SOS Intelligence currently tracks 173 distinct ransomware groups, with data collection covering 324 relays and mirrors.
In the reporting period, SOS Intelligence has identified 274 instances of publicised ransomware attacks. These were identified through the publication of victim details and data on ransomware blog sites accessible via Tor. Our analysis is presented below:
Threat Actor Activity
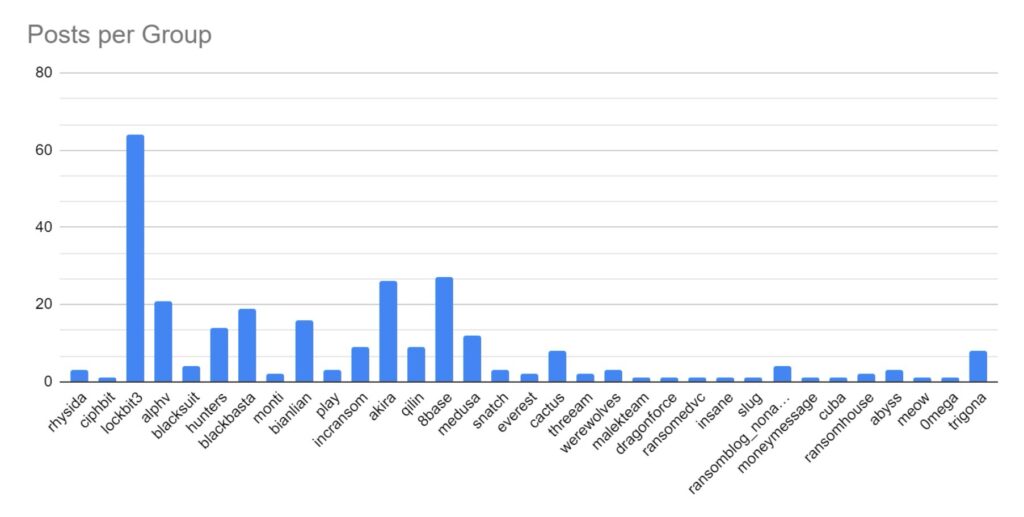
Lockbit has remained the market leader, maintaining a market share of approximately 23%. Blackbasta, Akira, Trigona, 8base and Bianlian have seen significant increases in activity over the month, while there have been decreases in activity from Cactus, Werewolves, Siegedsec, Dragonforce, and Play.
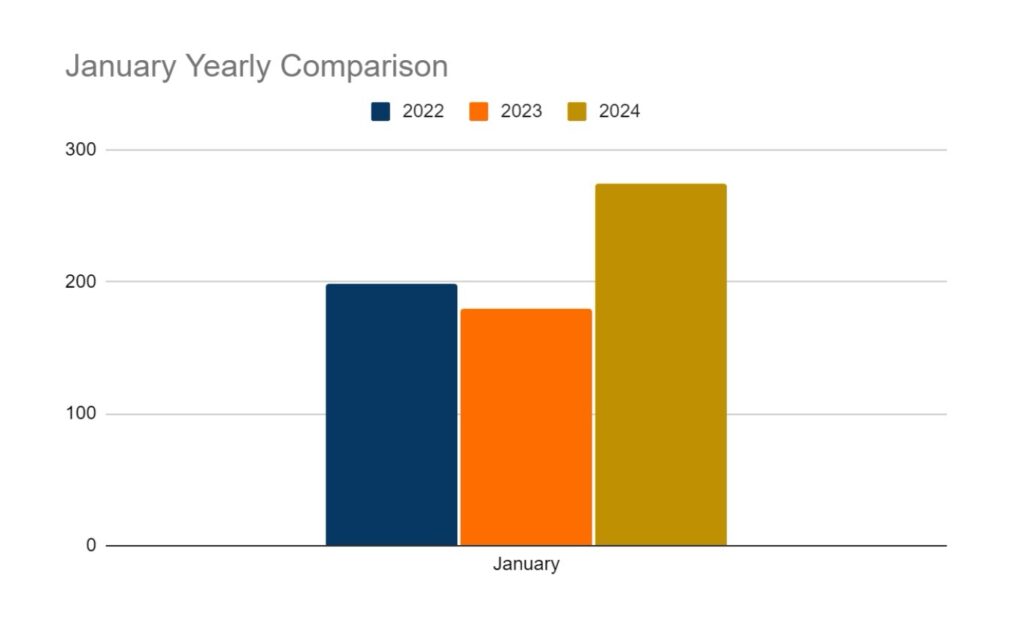
January is typically a quieter month for ransomware threat actors. In 2022, the volume of attacks was 17% less than the yearly average. In 2023, this increased to 54%. This slowing of activity is likely due to the proximity of several national and religious holidays observed globally between December and January. However, in 2024, we observed a significant increase in attacks across January. Two factors stand out as possible causes for this:
- Ongoing global hostilities
It has been observed that pro-Russian cybercriminal groups have been vocally supportive of the ongoing war in Ukraine, and have diverted significant resources in targeting the supporters of Ukraine. Similar patterns have been noted in the targeting of victims in countries which have shown support for Israel.
Although ransomware groups and threat actors are primarily financially motivated, their resources and skills are often seen turned against perceived enemies of the state, blurring the lines between criminal and hostile state activity.
- Counter Ransomware Initiative
The Counter Ransomware Initiative (CRI) is a US-led group of 50 nations and organisations dedicated to promoting solidarity and support in the face of ransomware activity. In October 2023, CRI members pledged not to pay ransoms when faced with cyber attacks.
As a result, it is expected that the number of observed postings to ransomware blogs will increase as victims no longer pay ransoms. This may show an increase in victims’ data being published, rather than an overall increase in the number of victims.
Country Targeting
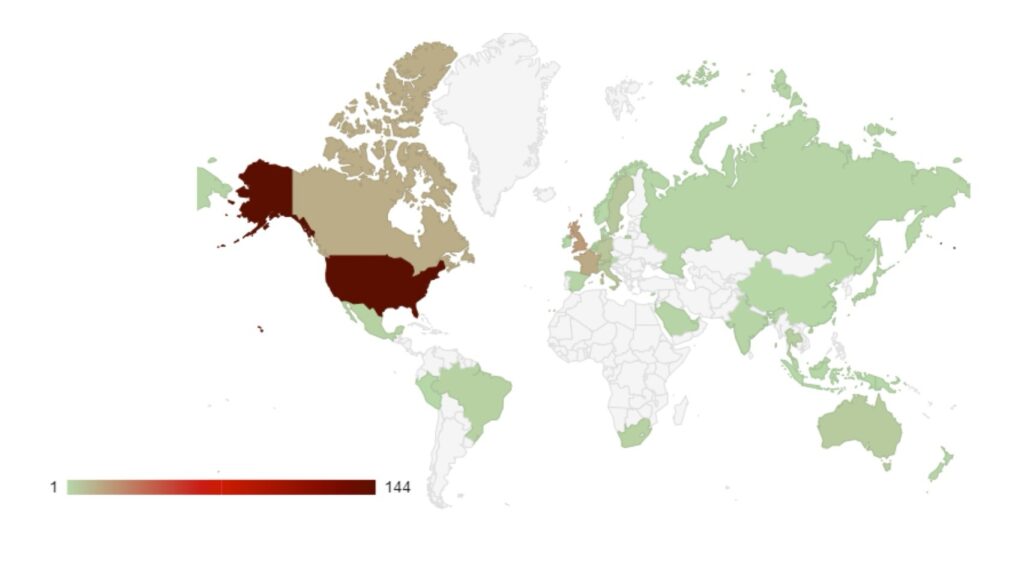
As stated above, ransomware threat actors’ choice of targets can be politically motivated, as well as financially. This is why we continue to see the majority of attacks target the USA, UK, Canada, France, Germany and Italy. As members of the G7, these countries have strong economies and therefore possess lucrative targets for financially-minded threat actors. However, this surge in activity may be politically motivated. Continued support for Israel and Ukraine may give certain threat actors additional motivation to target those countries.
This month has seen an increase in attacks against victims in Sweden. Sweden is in the process of joining NATO, which appears to have presented the country as a target for pro-Russian threat actors in support of the Russian state. Sweden’s membership would increase NATO’s presence in and around the Baltic Sea, a key waterway for allowing the Russian Navy into the North Sea and onward into the Atlantic. Furthermore, it would increase a NATO presence close to Russia’s border with the rest of Europe.
Industry Targeting
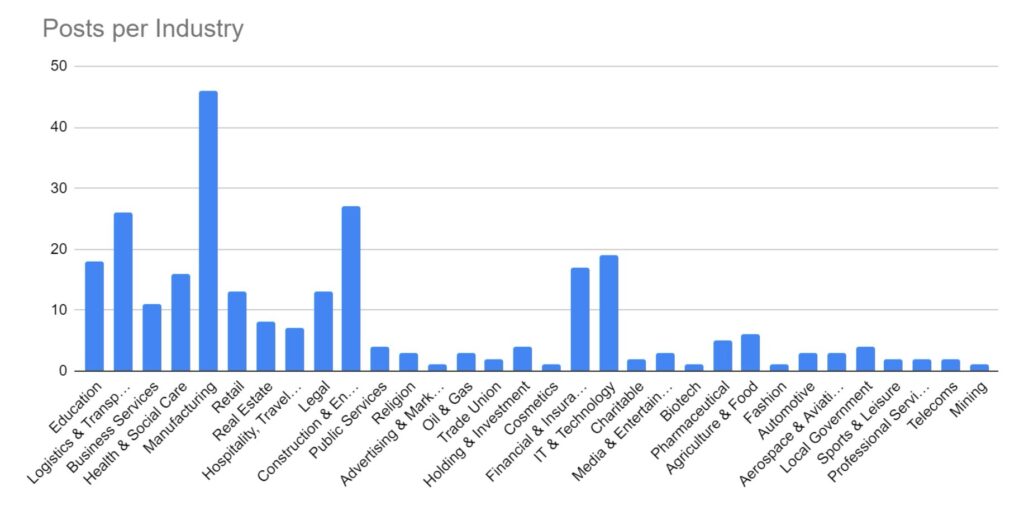
Manufacturing, Construction & Engineering, and Logistics & Transportation have remained the key targeted industries for January. These industries would be more reliant on technology to continue their business activities, so it logically follows that they would be more likely to pay a ransom to regain access to compromised computer systems. The Financial and Education sectors have also seen increased activity over the period.
We are seeing a shift in tactics for certain industries, particularly those where data privacy carries a higher importance (such as legal or healthcare), where threat actors are not deploying encryption software and instead relying solely on data exfiltration as the main source of material for blackmail and extortion.
ALPHV/Blackcat
In December 2023, law enforcement agencies from multiple jurisdictions targeted the ALPHV/Blackcat ransomware group, disrupting the groups’ activities and seizing their domain. Shortly after, the domain was “un-seized” before law enforcement agencies took back control. As a result of this action, the operators behind ALPHV/Blackcat have publicly withdrawn their rules regarding the targeting of Critical National Infrastructure (CNI), in apparent revenge for law enforcement activity.
Since the takedown, ALPHV/Blackcat activity has slowed but does not appear to have stopped. In recent weeks they claim to have targeted and stolen confidential and sensitive data from Trans-Northern Pipelines in Canada, as well as Technica, a contractor working with the US Department of Defence, FBI, and USAF.
The veracity of these claims is still being investigated, and so should be taken with a grain of salt. The ALPHV/Blackcat group has been hurt by law enforcement, impacting their operations and losing them customers. Therefore, it is possible that exaggerated claims are being made to save face and their reputation amongst the cybercrime community.

