SOS Intelligence is currently tracking 166 distinct ransomware groups. Data collection covers 309 relays and mirrors, 110 of which are currently online.
In the reporting period, SOS Intelligence has identified 437 instances of publicised ransomware attacks. These have been identified through the publication of victim details and data on ransomware blog sites accessible via Tor. Our analysis is presented below:
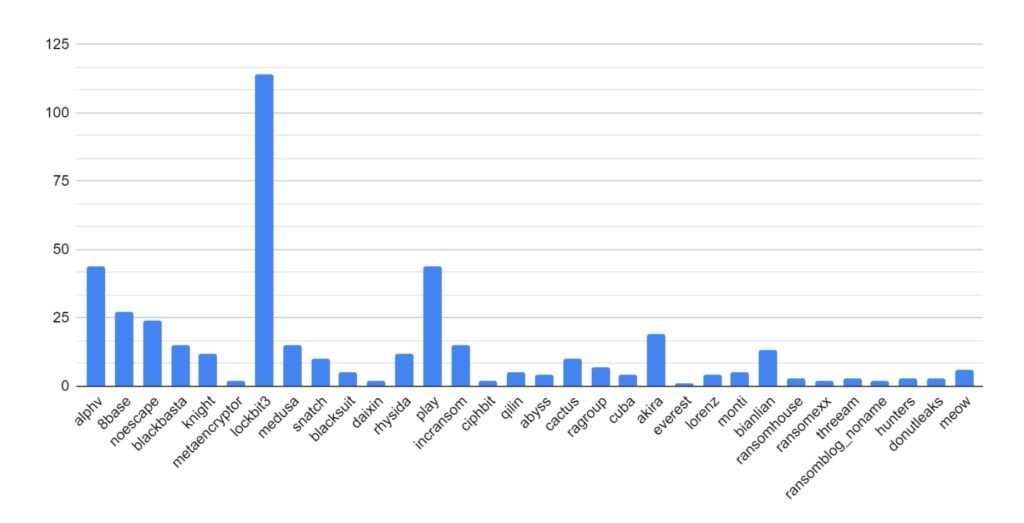
As in previous months, the ransomware landscape is dominated by strains using affiliate models. Lockbit remains the most active strain, and has seen a 73% increase in breach posts when compared to the previous month. High on the list is 8base, who release a large amount of data on 30th November. In contrast to the other high-profile groups observed, it is believed that the 8base group do not have their own proprietary ransomware, but instead rely on using other ransomware-as-a-service (RaaS) variants, such as Phobos.
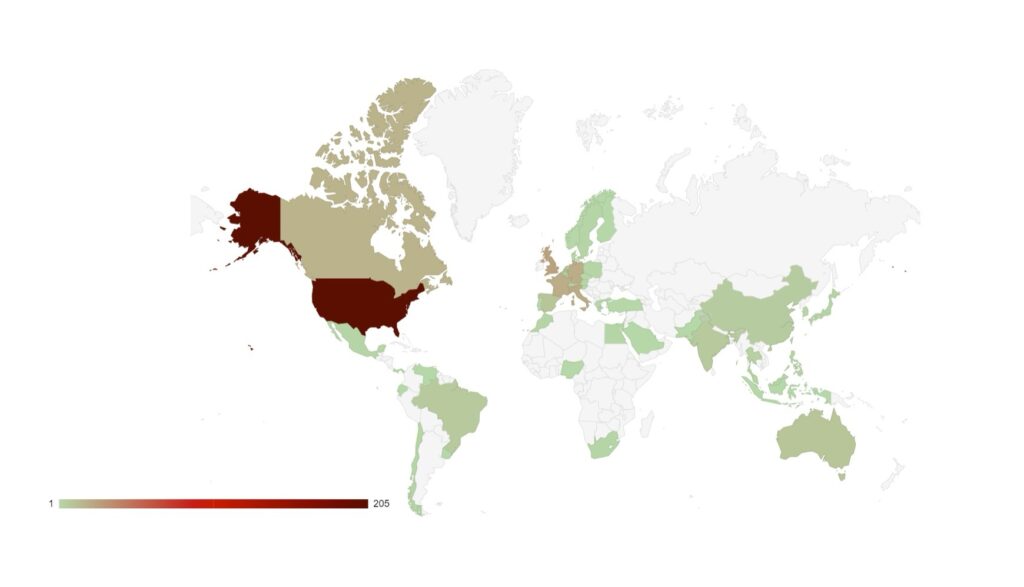
As seen in previous months, the USA remains the primary target of ransomware groups and threat actors. We have observed an increased release of data from France, Germany and Italy, while the UK and Canada have remained high on the list of targeted countries.
As members of the G7, these countries have strong economies and therefore possess lucrative targets for financially-minded threat actors. However, this surge in activity may be politically motivated. In recent weeks these countries have all shown support for Israel in its conflict with Hamas, which may give certain threat actors additional motivation to target those countries.
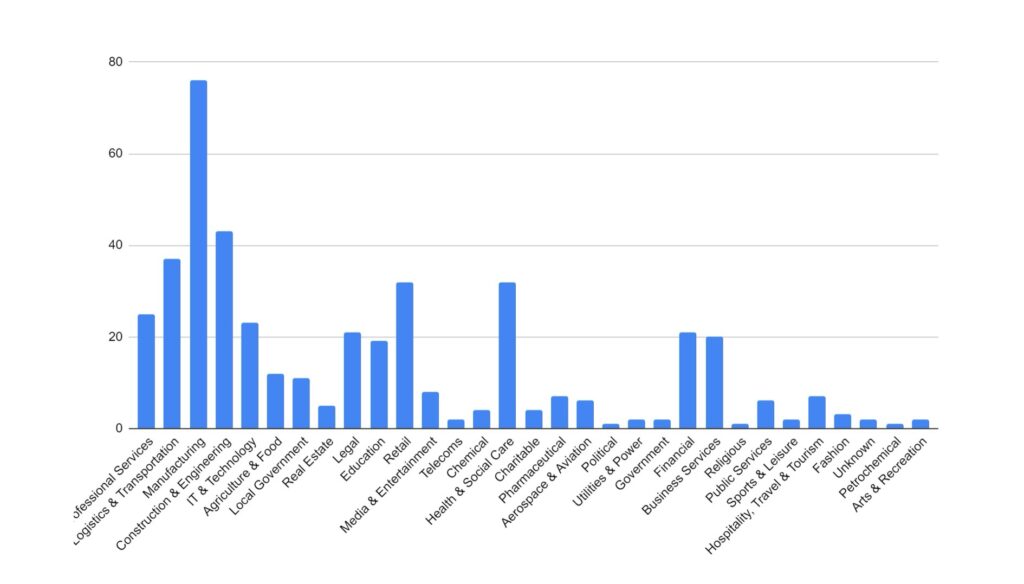
Logistics, manufacturing, and construction have remained the key targeted industries for November. These industries would be more reliant on technology in order to continue their business activities, and so it logically follows that they would be more likely to pay a ransom in order to regain access to compromised computer systems. We are seeing a shift in tactics for certain industries, particularly those where data privacy carries a higher importance (such as legal or healthcare), where threat actors are not deploying encryption software and instead relying solely on data exfiltration as the main source of material for blackmail and extortion.
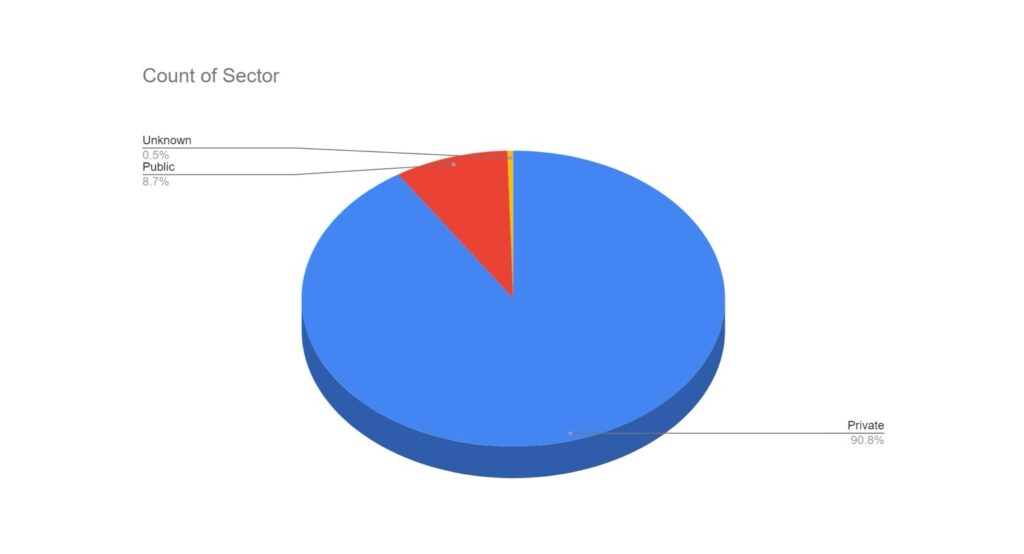
New for this month we have also considered the victim ownership; whether they’re privately or publicly owned. Within breach sites, the publicised victims are overwhelmingly privately owned. Publicly-owned victims tend to be either smaller, local government entities or educational districts within the US school system. Higher level public entities, while offering a lucrative target for hostile state actors, but may be more than a financially-motivated threat actor wishes to take on, owing to the likely increased law enforcement effort to obtain a judicial outcome.

