SOS Intelligence is currently tracking 170 distinct ransomware groups, with data collection covering 319 relays and mirrors.
In the reporting period, SOS Intelligence has identified 373 instances of publicised ransomware attacks. These have been identified through the publication of victim details and data on ransomware blog sites accessible via Tor. Our analysis is presented below:
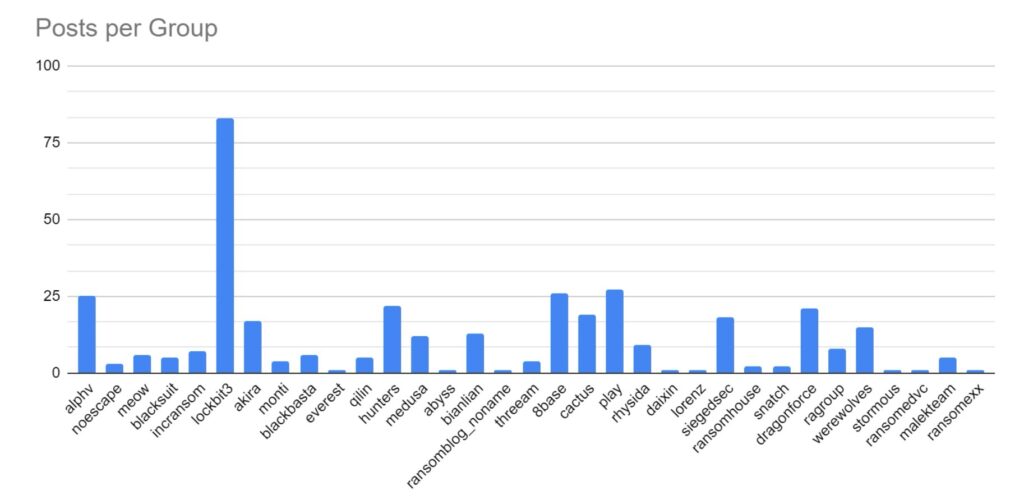
We first look at strain activity. As ever, the ransomware landscape is dominated by strains using affiliate models (Ransomware-as-a-Service (RaaS)). Lockbit remains the most active strain, and while there has been a decrease in overall activity, it maintains a 22% market share. 8base, AlphV and Play remain significantly active, but this month we have also seen significant activity by Hunters (RaaS), Cactus (RaaS), and Dragonforce.
Dragonforce are a newly emerged group, with little known about them at the time of print. Given the level of successful disruption by law enforcement during 2023, it is suspected that this group may be a rebranding of a previous threat group.
The Werewolves group has been observed increasing their level of attacks. The group appears relatively new, however, they have taken responsibility for a 2022 attack on the Electric Company of Ghana which resulted in significant power outages. The veracity of this claim is not known. Their level of activity is called into question by several of their victims also appearing on the LockBit breach site. Six identical posts were seen across both sites. Additionally, the ransomware used is a public domain version of Lockbit3, while their attacks make use of tools leaked from the Conti group. This would seem to indicate that the group was previously an affiliate of LockBit.
What makes this group standout is the targeting of Russian victims. Ransomware groups and operators are quite often pro-russian, with several groups supporting the Russian government publicly in its war against Ukraine. The targeting may explain a potential split from LockBit, and hint at a possible location for the group.
Finally, we have observed increased activity from the SiegedSec group. They appear focused more on data exfiltration, and are politically, rather than financially, motivated. Their focus has been on hacktivism, with a significant focus on targeting Israel and the USA.
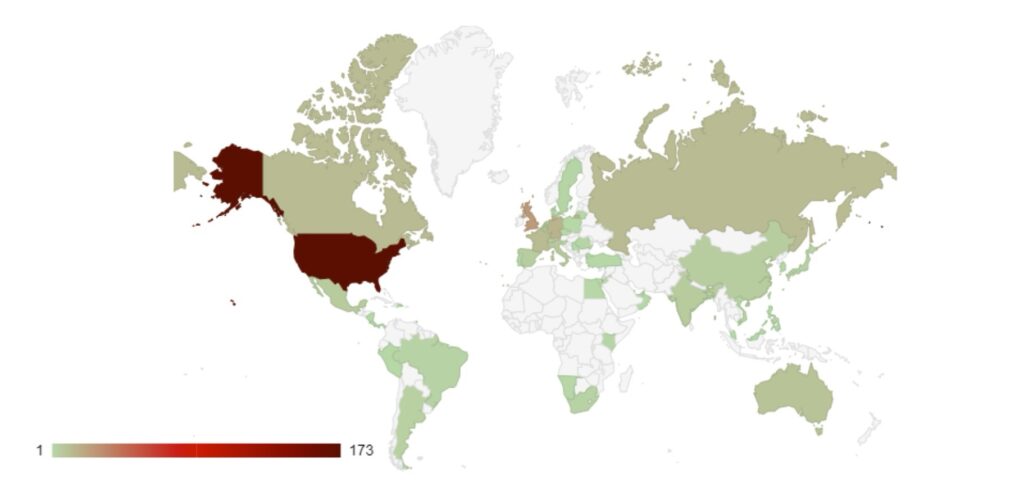
As seen in previous months, the USA remains the primary target of ransomware groups and threat actors. We have observed a steady release of data from Canada, France, Germany, Italy, and the UK. As members of the G7, these countries have strong economies and therefore possess lucrative targets for financially-minded threat actors.
However, this surge in activity may be politically motivated. In recent weeks these countries have all shown support for Israel in its conflict with Hamas, which may give certain threat actors additional motivation to target those countries. As highlighted previously, there have also been significant increases in the targeting of Israel and Russia.
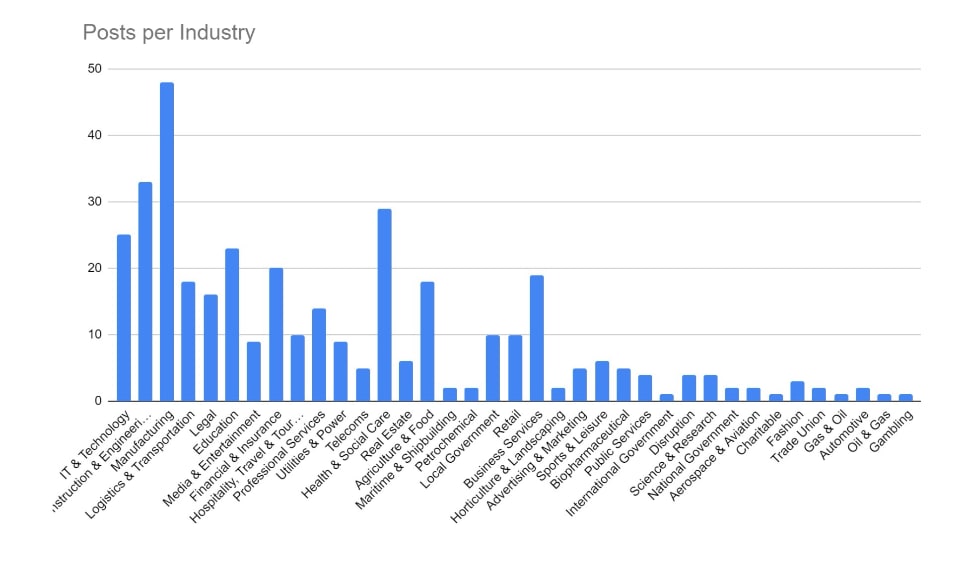
Manufacturing, Construction and Engineering, and IT and Technology have remained the key targeted industries for December. These industries would be more reliant on technology in order to continue their business activities, and so it logically follows that they would be more likely to pay a ransom in order to regain access to compromised computer systems. The Financial and Education sectors have also seen increased activity over the period.
We are seeing a shift in tactics for certain industries, particularly those where data privacy carries a higher importance (such as legal or healthcare), where threat actors are not deploying encryption software and instead relying solely on data exfiltration as the main source of material for blackmail and extortion.

