This weekly blog post is from via our unique intelligence collection pipelines. We are your eyes and ears online, including the Dark Web.
There are thousands of vulnerability discussions each week. SOS Intelligence gathers a list of the most discussed Common Vulnerabilities and Exposures (CVE) online for the previous week.
We make every effort to ensure the accuracy of the data presented. As this is an automated process some errors may creep in.
If you are feeling generous please do make us aware of anything you spot, feel free to follow us on Twitter @sosintel and DM us. Thank you!
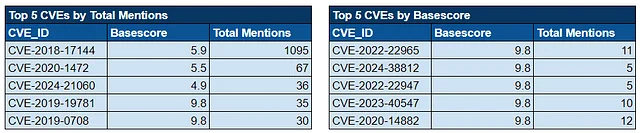
1. CVE-2018-17144
Bitcoin Core 0.14.x before 0.14.3, 0.15.x before 0.15.2, and 0.16.x before 0.16.3 and Bitcoin Knots 0.14.x through 0.16.x before 0.16.3 allow a remote denial of service (application crash) exploitable by miners via duplicate input. An attacker can make bitcoind or Bitcoin-Qt crash.
https://nvd.nist.gov/vuln/detail/CVE-2018-17144
2. CVE-2022-22965
A Spring MVC or Spring WebFlux application running on JDK 9+ may be vulnerable to remote code execution (RCE) via data binding. The specific exploit requires the application to run on Tomcat as a WAR deployment. If the application is deployed as a Spring Boot executable jar, i.e. the default, it is not vulnerable to the exploit. However, the nature of the vulnerability is more general, and there may be other ways to exploit it.
https://nvd.nist.gov/vuln/detail/CVE-2022-22965
3. CVE-2018-2628
Vulnerability in the Oracle WebLogic Server component of Oracle Fusion Middleware (subcomponent: WLS Core Components). Supported versions that are affected are 10.3.6.0, 12.1.3.0, 12.2.1.2 and 12.2.1.3. Easily exploitable vulnerability allows unauthenticated attacker with network access via T3 to compromise Oracle WebLogic Server. Successful attacks of this vulnerability can result in takeover of Oracle WebLogic Server. CVSS 3.0 Base Score 9.8 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
https://nvd.nist.gov/vuln/detail/CVE-2018-2628
4. CVE-2021-42278
Active Directory Domain Services Elevation of Privilege Vulnerability
https://nvd.nist.gov/vuln/detail/CVE-2021-42278
5. CVE-2024-23113
A use of externally-controlled format string in Fortinet FortiOS versions 7.4.0 through 7.4.2, 7.2.0 through 7.2.6, 7.0.0 through 7.0.13, FortiProxy versions 7.4.0 through 7.4.2, 7.2.0 through 7.2.8, 7.0.0 through 7.0.14, FortiPAM versions 1.2.0, 1.1.0 through 1.1.2, 1.0.0 through 1.0.3, FortiSwitchManager versions 7.2.0 through 7.2.3, 7.0.0 through 7.0.3 allows attacker to execute unauthorized code or commands via specially crafted packets.
https://nvd.nist.gov/vuln/detail/CVE-2024-23113
6. CVE-2024-38125
Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability
https://nvd.nist.gov/vuln/detail/CVE-2024-38125
7. CVE-2022-22947
In spring cloud gateway versions prior to 3.1.1+ and 3.0.7+ , applications are vulnerable to a code injection attack when the Gateway Actuator endpoint is enabled, exposed and unsecured. A remote attacker could make a maliciously crafted request that could allow arbitrary remote execution on the remote host.
https://nvd.nist.gov/vuln/detail/CVE-2022-22947
8. CVE-2024-38199
Windows Line Printer Daemon (LPD) Service Remote Code Execution Vulnerability
https://nvd.nist.gov/vuln/detail/CVE-2024-38199
9. CVE-2024-38140
Windows Reliable Multicast Transport Driver (RMCAST) Remote Code Execution Vulnerability
https://nvd.nist.gov/vuln/detail/CVE-2024-38140
10. CVE-2024-7262
Improper path validation in promecefpluginhost.exe in Kingsoft WPS Office version ranging from 12.2.0.13110 to 12.2.0.16412 (exclusive) on Windows allows an attacker to load an arbitrary Windows library.
The vulnerability was found weaponized as a single-click exploit in the form of a deceptive spreadsheet document
https://nvd.nist.gov/vuln/detail/CVE-2024-7262






















Recent Comments