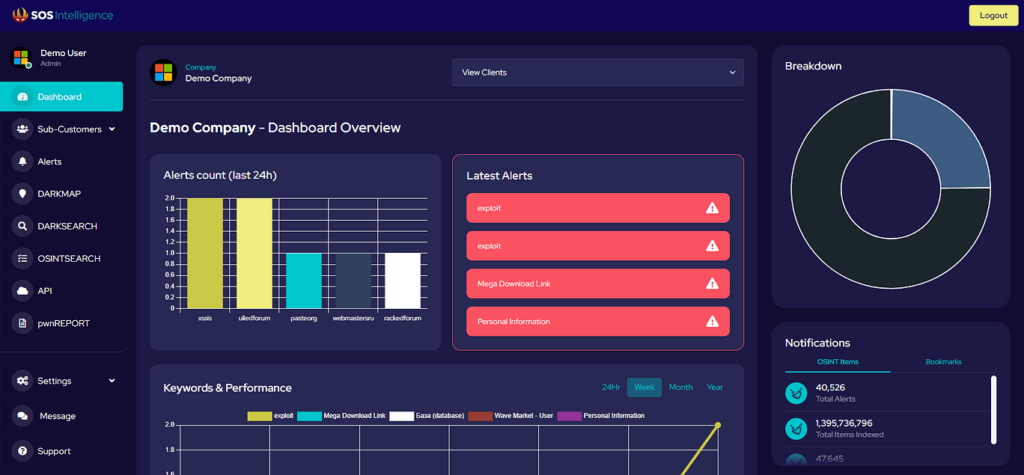
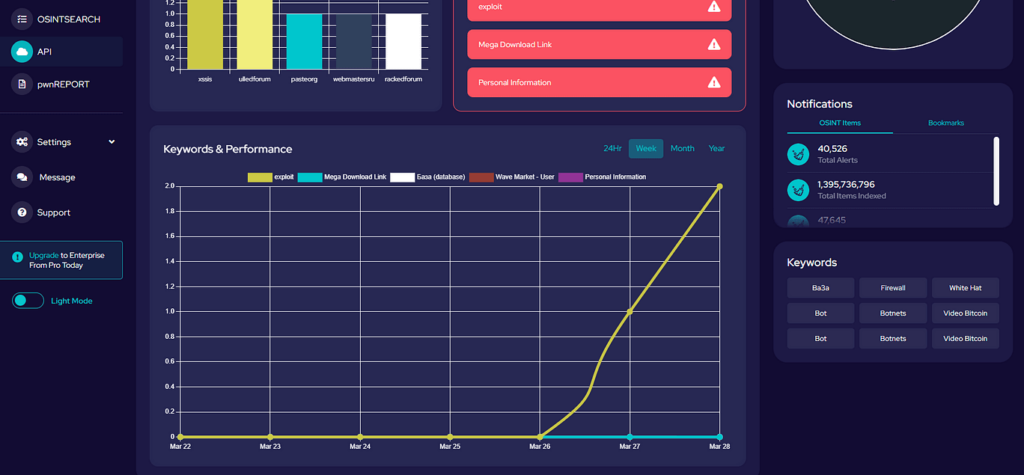
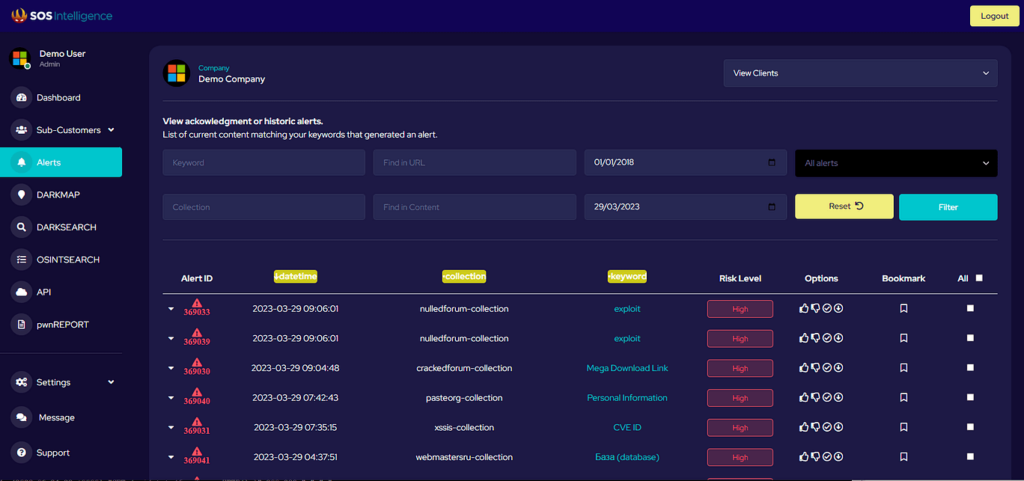
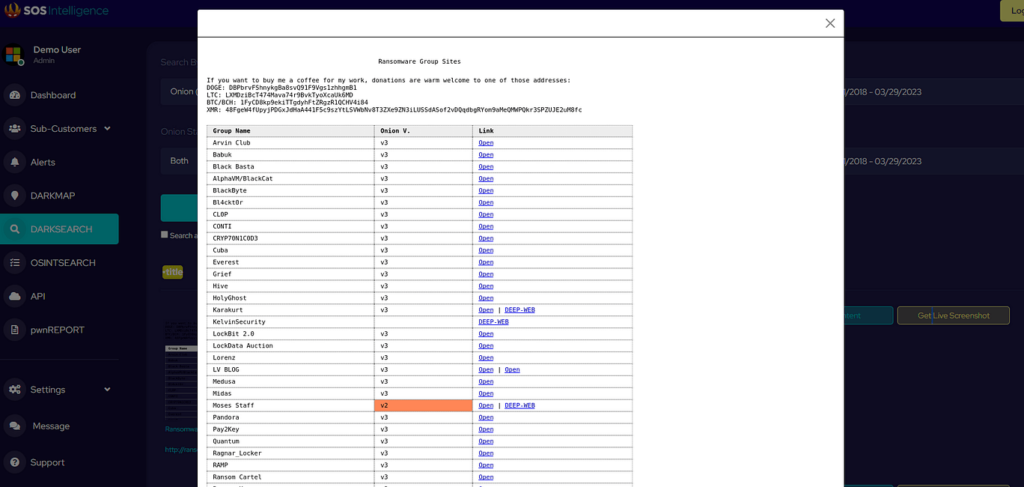
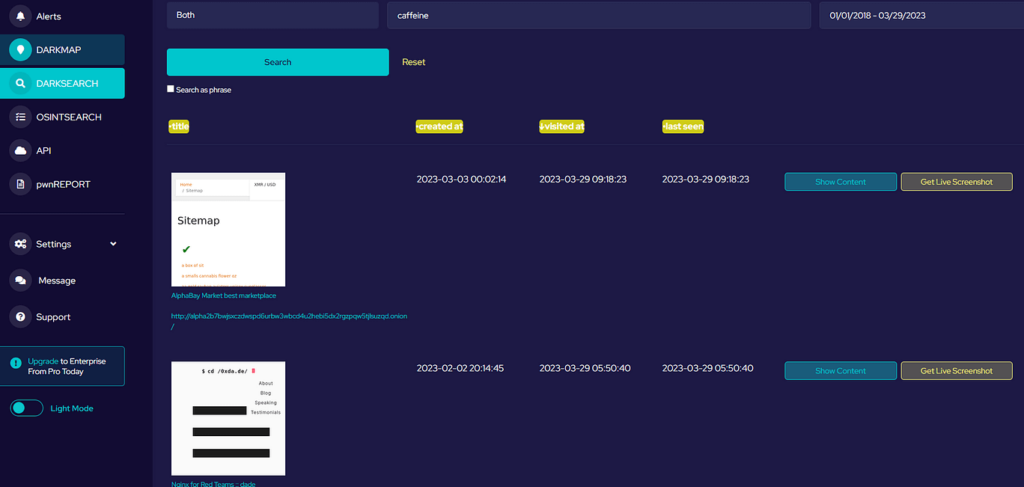
This weekly blog post is from via our unique intelligence collection pipelines. We are your eyes and ears online, including the Dark Web.
There are thousands of vulnerability discussions each week. SOS Intelligence gathers a list of the most discussed Common Vulnerabilities and Exposures (CVE) online for the previous week.
We make every effort to ensure the accuracy of the data presented. As this is an automated process some errors may creep in.
If you are feeling generous please do make us aware of anything you spot, feel free to follow us on Twitter @sosintel and DM us. Thank you!
1. CVE-2021-4034
A local privilege escalation vulnerability was found on polkit’s pkexec utility. The pkexec application is a setuid tool designed to allow unprivileged users to run commands as privileged users according predefined policies. The current version of pkexec doesn’t handle the calling parameters count correctly and ends trying to execute environment variables as commands. An attacker can leverage this by crafting environment variables in such a way it’ll induce pkexec to execute arbitrary code. When successfully executed the attack can cause a local privilege escalation given unprivileged users administrative rights on the target machine.
https://nvd.nist.gov/vuln/detail/CVE-2021-4034
2. CVE-2023-27532
Vulnerability in Veeam Backup & Replication component allows encrypted credentials stored in the configuration database to be obtained. This may lead to gaining access to the backup infrastructure hosts.
https://nvd.nist.gov/vuln/detail/CVE-2023-27532
3. CVE-2016-0167
The kernel-mode driver in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, and Windows 10 Gold and 1511 allows local users to gain privileges via a crafted application, aka “Win32k Elevation of Privilege Vulnerability,” a different vulnerability than CVE-2016-0143 and CVE-2016-0165.
https://nvd.nist.gov/vuln/detail/CVE-2016-0167
4. CVE-2022-40684
An authentication bypass using an alternate path or channel [CWE-288] in Fortinet FortiOS version 7.2.0 through 7.2.1 and 7.0.0 through 7.0.6, FortiProxy version 7.2.0 and version 7.0.0 through 7.0.6 and FortiSwitchManager version 7.2.0 and 7.0.0 allows an unauthenticated atttacker to perform operations on the administrative interface via specially crafted HTTP or HTTPS requests.
https://nvd.nist.gov/vuln/detail/CVE-2022-40684
5. CVE-2016-4117
The kernel-mode driver in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, and Windows 10 Gold and 1511 allows local users to gain privileges via a crafted application, aka “Win32k Elevation of Privilege Vulnerability,” a different vulnerability than CVE-2016-0143 and CVE-2016-0165.
https://nvd.nist.gov/vuln/detail/CVE-2016-4117
6. CVE-2018-17144
Bitcoin Core 0.14.x before 0.14.3, 0.15.x before 0.15.2, and 0.16.x before 0.16.3 and Bitcoin Knots 0.14.x through 0.16.x before 0.16.3 allow a remote denial of service (application crash) exploitable by miners via duplicate input. An attacker can make bitcoind or Bitcoin-Qt crash.
https://nvd.nist.gov/vuln/detail/CVE-2018-17144
7. CVE-2012-2459
Unspecified vulnerability in bitcoind and Bitcoin-Qt before 0.4.6, 0.5.x before 0.5.5, 0.6.0.x before 0.6.0.7, and 0.6.x before 0.6.2 allows remote attackers to cause a denial of service (block-processing outage and incorrect block count) via unknown behavior on a Bitcoin network.
https://nvd.nist.gov/vuln/detail/CVE-2012-2459
8. CVE-2023-24033
The Samsung Exynos Modem 5123, Exynos Modem 5300, Exynos 980, Exynos 1080, and Exynos Auto T512 baseband modem chipsets do not properly check format types specified by the Session Description Protocol (SDP) module, which can lead to a denial of service.
https://nvd.nist.gov/vuln/detail/CVE-2023-24033
9. CVE-2017-0261
The kernel-mode driver in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, and Windows 10 Gold and 1511 allows local users to gain privileges via a crafted application, aka “Win32k Elevation of Privilege Vulnerability,” a different vulnerability than CVE-2016-0143 and CVE-2016-0165.
https://nvd.nist.gov/vuln/detail/CVE-2017-0261
10. CVE-2017-0199
The kernel-mode driver in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, and Windows 10 Gold and 1511 allows local users to gain privileges via a crafted application, aka “Win32k Elevation of Privilege Vulnerability,” a different vulnerability than CVE-2016-0143 and CVE-2016-0165.
https://nvd.nist.gov/vuln/detail/CVE-2017-0199





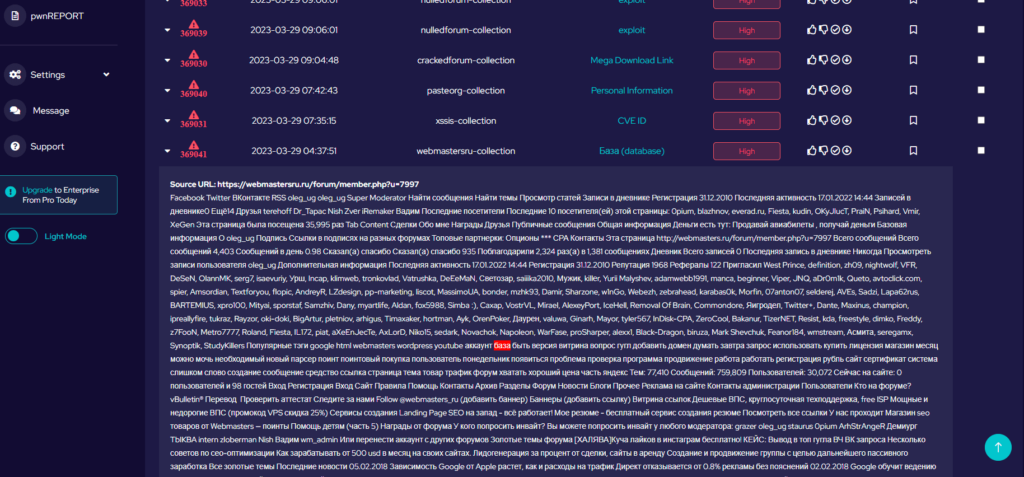
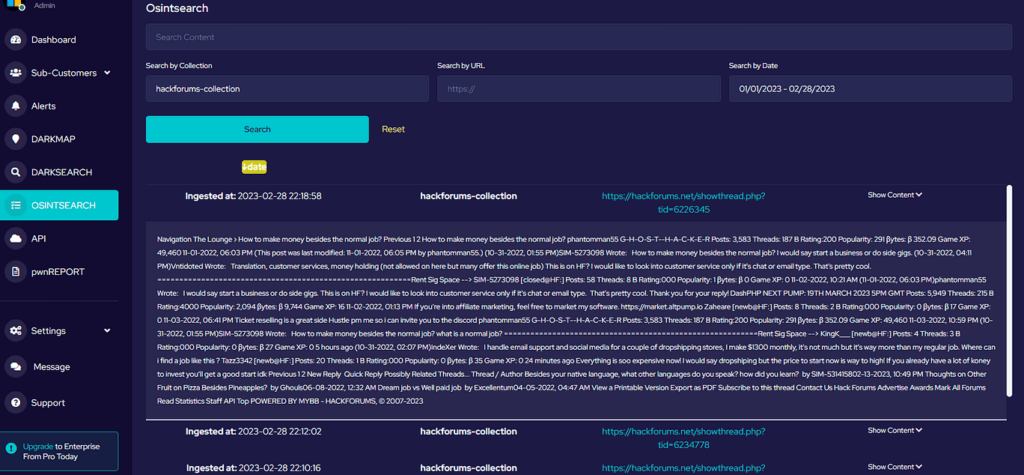
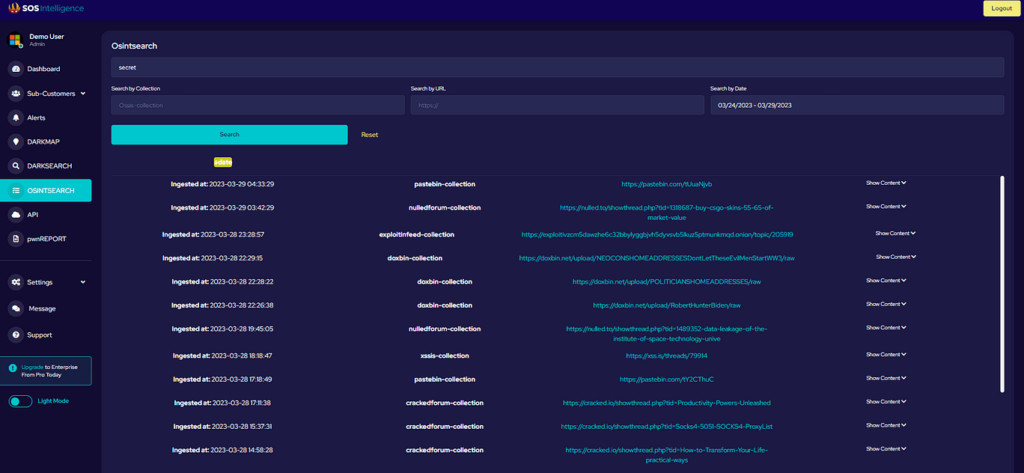
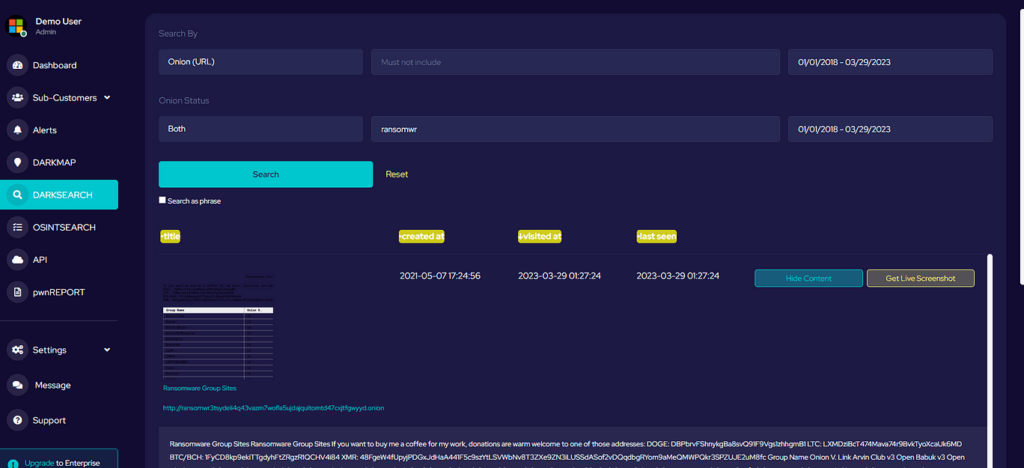

Recent Comments