EU and BRICS bloc countries. Furthermore, a significant number of attacks have been directed towards Israel, with likely political motivations.
Compared to June, 4% more countries were targeted in July. Our data is also showing interesting geographic targeting data. We have observed emerging or developing strains targeting developing countries in Southeast Asia, Africa and South America, whereas more established variants focus more on North America, Western Europe and Australia.
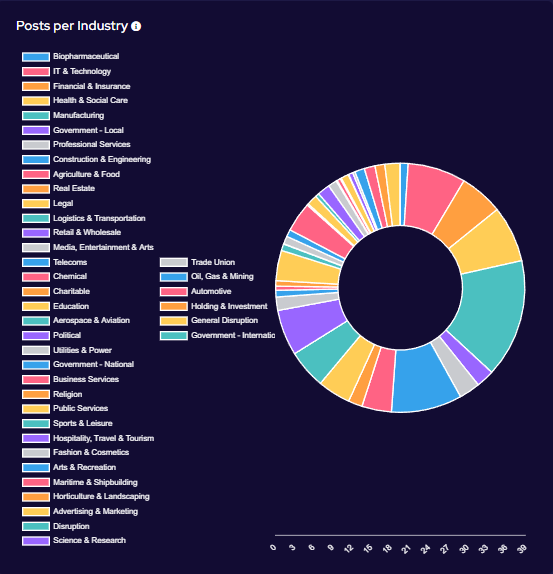
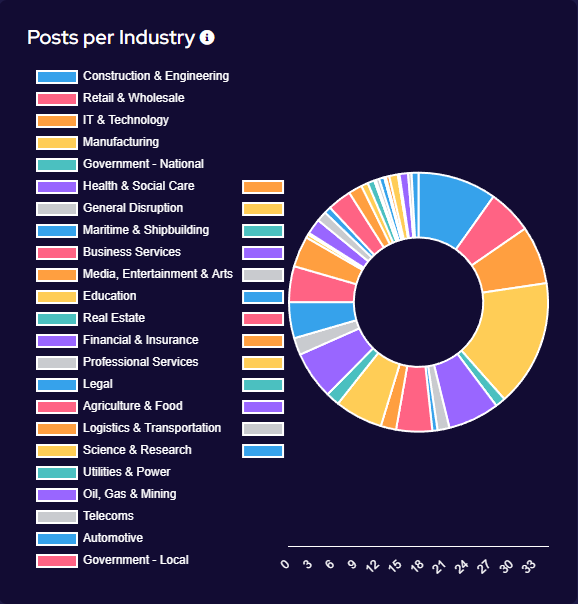
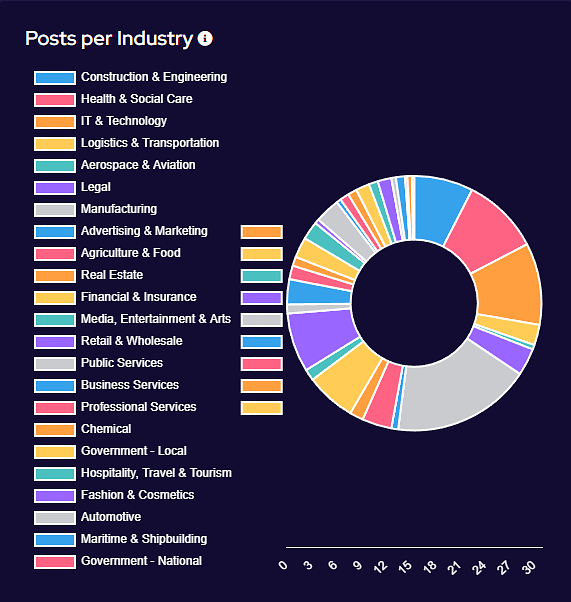
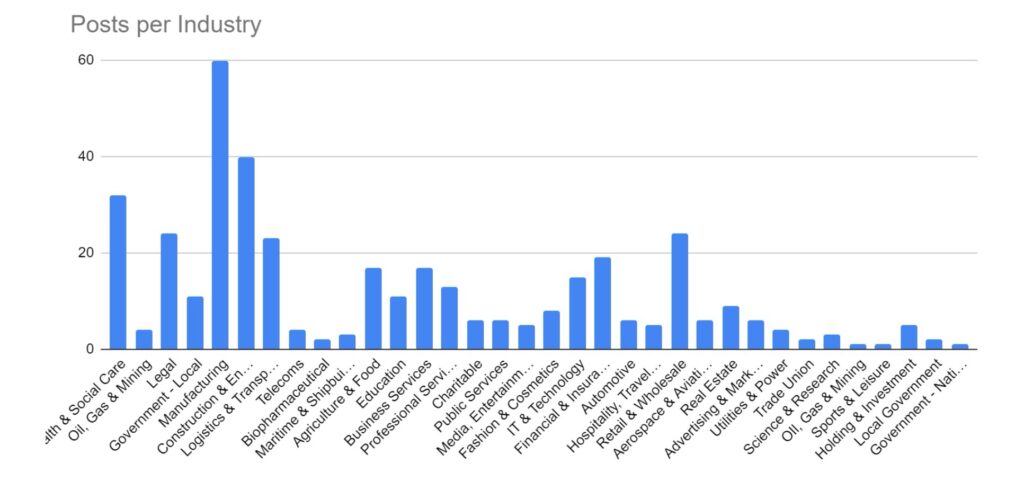
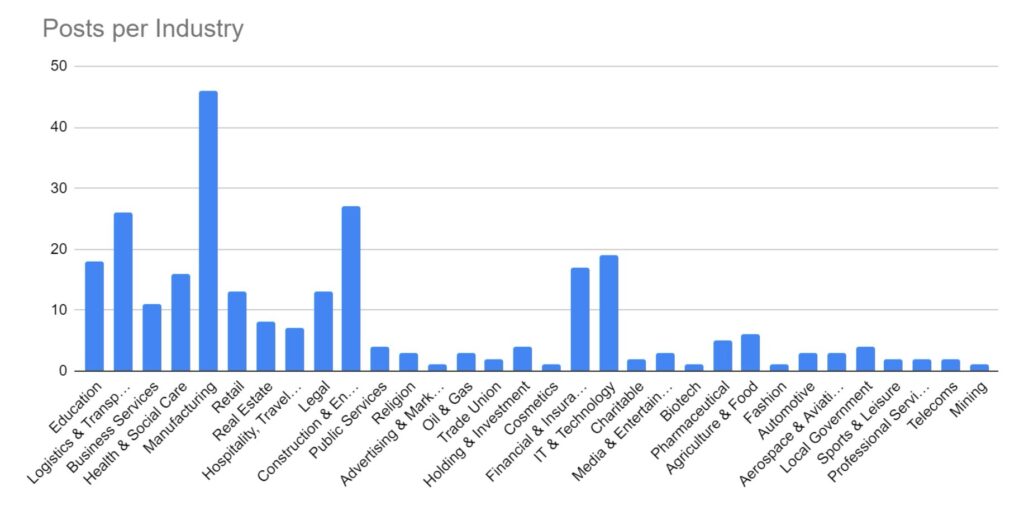
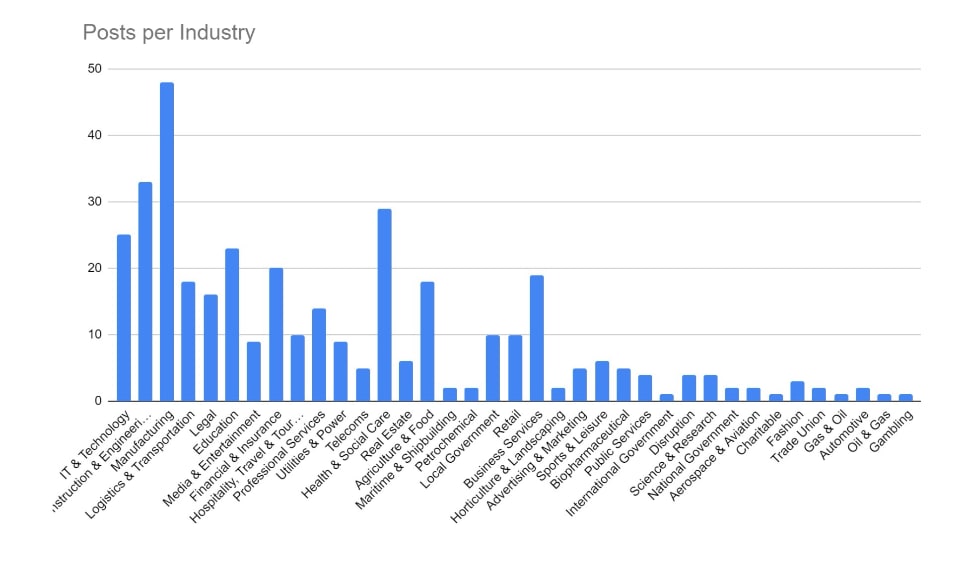
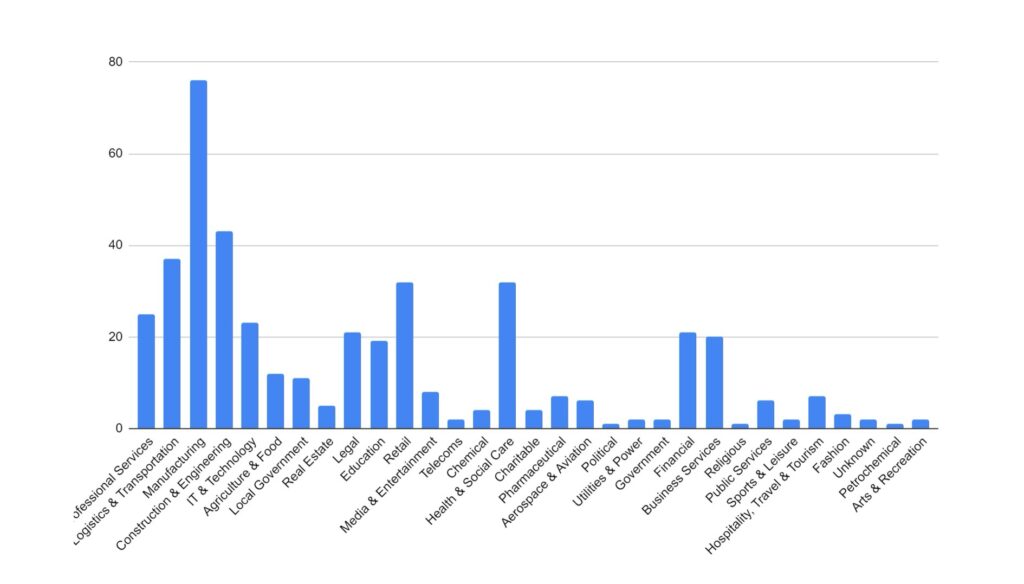
Industry Targeting
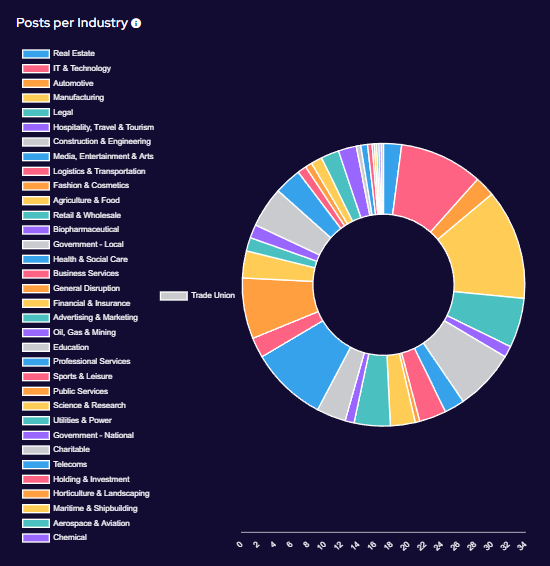
Targeting has broadly increased across all victim sectors, however significant increases have been seen in the Manufacturing, Construction & Engineering and IT & Technology industries.
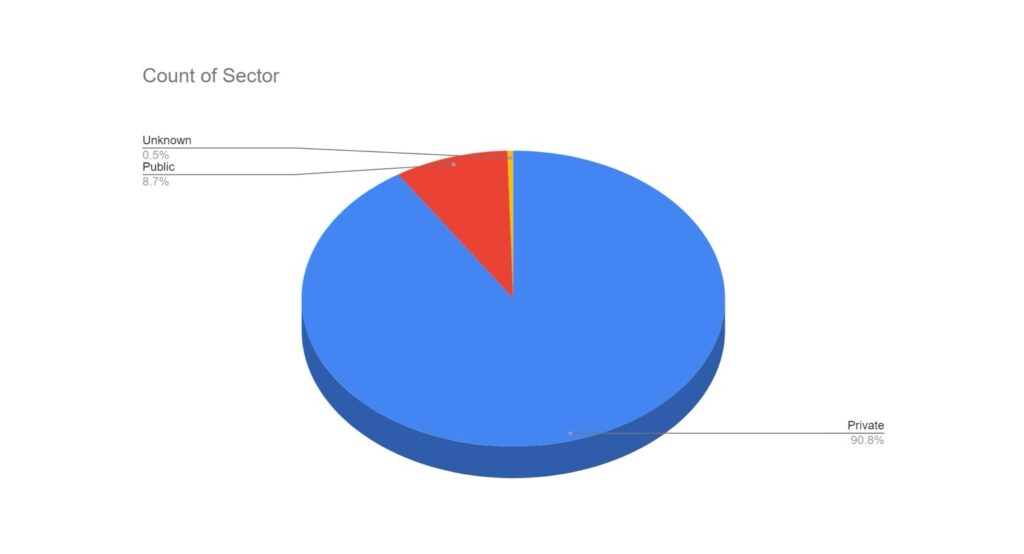
Notably, there appears to have been increased targeting against public-sector entities. This is likely a result of many groups abandoning their affiliate rules on targeting of such victims.
Significant Events
Scattered Spider, a threat actor group known for its social engineering tactics and attacks on VMware ESXi servers, has recently incorporated new ransomware strains into its operations. The group has adopted RansomHub, a rebranded variant of Knight ransomware, and Qilin ransomware. Previously, Scattered Spider used the now-defunct BlackCat ransomware, but it has since shifted to deploying RansomHub in post-compromise scenarios, reflecting its evolving tactics and adaptation to new tools within the cybercriminal landscape.
A flaw in the cryptographic scheme of the DoNex ransomware family has been identified, enabling victims to recover their files for free using a newly released decryptor. This vulnerability, affecting all variants of DoNex, was revealed at a recent cybersecurity conference and involves issues with the encryption key generation and application of ChaCha20 and RSA-4096 algorithms. The decryptor, available through private channels since March 2024, was publicly released following the flaw’s disclosure. Victims are advised to use a large example file for decryption and to back up their encrypted data before proceeding.
Two Russian nationals have pleaded guilty to their involvement in LockBit ransomware attacks that targeted victims worldwide. As affiliates of LockBit’s ransomware-as-a-service operation, they breached vulnerable systems, stole data, and deployed ransomware to encrypt files. One of the individuals has been arrested and faces up to 25 years in prison, while the other has been sentenced to four years. Despite recent law enforcement actions that have seized LockBit’s infrastructure and decryption keys, the ransomware group remains active, continuing to target victims and release stolen data.
Threat Group Development
Change in threat group TTPs to target VMWare ESXi
Play ransomware has recently expanded its focus to target VMware ESXi environments, marking a significant shift in its operations toward broader Linux platform attacks. Utilizing a dedicated Linux locker, Play ransomware encrypts virtual machines (VMs) by first verifying the environment, then scanning for and shutting down active VMs before proceeding with encryption. This approach highlights the group’s advanced evasion techniques and adaptability in the ransomware landscape. The encryption process affects critical VM files, such as disks and configurations, with files receiving a .PLAY extension. Additionally, Play has started using URL-shortening services for its operations, further showcasing its sophistication.
Similarly, Eldorado ransomware, which initially targeted Windows systems, has expanded its scope to include VMware ESXi VMs since its emergence in March. This ransomware employs ChaCha20 encryption across both platforms, allowing affiliates to customise attacks. Meanwhile, the SEXi ransomware operation, rebranded as APT INC, has intensified its focus on VMware ESXi servers since February 2024, leveraging leaked Babuk and LockBit 3 encryptors. APT INC has gained notoriety with high-profile attacks, such as the one on Chilean hosting provider IxMetro Powerhost, with ransom demands reaching millions. The operation continues to use the same encrypted messaging application for negotiations, with no known weaknesses in its encryption for file recovery.
Evolution of BlackBasta
In 2024, Black Basta ransomware has shown significant evolution, adapting to challenges by shifting to custom malware and incorporating new tools after the disruption of its previous partner, QBot. The group now utilizes sophisticated malware like the SilentNight backdoor, memory-only droppers such as DawnCry and KnowTrap, and custom tunneling tools including PortYard and SystemBC. Additionally, it has integrated reconnaissance and execution utilities like CogScan and KnockTrock into its attack processes. These developments underscore Black Basta’s resilience and sophistication, as it continues to pose a formidable global threat by employing advanced tactics and exploiting zero-day vulnerabilities.
New & Emerging Groups
MAD LIBERATOR is a newly emerged ransomware group that launched its leak site in July 2024. The group claims to offer services to help companies fix security issues and recover their files, demanding a fee for their assistance. If the payment is not made, MAD LIBERATOR threatens to publicly list the companies and publish their stolen data. They employ AES/RSA encryption for securing the files. As of the report’s writing, the group had already listed eight victims on its leak site, showcasing their active and ongoing operations.
Ransomcortex is a lesser-known ransomware group with limited information available. However, the group has claimed responsibility for three attacks, all targeting the healthcare sector in Brazil. Despite the lack of detailed information, the choice of victims within such a critical industry highlights the potentially serious impact of their activities.
Vanir Group is a new ransomware group that has quickly gained notoriety for its aggressive and professional tactics. They publicize their attacks via a data leak site and issue intimidating messages to CEOs and domain administrators of the affected companies. These messages warn that the companies’ internal infrastructure has been compromised, backups deleted or encrypted, and critical data stolen. The Vanir Group stresses the importance of cooperation to avoid further damage, threatening to sell or distribute the stolen data if demands are not met. Their website also features an interactive terminal for updates and invites potential affiliates to join their operations. Interestingly, their leak site bears a resemblance to that of Akira, another notorious ransomware group.
Vulnerabilities Observed in Use








Recent Comments