SOS Intelligence is currently tracking 192 distinct ransomware groups, with data collection covering 382 relays and mirrors.
In the reporting period, SOS Intelligence has identified 365 instances of publicised ransomware attacks. These have been identified through the publication of victim details and data on ransomware blog sites accessible via Tor. Our analysis is presented below:
Group Activity and Trends
Ransomware activity showed a 13% decrease in April when compared to the previous month, and a 7 % decrease in activity when compared to the previous year. However, the number of active groups has increased to 36 from 33 the previous month.
The overall drop in victim numbers for April is likely an ongoing effect of the dissolution of AlphV/BlackCat and the significant decrease in activity from Lockbit as a result of law enforcement activity in February.
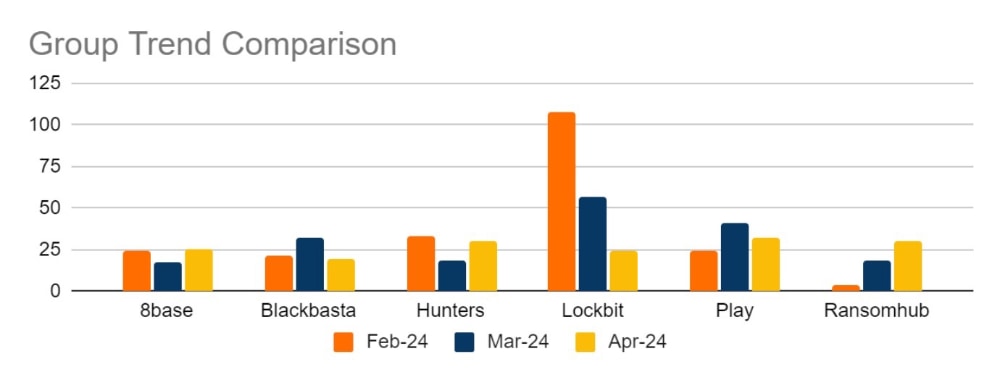
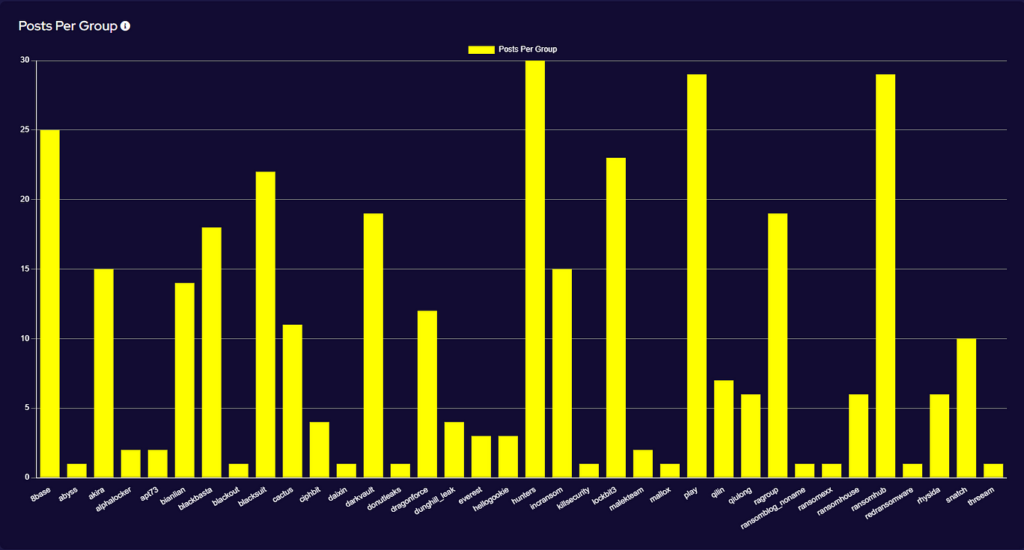
Since February, we have closely monitored group activity for signs of where AlphV and Lockbit affiliates would take their business. The top six groups for the year-to-date are represented above and as yet, no one group has emerged above the others. Hunters International, Play and Ransomhub established themselves as the most active across April, but over the three months, we have also seen significant activity from Blackbasta and 8base. This could suggest that displaced affiliates are not settled on a final product, and have been utilising different ransomware services in the wake of the downfall of AlphV and Lockbit.
Analysis of Geographic Targeting
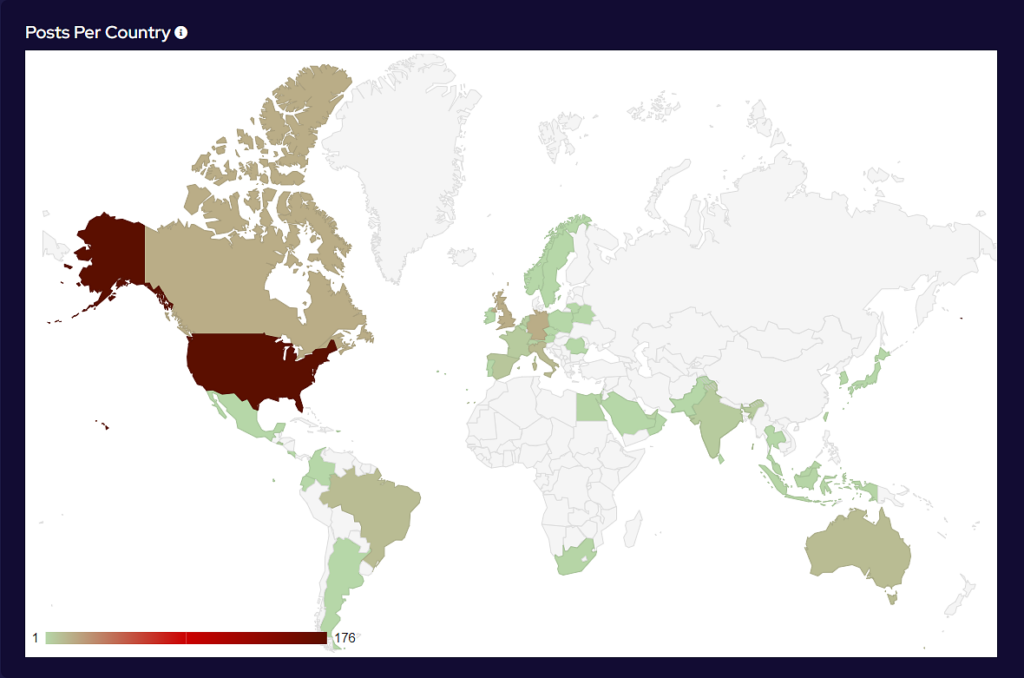
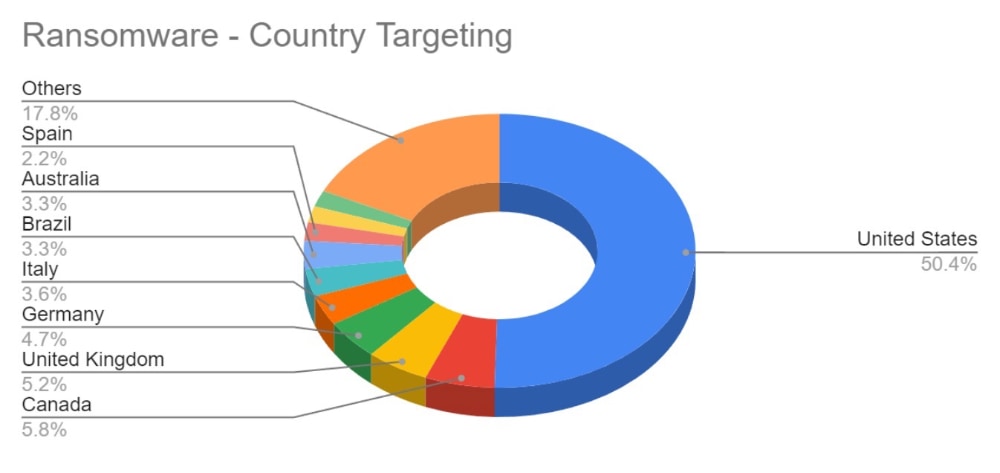
The volume of targeting against US-based victims has remained steady at around 50% of all reported ransomware attacks. Targeting continues to follow financial lines, with the majority of remaining attacks targeted at G7 and BRICS bloc countries.
Compared to March, 11% fewer countries were targeted in April. Our data is also showing interesting geographic targeting data. We have observed emerging or developing strains targeting developing countries, whereas more established variants focus more on North America, Western Europe and Australia.
Top Strains per Country
| United States | Canada | United Kingdom | Germany | Italy | ||||
| – play | – play | – snatch | – ragroup | – ransomhub | ||||
| – hunters | – blacksuit | – dragonforce | – 8base | – rhysida | ||||
| – blacksuit | – akira | – lockbit3 | – lockbit3 | – ciphbit |
Industry Targeting
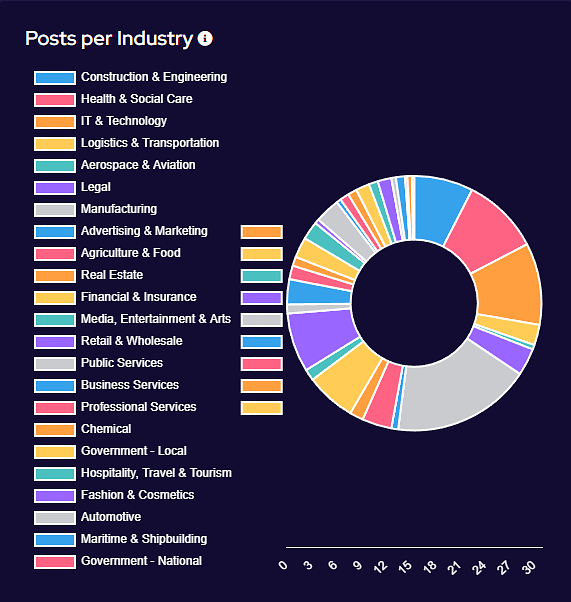
Despite a reduction in victim volume, Manufacturing and IT & Technology remain at the forefront of threat actor targeting. Health & Social Care and Retail & Wholesale continue to see an emergence as a target of choice amongst multiple different variants, likely due to many groups removing targeting restrictions in the wake of law enforcement activity and continued western support for Ukraine.
Top Strains per Industry
| Manufacturing | IT & Technology | Health & Social Care | Construction & Engineering | Retail & Wholesale | ||||
| – play | – ransomhub | – incransom | – play | – hunters | ||||
| – hunters | – darkvault | – qiulong | – cactus | – ransomhub | ||||
| – blackbasta | – cactus | – ransomhub | – lockbit3 | – lockbit3 |
Significant Events
8base targets the United Nations
The United Nations Development Programme (UNDP) was subject to an 8base ransomware attack, resulting in the exfiltration of human resources and procurement information. Despite significant demands being made, the UN has stood fast in its decision to not make payment.
Akira collects ransoms worth USD 42 million
An advisory provided cyber security centre’s in the USA, Netherlands and Europe has revealed that, since March 2023, the Akira ransomware strain has been responsible for attacks against 250 victims, with an estimated total ransom value of USD 42 million.
Lockbit not disappearing without a fight
The District of Columbia Department of Insurance, Securities & Banking,a local government department in the US capital, was added to the long list of Lockbit victims. An estimated 800GB of sensitive data was obtained in the breach, which has not been made available to the public amid reports of it being sold privately.
New Groups
APT73
- Suspected to be a LockBit spin-off – several pages on their leaksite resemble those used by LockBit
- Listed 4 victims since appearing in late April
DarkVault
- Suspected to be a LockBit spin-off – several pages on their leaksite resemble those used by LockBit
- Also involved in other illicit activities, such as bomb threats, doxing, and fraud.
- Listed 22 victims since appearing in April
Quilong
- Currently exclusively targeting victims in Brazil
- Listed 6 victims since appearing in April
SEXi
- Emerged in April 2024, targeting a hosting company in Chile.
- Encrypts VMware ESXi servers and backups, appending the .SEXi extension to encrypted files and dropping ransom notes named SEXi.txt. The name ‘SEXi’ is believed to be a play on ‘ESXi,’ as the attacks exclusively target VMWare ESXi servers.
Space Bears
- Sports a unique front end with corporate stock images but also maintains a classic “wall of shame” for their victims.
- Alongside instructions for affected companies, they operate both a .onion site and a clearnet website.
Vulnerability Exploitation
Threat actors are maintaining techniques focusing on the exploitation of vulnerabilities in public-facing corporate infrastructure.
In recent weeks, Linux variants of the Cerber ransomware have been seen to be deployed utilising exploitation of Atlassian Confluence Data Center and Server, specifically CVE-2023-22518. CVE-2023-22518 is a critical severity (CVSS 9.1) Improper Authorisation Vulnerability which allows an unauthenticated attacker to reset Confluence and create an administrator account for persistent access.

