The “dark web” has become something of a buzzword in recent years, often portrayed as the hidden underworld of the internet where cybercriminals operate in complete anonymity. For many, it conjures images of secret marketplaces, illicit data dumps, and hard-to-trace communications — all out of reach from the average internet user.
Because of this perception, it is a common misconception that all threat actor activity takes place exclusively on the dark web. While it certainly plays a role in enabling criminal operations, the truth is far more complex. Today’s threat actors are increasingly making use of platforms that are readily available, user-friendly, and in many cases, completely legal.
Much of their coordination, recruitment, and even data leakage now takes place in plain sight — across encrypted messaging apps, public forums, and mainstream social media platforms. Understanding where these actors truly operate is critical for any organisation looking to stay ahead of the threat landscape.

The Evolving Landscape of Threat Actor Platforms
The way threat actors communicate and coordinate has shifted significantly in recent years. Once heavily reliant on hidden services accessed through the Tor network, many cybercriminals are now embracing more accessible, mainstream platforms to conduct their activities.
This change has been driven by several key factors. One of the most prominent is the increased pressure from law enforcement. High-profile takedowns of dark web marketplaces such as AlphaBay and Hydra have disrupted long-standing criminal ecosystems, forcing actors to reconsider where and how they operate.
At the same time, modern platforms offer features that make them attractive to malicious users. Encrypted messaging apps provide a level of privacy that rivals, and in some cases exceeds, what is available on the dark web. Public forums and chat platforms are easy to access, require minimal technical knowledge, and can reach large audiences quickly.
For cybercriminals, scale and convenience matter. Hosting content on widely used services allows them to cast a broader net, whether they’re distributing stolen data, selling malware, or recruiting new affiliates. The lines between the open internet and covert criminal spaces are increasingly blurred, making it more difficult for defenders to track activity using traditional dark web monitoring alone.
Alternative Threat Actor Channels

While the dark web still plays a role in cybercriminal operations, many threat actors now prefer more accessible and user-friendly platforms. These alternatives offer speed, scalability, and often a surprising degree of anonymity — all without the need for specialised browsers or infrastructure. Below are some of the most commonly used non-dark web channels.
Telegram
Telegram has become a go-to platform for cybercriminals. With its end-to-end encryption, support for large group chats, and the ability to create private or public channels, it offers the ideal environment for discreet coordination at scale.
Threat actors use Telegram to:
- Leak stolen data and documents
- Advertise and sell credentials or access to compromised systems
- Host scam pages or phishing kits
- Organise affiliate networks or ransomware-as-a-service (RaaS) operations
Its minimal moderation and vast global user base make it a particularly attractive choice for cybercrime groups.
Discord and Other Chat Platforms
Originally designed for online gaming communities, Discord has evolved into a full-featured communication tool with support for text, voice, and private servers. Unfortunately, these same features have also made it a popular haven for fraudsters and cybercriminals.
Threat actors use Discord to:
- Create closed communities centred around fraud, hacking tools, or data leaks
- Share resources in “plug” communities — often focused on carding, identity theft, or botnet services
- Coordinate attacks or distribute malware through seemingly innocuous links
Other platforms such as Tox, Matrix, and IRC-based services are also used, albeit with smaller user bases.
Surface Web Forums
Despite the risks of being in plain sight, many cybercrime forums continue to operate openly on the surface web. These forums are often language-specific or focused on particular sectors, such as financial fraud, social engineering, or credential stuffing.
They are typically used to:
- Trade tools, tactics, and stolen data
- Post tutorials or share exploit code
- Vet and recruit participants for more private activities
Some forums operate with limited moderation or are hosted in jurisdictions with lax enforcement, allowing them to persist despite ongoing attention from security professionals.
Social Media (Twitter/X, Facebook, etc.)
Social media platforms remain surprisingly popular for certain types of threat actor activity. On services like Twitter/X, Facebook, and even LinkedIn, cybercriminals can quickly build audiences, push propaganda, or leak stolen information to make a statement.
Common uses include:
- Publicly claiming responsibility for attacks or breaches
- Promoting data leaks to gain notoriety or apply pressure to victims
- Running influence campaigns or disinformation efforts
- Recruiting low-level actors or collaborators
While these platforms generally respond quickly to takedown requests, the speed at which content can be published and spread makes them a persistent threat vector.
Paste Sites and Temporary File Hosts
Pastebin-style sites and ephemeral file hosting services continue to be used by cybercriminals to share content without needing to manage infrastructure. These services are often exploited to distribute:
- Malware payloads
- Indicators of compromise (IOCs)
- Stolen credentials or internal documentation
Examples include Pastebin, Ghostbin, file.io, and anonfiles (when active). Their simplicity and temporary nature make them appealing for one-off drops or fast-moving campaigns.
Why the Shift Away from the Dark Web?
While the dark web once provided the primary infrastructure for cybercriminal marketplaces and forums, it has become a less attractive option for many threat actors. A combination of practical challenges and strategic advantages has led to a growing preference for mainstream and surface-level platforms.
One of the key drivers behind this shift is the increasing success of global law enforcement operations. High-profile takedowns such as AlphaBay, Hansa, and Hydra have not only dismantled major criminal marketplaces but also sown distrust within dark web communities. With undercover operations and seizures now a recurring threat, many actors perceive mainstream platforms as less risky in terms of operational security, particularly when combined with disposable accounts and encrypted messaging.
Technical reliability is another issue. Dark web services can suffer from poor uptime, slow performance, and hosting instability. These problems make it harder for threat actors to run consistent operations or maintain communication, especially when compared to the seamless experience offered by platforms like Telegram or Discord.
Accessibility also plays a major role. Mainstream platforms are far easier to use and require no special configuration or tools. Anyone with a smartphone can join a Telegram group or browse a fraud forum hosted on the surface web. This lowers the barrier to entry for newer or less technically skilled actors, fuelling growth in cybercriminal communities.
Finally, these platforms offer scale. Social media, public channels, and open forums provide instant access to large audiences, whether for pushing stolen data, coordinating campaigns, or recruiting collaborators. The potential for amplification far exceeds what is typically possible within the confines of the dark web.
For all these reasons, the dark web is no longer the sole or even primary location for cybercriminal activity. Threat actors are adapting to a broader, more dynamic digital environment, and defenders must do the same.
Implications for Threat Intelligence Teams
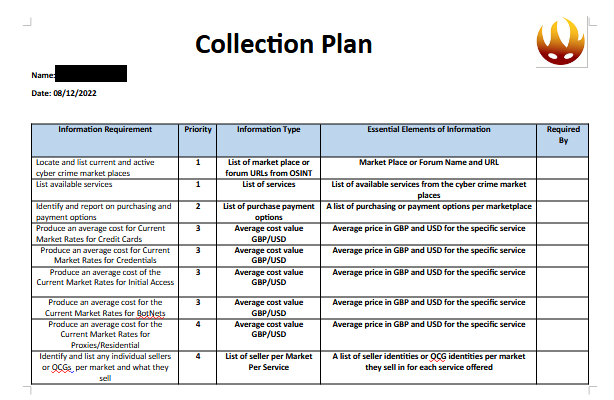
As threat actors diversify their platforms, the scope of effective cyber threat intelligence (CTI) must evolve accordingly. Relying solely on dark web monitoring is no longer sufficient. Instead, teams must broaden their visibility to include the various surface and semi-private spaces where cybercriminal activity increasingly takes place.
Monitoring closed channels such as Telegram groups, Discord servers, and niche forums has become essential. However, these spaces are often harder to access and require greater care in terms of operational security (OPSEC). Joining or observing these groups can carry significant risk if not done properly. Analysts must use hardened environments, anonymous accounts, and clear protocols to avoid detection or legal exposure.
Language skills and cultural awareness are also becoming increasingly important. Many cybercrime communities operate in non-English languages and use regional slang or coded terminology. Without this context, valuable intelligence can be missed or misinterpreted. Investing in native language analysts or translation tools can dramatically improve coverage and insight.
The scale and speed at which content is published across platforms make manual monitoring impractical. As such, automation is vital. Tools that scrape and index Telegram posts, track mentions on social media, or flag emerging IOCs can help intelligence teams respond quickly and reduce the chance of missing key developments.
Ultimately, the shift in threat actor behaviour demands a shift in defender strategy. The more fragmented and accessible the threat landscape becomes, the more agile and well-equipped CTI teams need to be in order to stay ahead.

Case Examples

LockBit’s Use of Telegram for PR and Leak Amplification (2024)
In early 2024, after suffering internal leaks and DDoS attacks against their dark web leak site, the LockBit ransomware group turned to Telegram to regain control of their narrative. The group created public Telegram channels to share statements, leak victim data, and coordinate with affiliates. This move not only ensured continuity during technical outages but also expanded their audience beyond the dark web’s limited reach.
Telegram’s encryption, ease of access, and built-in forwarding features allowed LockBit to amplify their message rapidly, including to journalists, researchers, and rival threat actors. It showcased a tactical shift: using mainstream tools as a parallel infrastructure for both influence and extortion pressure.
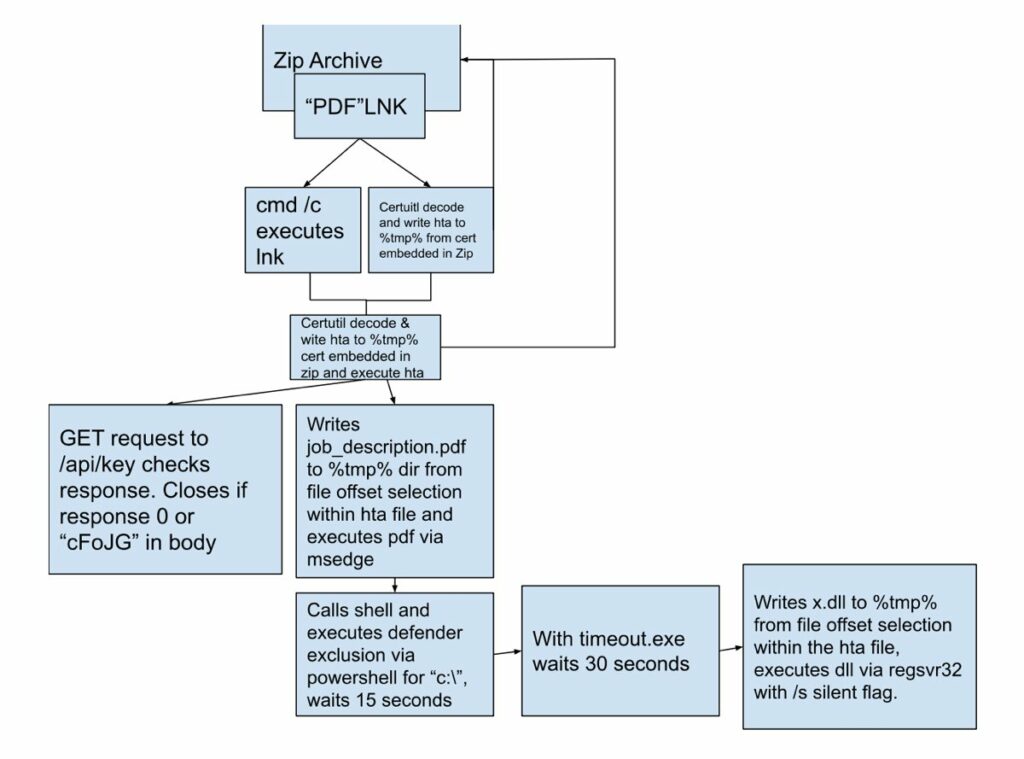
“Infinity Stealer” Malware Sold via Discord and GitHub (Mid–2023 Onwards)
Infinity Stealer, a malware strain targeting browser credentials and crypto wallets, began circulating heavily in 2023 via non-dark web platforms, notably Discord and GitHub. The malware was marketed in private Discord servers where prospective buyers were vetted and provided updates. GitHub repositories were used to host payloads, configuration templates, and instructions, often disguised as open-source tools.
This campaign highlights how cybercriminals are bypassing traditional marketplaces entirely, instead using legitimate platforms for both sales and delivery infrastructure. Discord’s private server structure and GitHub’s reputational cover enabled the operators to fly under the radar while still reaching a large pool of technically capable users.
Conclusion
The dark web remains a valuable source of cyber threat intelligence — but it is no longer the whole story. As cybercriminals adapt to a shifting digital landscape, they are increasingly leveraging open and semi-closed platforms like Telegram, Discord, and even mainstream social media to conduct and promote their activities.
For CTI teams, this evolution demands a broader approach. Effective monitoring now extends beyond Tor and onion domains to include a mix of channels, each with its own risks, nuances, and intelligence value. It also requires enhanced OPSEC, linguistic awareness, and the integration of automation tools to track activity at scale.
By recognising these trends and adapting monitoring strategies accordingly, defenders can stay better aligned with the current threat environment — one that is faster, more fragmented, and no longer confined to the shadows.





















Recent Comments