SOS Intelligence is currently tracking 163 distinct ransomware groups. Data collection covers 299 relays and mirrors, 93 of which are currently online.
In the reporting period, SOS Intelligence has identified 337 instances of publicised ransomware attacks. These have been identified through the publication of victim details and data on ransomware blog sites accessible via Tor. Our analysis is presented below:
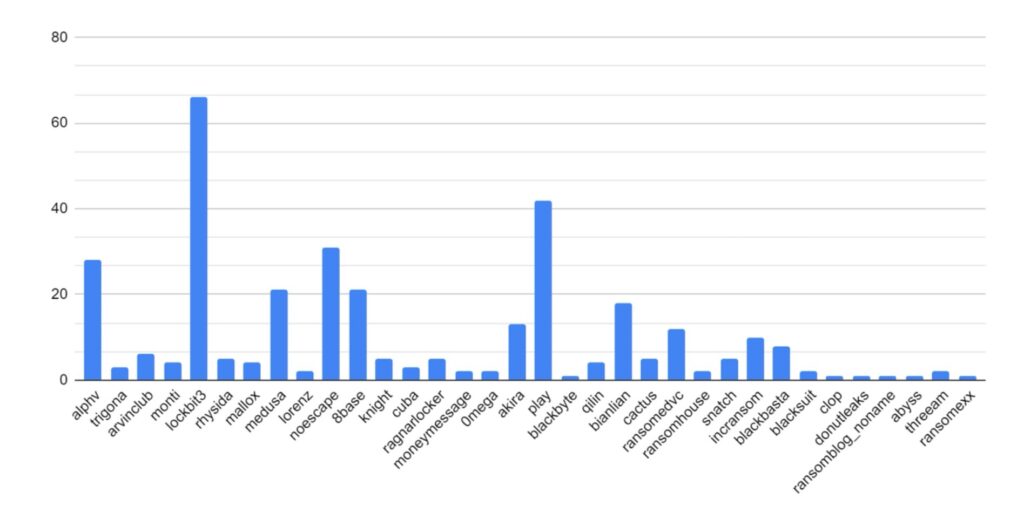
Our first graph shows attacks organised by strain. The most prominent threat groups have been AlphV/BlackCat, Play, and LockBit3. All three provide operate a Ransomware-as-a-Service (RaaS) business model, which would increase the number of threat actors using them, so it is no surprise to see these variants appearing responsible for more attacks.
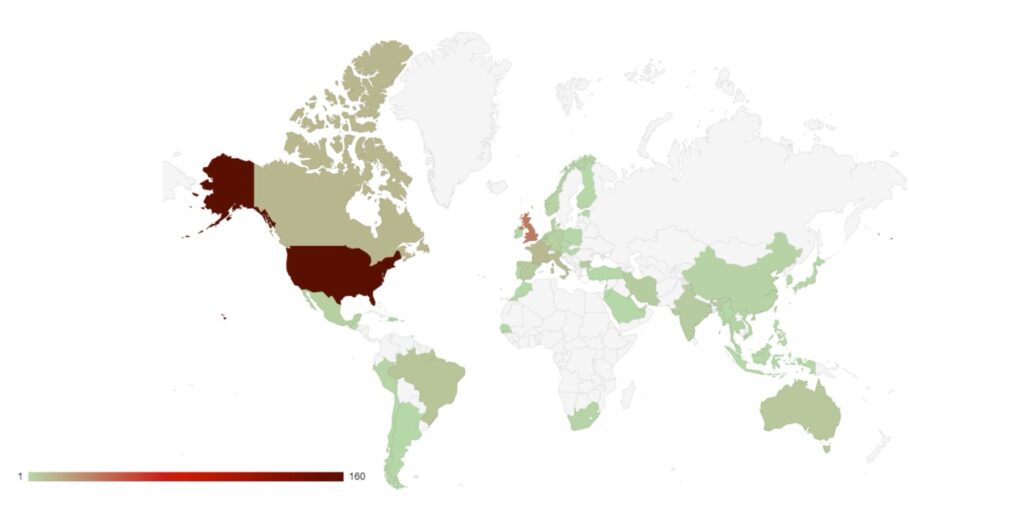
Secondly, we have looked at the spread of victims by country of origin. The USA remains the target of choice for many ransomware groups and threat actors, owing to the value of its economy and the likelihood of victims to pay ransoms.
A significant number of victims have been identified in Bulgaria, all of whom were targeted by the RansomedVC strain. RansomedVC does operate a RaaS business model, so it is hypothesised that this has been a single threat actor specifically targeting Bulgarian retail businesses.
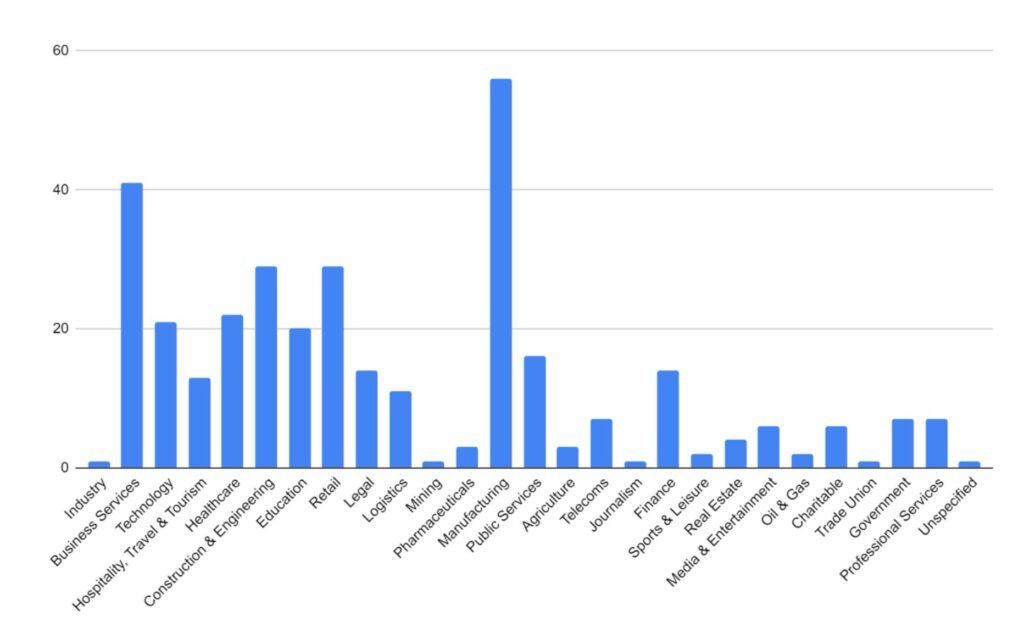
Finally, we have looked at the targeted industries. Business Services, Manufacturing and Retail sectors have experienced significantly more targeting. This is likely due to their reliance on technology to undertake their business functions: a company more reliant on technology is more likely to pay if their services and networks are disrupted.







Recent Comments