Home » SOS Intelligence » Page 14
This weekly blog post is from via our unique intelligence collection pipelines. We are your eyes and ears online, including the Dark Web.
There are thousands of vulnerability discussions each week. SOS Intelligence gathers a list of the most discussed Common Vulnerabilities and Exposures (CVE) online for the previous week.
We make every effort to ensure the accuracy of the data presented. As this is an automated process some errors may creep in.
If you are feeling generous please do make us aware of anything you spot, feel free to follow us on Twitter @sosintel and DM us. Thank you!
1. CVE-2023-4966
The HTTP/2 protocol allows a denial of service (server resource consumption) because request cancellation can reset many streams quickly, as exploited in the wild in August through October 2023.
https://nvd.nist.gov/vuln/detail/CVE-2023-4966
2. CVE-2018-17144
Bitcoin Core 0.14.x before 0.14.3, 0.15.x before 0.15.2, and 0.16.x before 0.16.3 and Bitcoin Knots 0.14.x through 0.16.x before 0.16.3 allow a remote denial of service (application crash) exploitable by miners via duplicate input. An attacker can make bitcoind or Bitcoin-Qt crash.
https://nvd.nist.gov/vuln/detail/CVE-2018-17144
3. CVE-2023-4863
Heap buffer overflow in libwebp in Google Chrome prior to 116.0.5845.187 and libwebp 1.3.2 allowed a remote attacker to perform an out of bounds memory write via a crafted HTML page. (Chromium security severity: Critical)
https://nvd.nist.gov/vuln/detail/CVE-2023-4863
4. CVE-2022-3696
A post-auth code injection vulnerability allows admins to execute code in Webadmin of Sophos Firewall releases older than version 19.5 GA.
https://nvd.nist.gov/vuln/detail/CVE-2022-3696
5. CVE-2021-21972
The vSphere Client (HTML5) contains a remote code execution vulnerability in a vCenter Server plugin. A malicious actor with network access to port 443 may exploit this issue to execute commands with unrestricted privileges on the underlying operating system that hosts vCenter Server. This affects VMware vCenter Server (7.x before 7.0 U1c, 6.7 before 6.7 U3l and 6.5 before 6.5 U3n) and VMware Cloud Foundation (4.x before 4.2 and 3.x before 3.10.1.2).
https://nvd.nist.gov/vuln/detail/CVE-2021-21972
6. CVE-2022-3236
A post-auth code injection vulnerability allows admins to execute code in Webadmin of Sophos Firewall releases older than version 19.5 GA.
https://nvd.nist.gov/vuln/detail/CVE-2022-3236
7. CVE-2020-1472
An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC), aka ‘Netlogon Elevation of Privilege Vulnerability’.
https://nvd.nist.gov/vuln/detail/CVE-2020-1472
8. CVE-2012-2459
Unspecified vulnerability in bitcoind and Bitcoin-Qt before 0.4.6, 0.5.x before 0.5.5, 0.6.0.x before 0.6.0.7, and 0.6.x before 0.6.2 allows remote attackers to cause a denial of service (block-processing outage and incorrect block count) via unknown behavior on a Bitcoin network.
https://nvd.nist.gov/vuln/detail/CVE-2012-2459
9. CVE-2021-24084
Windows Mobile Device Management Information Disclosure Vulnerability
https://nvd.nist.gov/vuln/detail/CVE-2021-24084
10. CVE-2022-40684
An authentication bypass using an alternate path or channel [CWE-288] in Fortinet FortiOS version 7.2.0 through 7.2.1 and 7.0.0 through 7.0.6, FortiProxy version 7.2.0 and version 7.0.0 through 7.0.6 and FortiSwitchManager version 7.2.0 and 7.0.0 allows an unauthenticated atttacker to perform operations on the administrative interface via specially crafted HTTP or HTTPS requests.
https://nvd.nist.gov/vuln/detail/CVE-2022-40684
This weekly blog post is from via our unique intelligence collection pipelines. We are your eyes and ears online, including the Dark Web.
There are thousands of vulnerability discussions each week. SOS Intelligence gathers a list of the most discussed Common Vulnerabilities and Exposures (CVE) online for the previous week.
We make every effort to ensure the accuracy of the data presented. As this is an automated process some errors may creep in.
If you are feeling generous please do make us aware of anything you spot, feel free to follow us on Twitter @sosintel and DM us. Thank you!
1. CVE-2018-17144
Bitcoin Core 0.14.x before 0.14.3, 0.15.x before 0.15.2, and 0.16.x before 0.16.3 and Bitcoin Knots 0.14.x through 0.16.x before 0.16.3 allow a remote denial of service (application crash) exploitable by miners via duplicate input. An attacker can make bitcoind or Bitcoin-Qt crash.
https://nvd.nist.gov/vuln/detail/CVE-2018-17144
2. CVE-2023-4911
A buffer overflow was discovered in the GNU C Library’s dynamic loader ld.so while processing the GLIBC_TUNABLES environment variable. This issue could allow a local attacker to use maliciously crafted GLIBC_TUNABLES environment variables when launching binaries with SUID permission to execute code with elevated privileges.
https://nvd.nist.gov/vuln/detail/CVE-2023-4911
3. CVE-2018-13379
An Improper Limitation of a Pathname to a Restricted Directory (“Path Traversal”) in Fortinet FortiOS 6.0.0 to 6.0.4, 5.6.3 to 5.6.7 and 5.4.6 to 5.4.12 and FortiProxy 2.0.0, 1.2.0 to 1.2.8, 1.1.0 to 1.1.6, 1.0.0 to 1.0.7 under SSL VPN web portal allows an unauthenticated attacker to download system files via special crafted HTTP resource requests.
https://nvd.nist.gov/vuln/detail/CVE-2018-13379
4. CVE-2023-4966
A vulnerability in the web-based management interface of Cisco RV340, RV340W, RV345, and RV345P Dual WAN Gigabit VPN Routers could allow an unauthenticated, remote attacker to upload arbitrary files to an affected device. This vulnerability is due to insufficient authorization enforcement mechanisms in the context of file uploads. An attacker could exploit this vulnerability by sending a crafted HTTP request to an affected device. A successful exploit could allow the attacker to upload arbitrary files to the affected device.
https://nvd.nist.gov/vuln/detail/CVE-2023-4966
5. CVE-2017-9841
A buffer overflow was discovered in the GNU C Library’s dynamic loader ld.so while processing the GLIBC_TUNABLES environment variable. This issue could allow a local attacker to use maliciously crafted GLIBC_TUNABLES environment variables when launching binaries with SUID permission to execute code with elevated privileges.
https://nvd.nist.gov/vuln/detail/CVE-2017-9841
6. CVE-2021-20028
** UNSUPPORTED WHEN ASSIGNED ** Improper neutralization of a SQL Command leading to SQL Injection vulnerability impacting end-of-life Secure Remote Access (SRA) products, specifically the SRA appliances running all 8.x firmware and 9.0.0.9-26sv or earlier.
https://nvd.nist.gov/vuln/detail/CVE-2021-20028
7. CVE-2023-20598
N/A
https://nvd.nist.gov/vuln/detail/CVE-2023-20598
8. CVE-2021-21972
The vSphere Client (HTML5) contains a remote code execution vulnerability in a vCenter Server plugin. A malicious actor with network access to port 443 may exploit this issue to execute commands with unrestricted privileges on the underlying operating system that hosts vCenter Server. This affects VMware vCenter Server (7.x before 7.0 U1c, 6.7 before 6.7 U3l and 6.5 before 6.5 U3n) and VMware Cloud Foundation (4.x before 4.2 and 3.x before 3.10.1.2).
https://nvd.nist.gov/vuln/detail/CVE-2021-21972
9. CVE-2020-1472
The vSphere Client (HTML5) contains a remote code execution vulnerability in a vCenter Server plugin. A malicious actor with network access to port 443 may exploit this issue to execute commands with unrestricted privileges on the underlying operating system that hosts vCenter Server. This affects VMware vCenter Server (7.x before 7.0 U1c, 6.7 before 6.7 U3l and 6.5 before 6.5 U3n) and VMware Cloud Foundation (4.x before 4.2 and 3.x before 3.10.1.2).
https://nvd.nist.gov/vuln/detail/CVE-2020-1472
10. CVE-2023-35841
N/A
https://nvd.nist.gov/vuln/detail/CVE-2023-35841
CVE-2023-47246
CVSS: TBD
Research by Microsoft Threat Intelligence has identified a vulnerability in SysAid IT On-Premise software, documented as CVE-2023-47246. The vulnerability allows a threat actor to leverage path traversal in order to execute their own code within the target system.
It has been identified that the threat actor Lace Tempest has exploited the vulnerability by uploading a WAR archive containing a WebShell and other payloads into the webroot of the SysAid Tomcat web service. The full directory path was:
C:\Program Files\SysAidServer\tomcat\webapps\usersfiles\
The deployed WebShell granted the threat actor unauthorised access and control. Once established, they utilised PowerShell scripts to run a malware loader (with filename user.exe). This was in turn used to deploy the GraceWire Trojan, which was injected into one of the following running processes:
Once GraceWire was deployed, a second PowerShell script was executed to erase evidence of the threat actor’s presence from the disk and associated web logs.
Lace Tempest has previously been observed utilising the MOVEit vulnerability in June 2023, and deploying Cl0p ransomware.
Given the severity of the vulnerability, it is recommended that steps are taken immediately to deploy patches issued by SysAid. Vulnerable users of the software should also review systems for evidence of prior exploitation. Further details can be found on the SysAid blog here.
SOS Intelligence is currently tracking 163 distinct ransomware groups. Data collection covers 299 relays and mirrors, 93 of which are currently online.
In the reporting period, SOS Intelligence has identified 337 instances of publicised ransomware attacks. These have been identified through the publication of victim details and data on ransomware blog sites accessible via Tor. Our analysis is presented below:
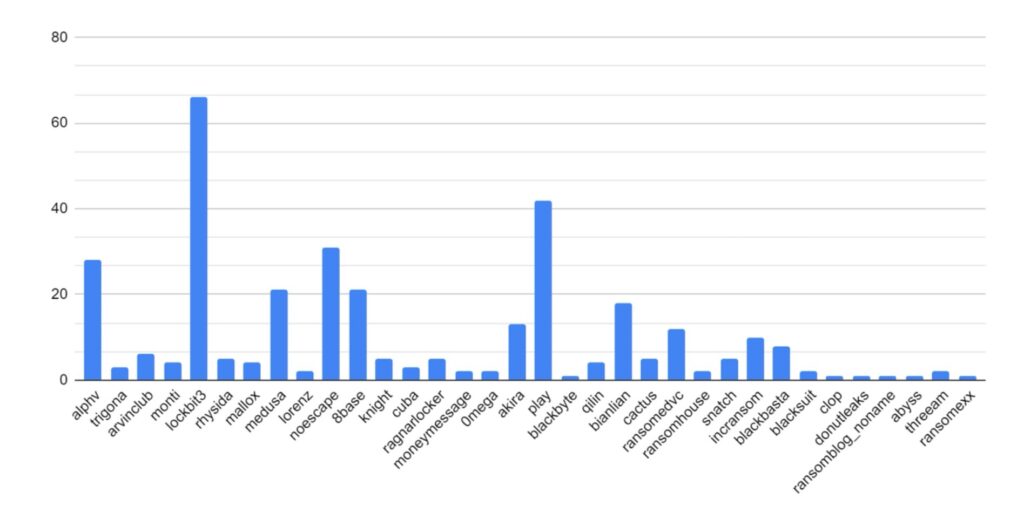
Our first graph shows attacks organised by strain. The most prominent threat groups have been AlphV/BlackCat, Play, and LockBit3. All three provide operate a Ransomware-as-a-Service (RaaS) business model, which would increase the number of threat actors using them, so it is no surprise to see these variants appearing responsible for more attacks.
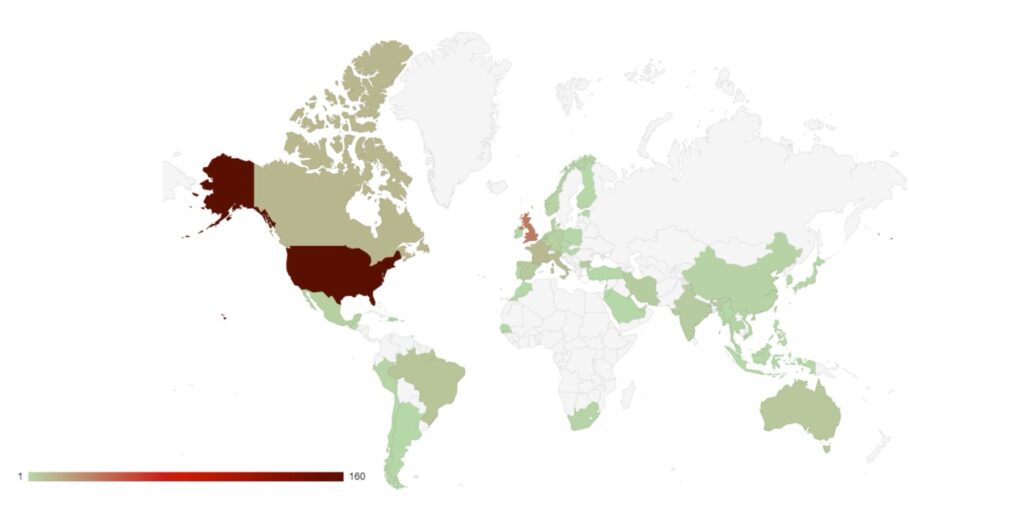
Secondly, we have looked at the spread of victims by country of origin. The USA remains the target of choice for many ransomware groups and threat actors, owing to the value of its economy and the likelihood of victims to pay ransoms.
A significant number of victims have been identified in Bulgaria, all of whom were targeted by the RansomedVC strain. RansomedVC does operate a RaaS business model, so it is hypothesised that this has been a single threat actor specifically targeting Bulgarian retail businesses.
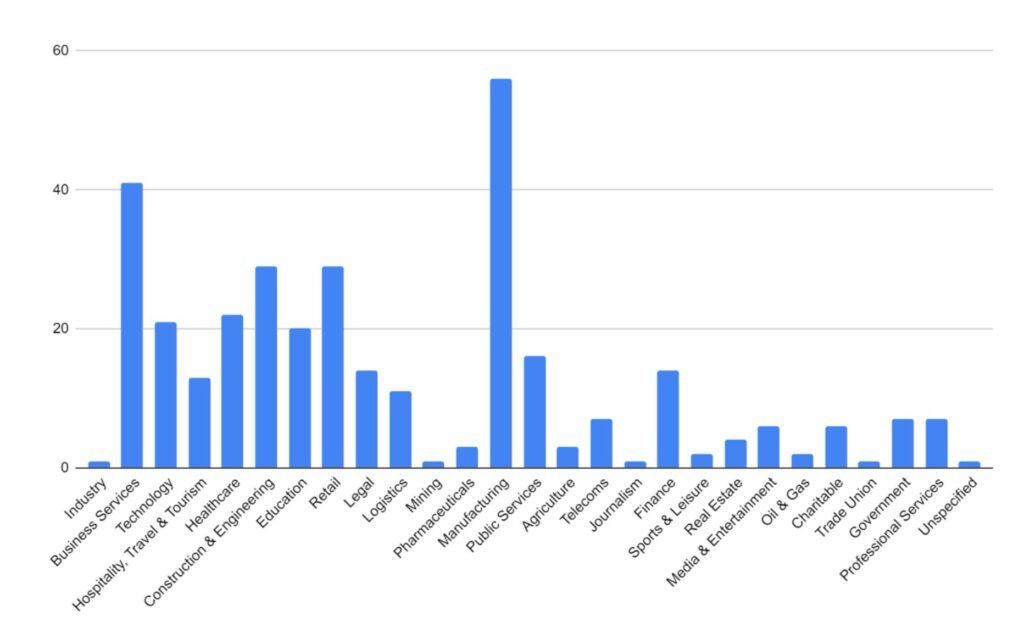
Finally, we have looked at the targeted industries. Business Services, Manufacturing and Retail sectors have experienced significantly more targeting. This is likely due to their reliance on technology to undertake their business functions: a company more reliant on technology is more likely to pay if their services and networks are disrupted.
This weekly blog post is from via our unique intelligence collection pipelines. We are your eyes and ears online, including the Dark Web.
There are thousands of vulnerability discussions each week. SOS Intelligence gathers a list of the most discussed Common Vulnerabilities and Exposures (CVE) online for the previous week.
We make every effort to ensure the accuracy of the data presented. As this is an automated process some errors may creep in.
If you are feeling generous please do make us aware of anything you spot, feel free to follow us on Twitter @sosintel and DM us. Thank you!
1. CVE-2023-20198
A vulnerability in the web UI feature of Cisco IOS XE Software could allow an authenticated, remote attacker to inject commands with the privileges of root.
This vulnerability is due to insufficient input validation. An attacker could exploit this vulnerability by sending crafted input to the web UI. A successful exploit could allow the attacker to inject commands to the underlying operating system with root privileges.
https://nvd.nist.gov/vuln/detail/CVE-2023-20198
2. CVE-2023-20273
A vulnerability in the web UI feature of Cisco IOS XE Software could allow an authenticated, remote attacker to inject commands with the privileges of root.
This vulnerability is due to insufficient input validation. An attacker could exploit this vulnerability by sending crafted input to the web UI. A successful exploit could allow the attacker to inject commands to the underlying operating system with root privileges.
https://nvd.nist.gov/vuln/detail/CVE-2023-20273
3. CVE-2023-42846
This issue was addressed by removing the vulnerable code. This issue is fixed in watchOS 10.1, iOS 16.7.2 and iPadOS 16.7.2, tvOS 17.1, iOS 17.1 and iPadOS 17.1. A device may be passively tracked by its Wi-Fi MAC address.
https://nvd.nist.gov/vuln/detail/CVE-2023-42846
4. CVE-2021-21972
An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC), aka ‘Netlogon Elevation of Privilege Vulnerability’.
https://nvd.nist.gov/vuln/detail/CVE-2021-21972
5. CVE-2023-4966
Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server.
https://nvd.nist.gov/vuln/detail/CVE-2023-4966
6. CVE-2020-1472
An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC), aka ‘Netlogon Elevation of Privilege Vulnerability’.
https://nvd.nist.gov/vuln/detail/CVE-2020-1472
7. CVE-2023-46747
The HTTP/2 protocol allows a denial of service (server resource consumption) because request cancellation can reset many streams quickly, as exploited in the wild in August through October 2023.
https://nvd.nist.gov/vuln/detail/CVE-2023-46747
8. CVE-2021-34473
Microsoft Exchange Server Remote Code Execution Vulnerability This CVE ID is unique from CVE-2021-31196, CVE-2021-31206.
https://nvd.nist.gov/vuln/detail/CVE-2021-34473
9. CVE-2023-36596
SPNEGO Extended Negotiation (NEGOEX) Security Mechanism Remote Code Execution Vulnerability
https://nvd.nist.gov/vuln/detail/CVE-2023-36596
10. CVE-2017-0143
The SMBv1 server in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows remote attackers to execute arbitrary code via crafted packets, aka “Windows SMB Remote Code Execution Vulnerability.” This vulnerability is different from those described in CVE-2017-0144, CVE-2017-0145, CVE-2017-0146, and CVE-2017-0148.
https://nvd.nist.gov/vuln/detail/CVE-2017-0143
This weekly blog post is from via our unique intelligence collection pipelines. We are your eyes and ears online, including the Dark Web.
There are thousands of vulnerability discussions each week. SOS Intelligence gathers a list of the most discussed Common Vulnerabilities and Exposures (CVE) online for the previous week.
We make every effort to ensure the accuracy of the data presented. As this is an automated process some errors may creep in.
If you are feeling generous please do make us aware of anything you spot, feel free to follow us on Twitter @sosintel and DM us. Thank you!
1. CVE-2023-20198
A vulnerability in the web UI feature of Cisco IOS XE Software could allow an authenticated, remote attacker to inject commands with the privileges of root.
This vulnerability is due to insufficient input validation. An attacker could exploit this vulnerability by sending crafted input to the web UI. A successful exploit could allow the attacker to inject commands to the underlying operating system with root privileges.
https://nvd.nist.gov/vuln/detail/CVE-2023-20198
2. CVE-2020-1472
An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC), aka ‘Netlogon Elevation of Privilege Vulnerability’.
https://nvd.nist.gov/vuln/detail/CVE-2020-1472
3. CVE-2021-21972
An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC), aka ‘Netlogon Elevation of Privilege Vulnerability’.
https://nvd.nist.gov/vuln/detail/CVE-2021-21972
4. CVE-2023-20273
A vulnerability in the web UI feature of Cisco IOS XE Software could allow an authenticated, remote attacker to inject commands with the privileges of root.
This vulnerability is due to insufficient input validation. An attacker could exploit this vulnerability by sending crafted input to the web UI. A successful exploit could allow the attacker to inject commands to the underlying operating system with root privileges.
https://nvd.nist.gov/vuln/detail/CVE-2023-20273
5. CVE-2023-4863
Heap buffer overflow in libwebp in Google Chrome prior to 116.0.5845.187 and libwebp 1.3.2 allowed a remote attacker to perform an out of bounds memory write via a crafted HTML page. (Chromium security severity: Critical)
https://nvd.nist.gov/vuln/detail/CVE-2023-4863
6. CVE-2023-4966
The HTTP/2 protocol allows a denial of service (server resource consumption) because request cancellation can reset many streams quickly, as exploited in the wild in August through October 2023.
https://nvd.nist.gov/vuln/detail/CVE-2023-4966
7. CVE-2021-1435
A vulnerability in the web UI feature of Cisco IOS XE Software could allow an authenticated, remote attacker to inject commands with the privileges of root.
This vulnerability is due to insufficient input validation. An attacker could exploit this vulnerability by sending crafted input to the web UI. A successful exploit could allow the attacker to inject commands to the underlying operating system with root privileges.
https://nvd.nist.gov/vuln/detail/CVE-2021-1435
8. CVE-2023-44487
The HTTP/2 protocol allows a denial of service (server resource consumption) because request cancellation can reset many streams quickly, as exploited in the wild in August through October 2023.
https://nvd.nist.gov/vuln/detail/CVE-2023-44487
9. CVE-2023-5631
Roundcube before 1.4.15, 1.5.x before 1.5.5, and 1.6.x before 1.6.4 allows stored XSS via an HTML e-mail message with a crafted SVG document because of program/lib/Roundcube/rcube_washtml.php behavior. This could allow a remote attacker
to load arbitrary JavaScript code.
https://nvd.nist.gov/vuln/detail/CVE-2023-5631
10. CVE-2023-20073
The HTTP/2 protocol allows a denial of service (server resource consumption) because request cancellation can reset many streams quickly, as exploited in the wild in August through October 2023.
https://nvd.nist.gov/vuln/detail/CVE-2023-20073
This weekly blog post is from via our unique intelligence collection pipelines. We are your eyes and ears online, including the Dark Web.
There are thousands of vulnerability discussions each week. SOS Intelligence gathers a list of the most discussed Common Vulnerabilities and Exposures (CVE) online for the previous week.
We make every effort to ensure the accuracy of the data presented. As this is an automated process some errors may creep in.
If you are feeling generous please do make us aware of anything you spot, feel free to follow us on Twitter @sosintel and DM us. Thank you!
1. CVE-2023-2315
Path Traversal in OpenCart versions 4.0.0.0 to 4.0.2.2 allows an authenticated user with access/modify privilege on the Log component to empty out arbitrary files on the server
https://nvd.nist.gov/vuln/detail/CVE-2023-2315
2. CVE-2023-5178
N/A
https://nvd.nist.gov/vuln/detail/CVE-2023-5178
3. CVE-2023-44487
A vulnerability in the web-based management interface of Cisco RV340, RV340W, RV345, and RV345P Dual WAN Gigabit VPN Routers could allow an unauthenticated, remote attacker to upload arbitrary files to an affected device. This vulnerability is due to insufficient authorization enforcement mechanisms in the context of file uploads. An attacker could exploit this vulnerability by sending a crafted HTTP request to an affected device. A successful exploit could allow the attacker to upload arbitrary files to the affected device.
https://nvd.nist.gov/vuln/detail/CVE-2023-44487
4. CVE-2023-4863
A vulnerability in the web-based management interface of Cisco RV340, RV340W, RV345, and RV345P Dual WAN Gigabit VPN Routers could allow an unauthenticated, remote attacker to upload arbitrary files to an affected device. This vulnerability is due to insufficient authorization enforcement mechanisms in the context of file uploads. An attacker could exploit this vulnerability by sending a crafted HTTP request to an affected device. A successful exploit could allow the attacker to upload arbitrary files to the affected device.
https://nvd.nist.gov/vuln/detail/CVE-2023-4863
5. CVE-2023-20198
Cisco is aware of active exploitation of a previously unknown vulnerability in the web UI feature of Cisco IOS XE Software when exposed to the internet or to untrusted networks. This vulnerability allows a remote, unauthenticated attacker to create an account on an affected system with privilege level 15 access. The attacker can then use that account to gain control of the affected system.
For steps to close the attack vector for this vulnerability, see the Recommendations section of this advisory
Cisco will provide updates on the status of this investigation and when a software patch is available.
https://nvd.nist.gov/vuln/detail/CVE-2023-20198
6. CVE-2022-30190
Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability.
https://nvd.nist.gov/vuln/detail/CVE-2022-30190
7. CVE-2022-40684
An authentication bypass using an alternate path or channel [CWE-288] in Fortinet FortiOS version 7.2.0 through 7.2.1 and 7.0.0 through 7.0.6, FortiProxy version 7.2.0 and version 7.0.0 through 7.0.6 and FortiSwitchManager version 7.2.0 and 7.0.0 allows an unauthenticated atttacker to perform operations on the administrative interface via specially crafted HTTP or HTTPS requests.
https://nvd.nist.gov/vuln/detail/CVE-2022-40684
8. CVE-2009-0658
Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability.
https://nvd.nist.gov/vuln/detail/CVE-2009-0658
9. CVE-2023-3519
Unauthenticated remote code execution
https://nvd.nist.gov/vuln/detail/CVE-2023-3519
10. CVE-2021-34473
Microsoft Exchange Server Remote Code Execution Vulnerability This CVE ID is unique from CVE-2021-31196, CVE-2021-31206.
https://nvd.nist.gov/vuln/detail/CVE-2021-34473
CVSS: 9.4
Last week, Citrix released a patch for CVE-2023-4966. This vulnerability allows threat actors to hijack existing, authenticated sessions and bypass multi-factor authentication. As a result, they could fully control NetScaler environments, and therefore manage and control application delivery.
The vulnerability impacts the following versions of Citrix NetScaler:
Cybersecurity firm Mandiant has been tracking exploitation of the vulnerability and has seen evidence of use since August 2023 by an as-yet-unknown threat actor. This threat actor appears most concerned with cyberespionage, with targets including professional services, technology and government organisations. Over time, it is anticipated that further threat actors will begin exploiting this vulnerability across wider sectors for financial gain.
Despite the patch being issued, it is anticipated that exploitation of this vulnerability will increase. This is down to a slow uptake of patching undertaken by users of Citrix NetScaler. For example, we previously reported on CVE-2023-3519 which was patched in July 2023 after being exploited as early as June 2023. Research by the Shadowserver Foundation indicates at least 1,300 NetScaler instances are still vulnerable to this exploit.
Citrix recommends updating and patching all instances of NetScaler to the most recently available versions in order to limit the impact of the vulnerability. Further details can be found here.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |


Recent Comments