This weekly blog post is from via our unique intelligence collection pipelines. We are your eyes and ears online, including the Dark Web.
There are thousands of vulnerability discussions each week. SOS Intelligence gathers a list of the most discussed Common Vulnerabilities and Exposures (CVE) online for the previous week.
We make every effort to ensure the accuracy of the data presented. As this is an automated process some errors may creep in.
If you are feeling generous please do make us aware of anything you spot, feel free to follow us on Twitter @sosintel and DM us. Thank you!
1. CVE-2023-32560
An attacker can send a specially crafted message to the Wavelink Avalanche Manager, which could result in service disruption or arbitrary code execution.
Thanks to a Researcher at Tenable for finding and reporting.
Fixed in version 6.4.1.
https://nvd.nist.gov/vuln/detail/CVE-2023-32560
2. CVE-2023-34056
vCenter Server contains a partial information disclosure vulnerability. A malicious actor with non-administrative privileges to vCenter Server may leverage this issue to access unauthorized data.
https://nvd.nist.gov/vuln/detail/CVE-2023-34056
3. CVE-2023-34048
vCenter Server contains a partial information disclosure vulnerability. A malicious actor with non-administrative privileges to vCenter Server may leverage this issue to access unauthorized data.
https://nvd.nist.gov/vuln/detail/CVE-2023-34048
4. CVE-2023-29689
PyroCMS 3.9 contains a remote code execution (RCE) vulnerability that can be exploited through a server-side template injection (SSTI) flaw. This vulnerability allows a malicious attacker to send customized commands to the server and execute arbitrary code on the affected system.
https://nvd.nist.gov/vuln/detail/CVE-2023-29689
5. CVE-2019-14899
A vulnerability was discovered in Linux, FreeBSD, OpenBSD, MacOS, iOS, and Android that allows a malicious access point, or an adjacent user, to determine if a connected user is using a VPN, make positive inferences about the websites they are visiting, and determine the correct sequence and acknowledgement numbers in use, allowing the bad actor to inject data into the TCP stream. This provides everything that is needed for an attacker to hijack active connections inside the VPN tunnel.
https://nvd.nist.gov/vuln/detail/CVE-2019-14899
6. CVE-2023-1389
TP-Link Archer AX21 (AX1800) firmware versions before 1.1.4 Build 20230219 contained a command injection vulnerability in the country form of the /cgi-bin/luci;stok=/locale endpoint on the web management interface. Specifically, the country parameter of the write operation was not sanitized before being used in a call to popen(), allowing an unauthenticated attacker to inject commands, which would be run as root, with a simple POST request.
https://nvd.nist.gov/vuln/detail/CVE-2023-1389
7. CVE-2023-37569
This vulnerability exists in ESDS Emagic Data Center Management Suit due to lack of input sanitization in its Ping component. A remote authenticated attacker could exploit this by injecting OS commands on the targeted system.
Successful exploitation of this vulnerability could allow the attacker to execute arbitrary code on targeted system.
https://nvd.nist.gov/vuln/detail/CVE-2023-37569
8.
https://nvd.nist.gov/vuln/detail/
9.
https://nvd.nist.gov/vuln/detail/
10.
https://nvd.nist.gov/vuln/detail/





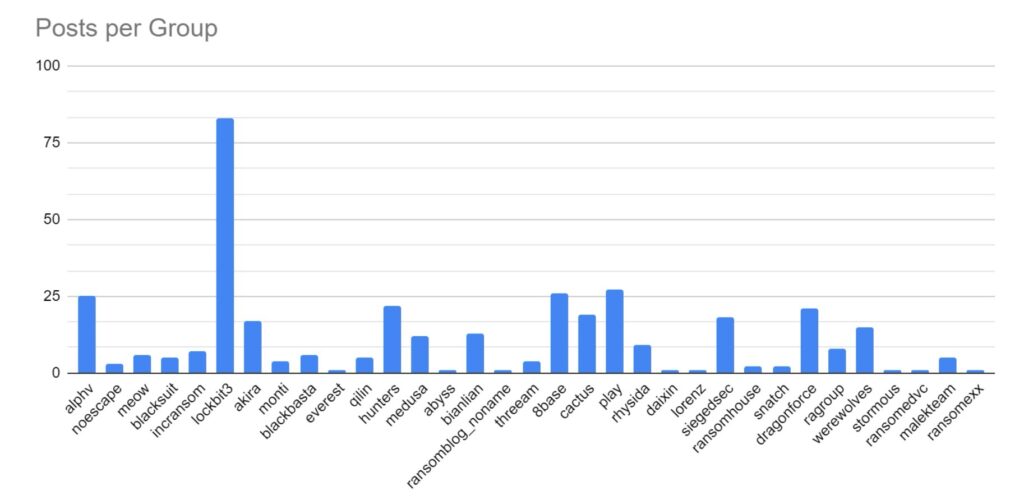
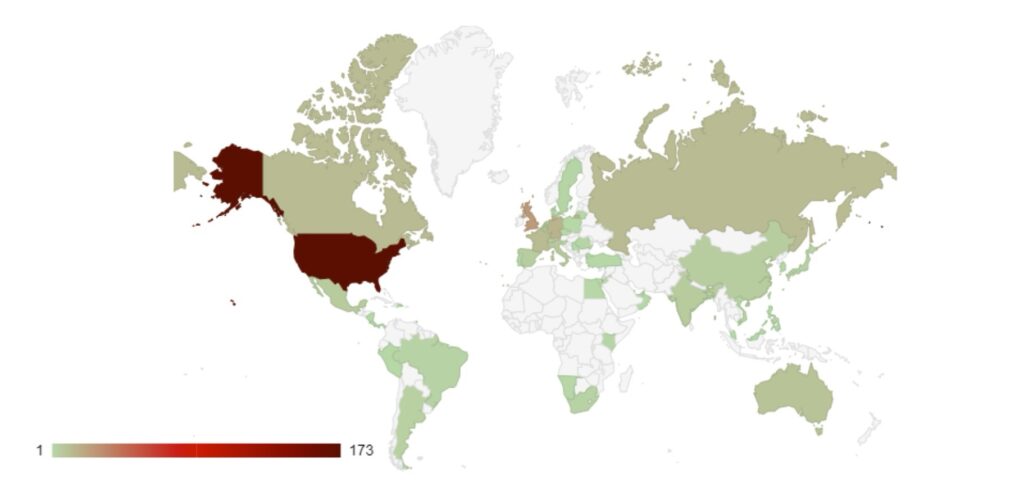
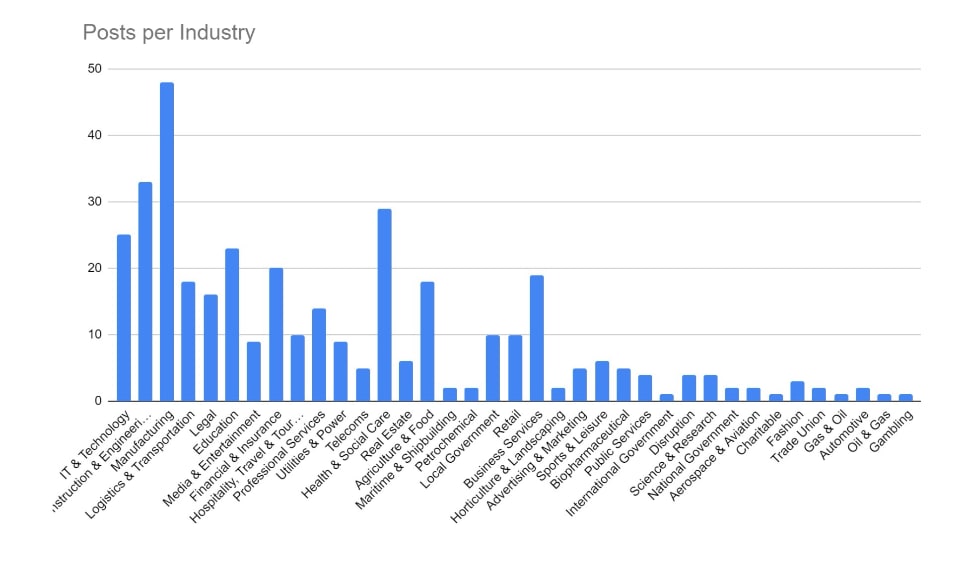
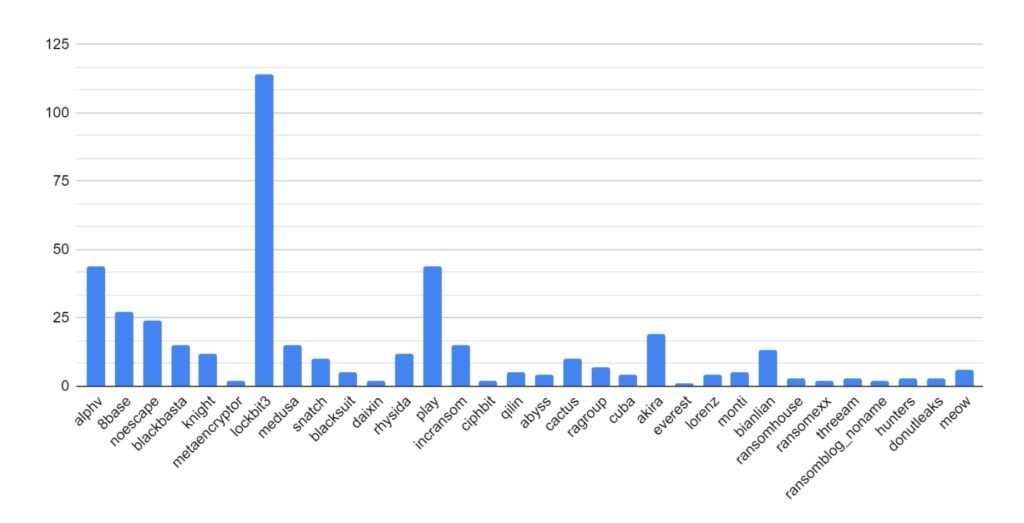
Recent Comments